Scenarios
You can configure security group rules to protect the instances such as cloud servers that are associated with the security group. A security group consists of inbound and outbound rules.
- Inbound rules control incoming traffic to cloud servers in the security group.
- Outbound rules control outgoing traffic from cloud servers in the security group.
Procedure
- Log in to the FlexusL console and click a resource card to go to the instance details page.
- In the navigation pane on the left, choose Cloud Servers and then click the server name.
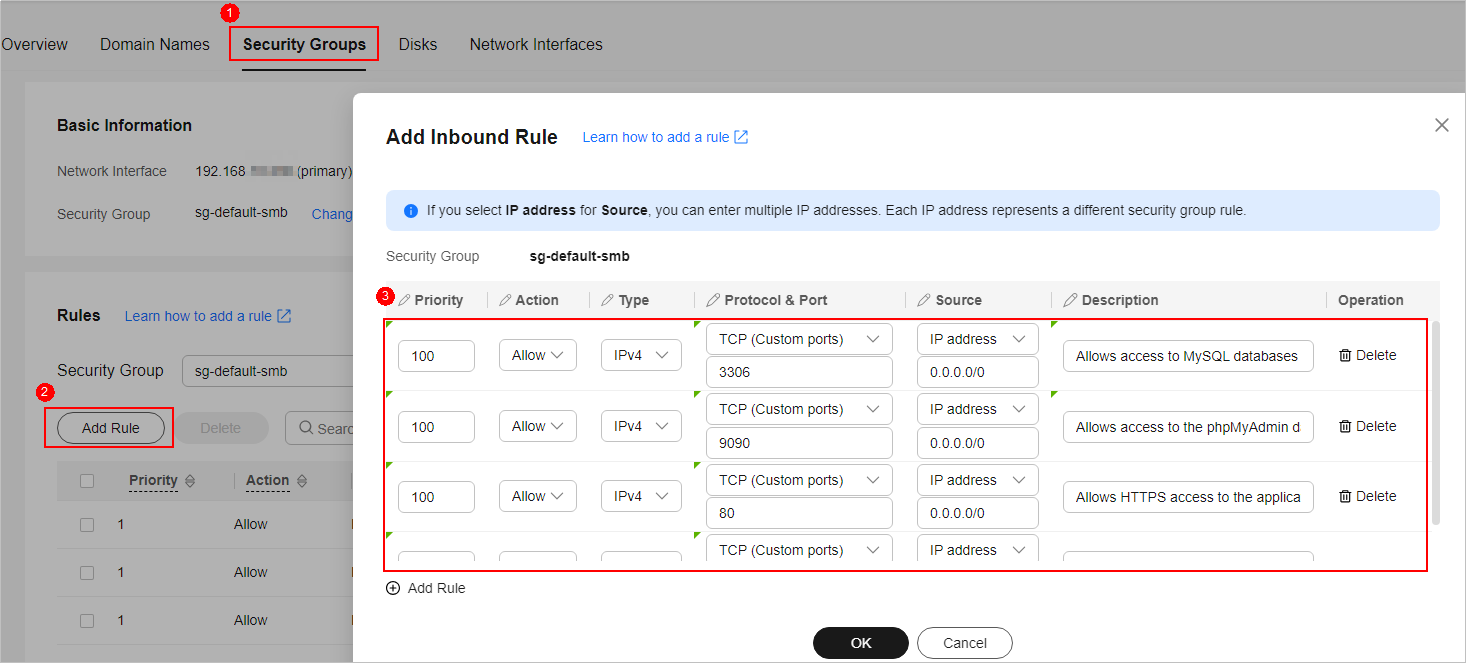
- On the Security Groups tab, select Inbound rules and click Add Rule.
You can click + to add more inbound rules.
Table 1 Inbound rule parameter description
|
Parameter |
Description |
Example Value |
|
Priority |
The security group rule priority.
The priority value ranges from 1 to 100. The default value is 1, indicating the highest priority. The security group rule with a smaller value has a higher priority. |
1 |
|
Action |
Allow or Deny
- If the Action is set to Allow, access from the source is allowed to cloud servers in the security group over specified ports.
- If the Action is set to Deny, access from the source is denied to cloud servers in the security group over specified ports.
Deny rules take precedence over allow rules of the same priority. |
Allow |
|
Type |
Source IP address version. You can select:
|
IPv4 |
|
Protocol & Port |
The network protocol used to match traffic in a security group rule.
Currently, the value can be All, TCP, UDP, ICMP, or more. |
TCP |
|
Destination port used to match traffic in a security group rule. The value can be from 1 to 65535.
Inbound rules control incoming traffic over specific ports to instances in the security group.
Specify one of the following:
- Individual port: Enter a port, such as 22.
- Consecutive ports: Enter a port range, such as 22-30.
- Non-consecutive ports: Enter ports and port ranges, such as 22,23-30. You can enter a maximum of 20 ports and port ranges. Each port range must be unique.
- All ports: Leave it empty or enter 1-65535.
|
22 or 22-30 |
|
Source |
The source in an inbound rule is used to match the IP address or address range of an external request. The source can be:
- IP address: If you select IP address for Source, you can enter multiple IP addresses in the same IP address box. Each IP address represents a different security group rule.
- Single IP address: IP address/mask
Example IPv4 address: 192.168.10.10/32
Example IPv6 address: 2002:50::44/128
- An IP address range in CIDR notation: IP address/mask
Example IPv4 address range: 192.168.52.0/24
Example IPv6 address range: 2407:c080:802:469::/64
- All IP addresses
0.0.0.0/0 represents all IPv4 addresses.
::/0 represents all IPv6 addresses.
- Security group: The source is from another security group. You can select a security group in the same region under the current account from the drop-down list. Instance A is in security group A and instance B is in security group B. If security group A has an inbound rule with Action set to Allow and Source set to security group B, access from instance B is allowed to instance A.
- IP address group: The source is an IP address group. An IP address group is a collection of one or more IP addresses. You can select an available IP address group from the drop-down list. An IP address group can help you manage IP address ranges and IP addresses with same security requirements in a more simple way.
|
IP address: 0.0.0.0/0 |
|
Description |
Supplementary information about the security group rule. This parameter is optional.
The description can contain a maximum of 255 characters and cannot contain angle brackets (< or >). |
- |
- On the Security Groups tab page, select Outbound rules and click Add Rule.
You can click
+ to add more outbound rules.
Table 2 Outbound rule parameter description
|
Parameter |
Description |
Example Value |
|
Priority |
The security group rule priority.
The priority value ranges from 1 to 100. The default value is 1, indicating the highest priority. The security group rule with a smaller value has a higher priority. |
1 |
|
Action |
Allow or Deny
- If the Action is set to Allow, access from cloud servers in the security group is allowed to the destination over specified ports.
- If the Action is set to Deny, access from cloud servers in the security group is denied to the destination over specified ports.
Deny rules take precedence over allow rules of the same priority. |
Allow |
|
Type |
Destination IP address version. You can select:
|
IPv4 |
|
Protocol & Port
|
The network protocol used to match traffic in a security group rule.
Currently, the value can be All, TCP, UDP, ICMP, or more. |
TCP |
|
Destination port used to match traffic in a security group rule. The value can be from 1 to 65535.
Outbound rules control outgoing traffic over specific ports from instances in the security group.
Specify one of the following:
- Individual port: Enter a port, such as 22.
- Consecutive ports: Enter a port range, such as 22-30.
- Non-consecutive ports: Enter ports and port ranges, such as 22,23-30. You can enter a maximum of 20 ports and port ranges. Each port range must be unique.
- All ports: Leave it empty or enter 1-65535.
|
22 or 22-30 |
|
Destination |
The destination in an outbound rule is used to match the IP address or address range of an internal request. The destination can be:
- IP address: If you select IP address for Destination, you can enter multiple IP addresses in the same IP address box. Each IP address represents a different security group rule.
- Single IP address: IP address/mask
Example IPv4 address: 192.168.10.10/32
Example IPv6 address: 2002:50::44/128
- An IP address range in CIDR notation: IP address/mask
Example IPv4 address range: 192.168.52.0/24
Example IPv6 address range: 2407:c080:802:469::/64
- All IP addresses
0.0.0.0/0 represents all IPv4 addresses.
::/0 represents all IPv6 addresses.
- Security group: The destination is from another security group. You can select a security group in the same region under the current account from the drop-down list. For example, instance A is in security group A and instance B is in security group B. If security group A has an outbound rule with Action set to Allow and Destination set to security group B, access from instance A is allowed to instance B.
- IP address group: The destination is an IP address group. An IP address group is a collection of one or more IP addresses. You can select an available IP address group from the drop-down list. An IP address group can help you manage IP address ranges and IP addresses with same security requirements in a more simple way.
|
IP address: 0.0.0.0/0 |
|
Description |
Supplementary information about the security group rule. This parameter is optional.
The description can contain a maximum of 255 characters and cannot contain angle brackets (< or >). |
- |
- Click OK.
Verifying Security Group Rules
After inbound and outbound rules are added, you can verify whether the rules take effect. Suppose you have deployed a website on a FlexusL instance server. To allow your users to access your website over port 80 (HTTP), you add a security group rule shown in Table 3.
Table 3 Security group rule
|
Direction |
Protocol/Application |
Port |
Source |
|
Inbound |
TCP |
80 |
0.0.0.0/0 |
Linux servers
To verify the security group rule on a Linux server:
- Log in to the server.
- Run the following command to check whether TCP port 80 is listened:
netstat -an | grep 80
If command output shown in Figure 2 is displayed, TCP port 80 is listened.
Figure 2 Command output for the Linux server

- Enter http://EIP bound to the server in the address box of the browser and press Enter.
If the requested page can be accessed, the security group rule has taken effect.
Related Operations
On the Inbound Rules and Outbound Rules tab pages, you can also modify, replicate, or delete existing rules.
Deleting security group rules will disable some functions.
- If you delete a rule with Protocol & Port specified as TCP: 20-21, you will not be able to upload files to or download them from servers using FTP.
- If you delete a rule with Protocol & Port specified as ICMP: All, you will not be able to ping the servers.
- If you delete a rule with Protocol & Port specified as TCP: 443, you will not be able to connect to websites on the servers using HTTPS.
- If you delete a rule with Protocol & Port specified as TCP: 80, you will not be able to connect to websites on servers using HTTP.
- If you delete a rule with Protocol & Port specified as TCP: 22, you will not be able to remotely connect to Linux server using SSH.