Configuring Kafka Public Access
A client can use IPv4 or IPv6 addresses to access a Kafka instance over a public network.
- By IPv4: On the Kafka console, enable public access and configure EIPs for the instance.
- By IPv6: Enable IPv6 in Kafka instance creation and add IPv6 addresses to the shared bandwidth to support both private and public IPv6 access.
Notes and Constraints
Kafka instances only support IPv4 EIPs. IPv6 EIPs are not supported.
Prerequisites
- You can change the public access setting only when the Kafka instance is in the Running state.
- (Optional) To access a Kafka instance using IPv6 addresses, ensure that IPv6 is enabled for the Kafka instance.
Enabling Public Access to a Kafka Instance
A client can use IPv4 or IPv6 addresses to access a Kafka instance over a public network.
On the Kafka console, the procedures for enabling public IPv4 access vary depending on the content displayed in the Connection area on the Overview page.
- To enable IPv4 public access when IPv6 is enabled, see section "Enabling Public IPv4 Access (SASL Cannot Be Changed)".
- To enable IPv4 public access when IPv6 is disabled, see section "Enabling Public IPv4 Access (Plaintext or Ciphertext Access Can Be Changed)".
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click a Kafka instance name to go to the Overview page.
- Click
 next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
If the EIPs are insufficient, do as follows to set them.
- Click Create Elastic IP to go to the Buy EIP page and purchase EIPs. For details, see Assigning an EIP.
- After the purchase is complete, return to the public access enabling page.
- Click
 after Elastic IP Address, select an EIP for each broker and then click
after Elastic IP Address, select an EIP for each broker and then click  .
. - You can view the operation progress on the Instance > Background Tasks page. If the task status is Successful, the modification has succeeded.
Figure 1 Enabling public access
After public access is enabled, configure security group rules listed in Table 1 before attempting to access Kafka. For details about accessing Kafka, see Connecting to an Instance.
Table 1 Kafka instance security group rules (public IPv4 access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9094
IP address or IP address group of the Kafka client
Accessing Kafka over a public network (without SSL)
Inbound
TCP
IPv4
9095
IP address or IP address group of the Kafka client
Accessing Kafka over a public network (with SSL)
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click a Kafka instance name to go to the Overview page.
- Click
 next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
If the EIPs are insufficient, do as follows to set them.
- Click Create Elastic IP to go to the Buy EIP page and purchase EIPs. For details, see Assigning an EIP.
- After the purchase is complete, return to the public access enabling page.
- Click
 after Elastic IP Address, select an EIP for each broker and then click
after Elastic IP Address, select an EIP for each broker and then click  . The Background Tasks page is displayed.
. The Background Tasks page is displayed. - If the status of the task turns to Successful, public access is successfully enabled.
Figure 2 Enabling public access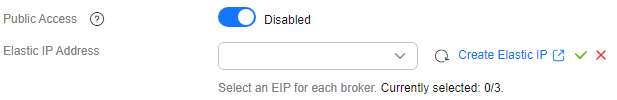
After public access is enabled, configure the access mode (plaintext or ciphertext) and security group rules listed in Table 2 before attempting to access Kafka. For details about accessing Kafka, see Connecting to an Instance.
Table 2 Kafka instance security group rules (public IPv4 access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9094
IP address or IP address group of the Kafka client
Public plaintext access to Kafka
Inbound
TCP
IPv4
9095
IP address or IP address group of the Kafka client
Public ciphertext access to Kafka
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click a Kafka instance name to go to the Overview page.
- In the Connection area, obtain IPv6 Instance Address (Private Network). In the Network area, view and record the VPC and subnet.
Figure 3 Instance details page
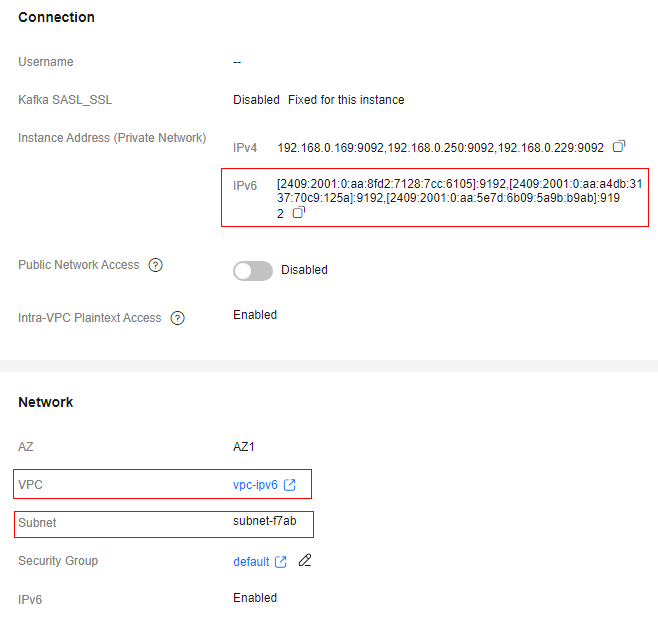
- Click
 in the upper left corner of the management console and choose Network > Elastic IP. The EIPs page is displayed.
in the upper left corner of the management console and choose Network > Elastic IP. The EIPs page is displayed. - Choose Shared Bandwidths in the navigation pane.
- Apply for a shared bandwidth. For details, see Assigning a Shared Bandwidth.
If a shared bandwidth already exists, you do not need to apply for one again.
- In the row containing the shared bandwidth, click Add Public IP Address.
- Set the parameters as described in Table 3 and click OK.
Table 3 Adding public IP parameters Parameter
Description
Public IP Address
Select IPv6 Address.
VPC
Select the VPC in 4 from the drop-down list.
Subnet
Select the subnet in 4 from the drop-down list. Select all IPv6 addresses in 4.
Figure 4 Adding public IPs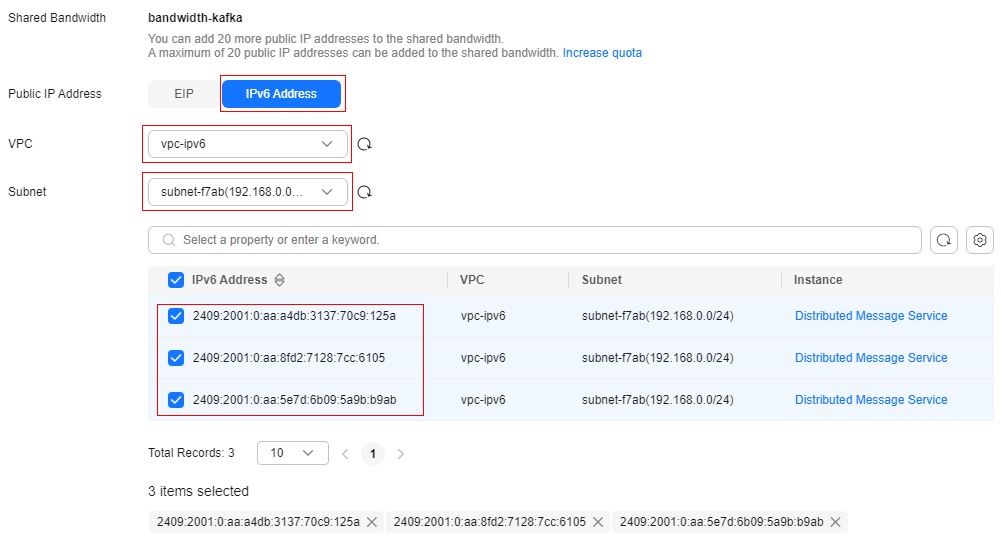
- After the shared bandwidth is configured, set a Kafka instance security group with the rules described in Table 4.
Table 4 Kafka instance security group rules (IPv6 access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv6
9192
::/0
Accessing a Kafka instance using IPv6 addresses (without SSL encryption)
Inbound
TCP
IPv6
9193
::/0
Accessing a Kafka instance using IPv6 addresses (with SSL encryption)
When a client is connected to a Kafka instance over an IPv6 public network:
- The Kafka connection addresses are the IPv6 addresses in Instance Address (Private Network).
- The client NIC must be added to shard bandwidth. Shared bandwidth is using a connected network. The shared bandwidth of the client NIC and that of the Kafka instance can be different.
Disabling Public Access to a Kafka Instance
On the Kafka console, the procedures for disabling public IPv4 access vary depending on the content displayed in the Connection area on the Overview page.
- To disable IPv4 public access when IPv6 is enabled, see section "Disabling Public IPv4 Access (SASL Cannot Be Changed)".
- To disable IPv4 public access when IPv6 is disabled, see section "Disabling Public IPv4 Access (Plaintext or Ciphertext Access Can Be Changed)".
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click a Kafka instance name to go to the Overview page.
- Click
 next to Public Access.
next to Public Access.
You can view the operation progress on the Instance > Background Tasks page. If the task status is Successful, the modification has succeeded.
After public access is disabled, configure security group rules listed in Table 5 before attempting to access Kafka in a VPC. For details about accessing Kafka, see Connecting to an Instance.
Table 5 Kafka instance security group rules (private access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9092
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (without SSL)
Inbound
TCP
IPv4
9093
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (with SSL)

After a security group is created, its default inbound rule allows communication among ECSs within the security group and its default outbound rule allows all outbound traffic. In this case, you can access a Kafka instance within a VPC, and do not need to add rules according to Table 5.
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click a Kafka instance name to go to the Overview page.
- Before disabling public access, disable Plaintext Access and Ciphertext Access next to Public Network Access. Then click
 next to Public Access.
next to Public Access. - Click OK. The Background Tasks page is displayed. If the status of the task turns to Successful, public access is successfully disabled.
After public access is disabled, configure security group rules listed in Table 6 before attempting to access Kafka in a VPC. For details about accessing Kafka, see Connecting to an Instance.

After a security group is created, its default inbound rule allows communication among ECSs within the security group and its default outbound rule allows all outbound traffic. In this case, you can access a Kafka instance within a VPC, and do not need to add rules according to Table 6.
Table 6 Kafka instance security group rules (private access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9092
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (in plaintext)
Inbound
TCP
IPv4
9093
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (in ciphertext)
Remove the IPv6 addresses of a Kafka instance from the shared bandwidth. For details, see Removing EIPs from a Shared Bandwidth.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





