Viewing MRS Cluster Audit Logs
The Audit page records user operations on Manager. Administrators can view user operation records on Manager. For details, see Audit logs.
This section describes how to view and export audit logs on MRS Manager for post-event tracing, fault cause locating, and responsibility division of security events.
Viewing Audit Logs (MRS 3.x or Later)
- Log in to FusionInsight Manager of the MRS cluster.
For details about how to log in to FusionInsight Manager, see Accessing MRS Manager.
- Choose Audit. The Audit page displays audit information of FusionInsight Manager, including the operation type, risk level, start time, end time, user, host, service, instance, and operation result.
Table 1 Audit information Parameter
Description
Operation Type
Type of operation performed on FusionInsight Manager. The options include User_Manager, Cluster, Service, Alarm, Backup and Restoration, and Tenant.
Severity
Security level of each audit log. The options include Critical, Major, Minor, and Notice.
Started
Time when the operation starts
Completed
Time when the operation ends
User
Name of the user who performs the operation
Host
Cluster node where the operation is performed
Service
Cluster service involved in the operation
Instance
Cluster role instance involved in the operation
Operation Result
User operation result. The options include Successful, Failed, and Unknown.
Figure 1 Audit information list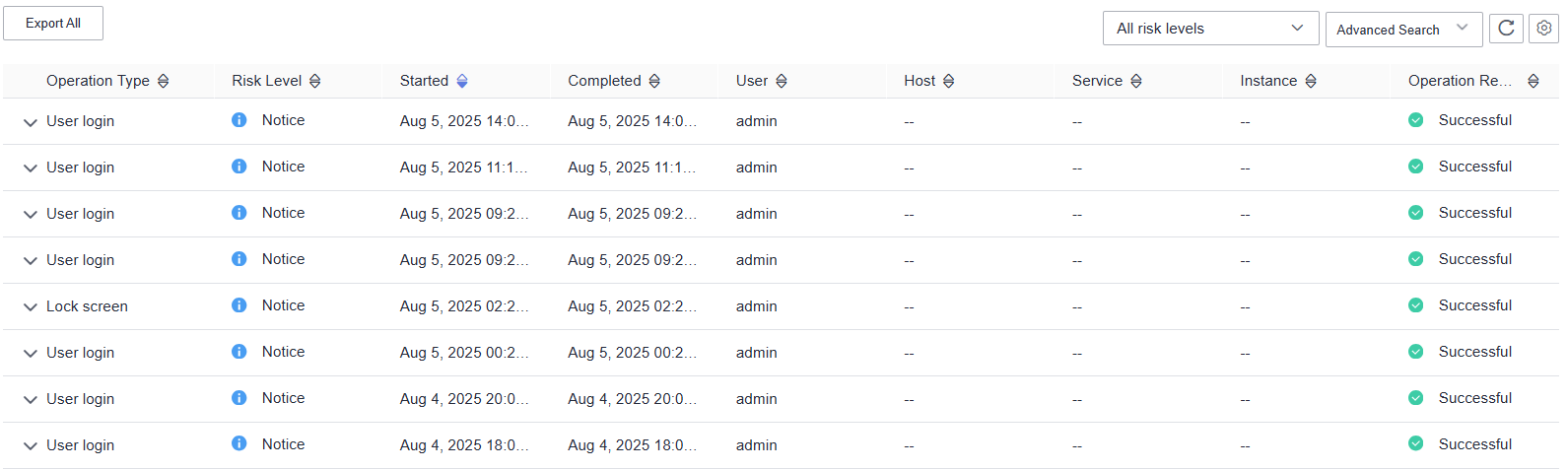
- You can select audit logs at the Critical, Major, Minor, or Notice level from the All risk levels drop-down list.
- In Advanced Search, you can set filter criteria to query audit logs.
- You can query audit logs by user management, cluster, service, and health in the Operation Type column.
- In the Service column, you can select a service to query corresponding audit logs.
You can select -- to search for audit logs using all search criteria except the service.
- You can query audit logs by operation result. The options are All, Successful, Failed, and Unknown.
- You can click
 to manually refresh the current page or click
to manually refresh the current page or click  to choose the columns to display on the page.
to choose the columns to display on the page. - Click Export All to export all audit information at a time, in TXT or CSV format.
Viewing Audit Logs (Versions Earlier Than MRS 3.x)
- Log in to FusionInsight Manager of the MRS cluster.
For details about how to log in to FusionInsight Manager, see Accessing MRS Manager.
- Click Audit to view default audit logs.
- If an audit log contains more than 256 characters, click expand button to view full audit details.
- Records are sorted in descending order by the Occurred column as the default setting. To change the sorting mode, click Operation Type, Severity, Occurred, User, Host, Service, Instance, or Operation Result.
- You can filter all alarms of the same severity, including both cleared and uncleared alarms, by Severity.
Exported audit log files contain the following columns:
Table 2 Audit log file information Parameter
Description
Sno
Number of audit logs generated by MRS Manager. The number increases by 1 each time an audit log is generated.
Operation Type
Operation type. The options are Alarm, Auditlog, Backup and Restoration, Cluster, Collect Log, Host, Service, Tenant, and User_Manager. User_Manager is available only for clusters with Kerberos authentication enabled. Each option contains varying operation types. For example, Alarm includes Export alarms, Cluster includes Start cluster, and Tenant includes Add tenant.
Severity
Security level of each audit log, including Critical, Major, Minor, and Informational.
Start Time
Time when the operation starts, which is the CET or CEST time
End Time
Time when the operation ends, which is the CET or CEST time
User IP Address
IP address used by a user to perform the operation
User
Name of the user who performs the operation
Host
Node where the operation is performed. The information is not saved if the operation does not involve a node.
Service
Service on which the operation is performed. The information is not saved if the operation does not involve a service.
Instance
Role instance on which the operation is performed. The information is not saved if the operation does not involve a role instance.
Operation Result
User operation result. The options include Successful, Failed, and Unknown.
Content
Detailed information of the operation
- Click Advanced Search. In the search area, set search criteria and click Search to view audit logs of a specified type. Click Reset to clear the search criteria.
Start Time and End Time specify the start time and end time of the time range. You can search for alarms generated within the time range.
- To export all audit log files in the log list, click Export All.
- To export an audit log file, select it in the log list and click Export.
Helpful Links
- Audit logs of MRS cluster components are classified by name and stored in the /var/log/Bigdata/audit directory on each node in the cluster. You can change the maximum number of audit log files that can be backed up by OMS. For details, see Configuring the Number of Local Backups of MRS Cluster Audit Logs.
- You can save the audit logs of Manager to other archive servers. For details, see Configuring Dumping for MRS Cluster Audit Logs.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





