Help Center/
Database Security Service/
User Guide/
Database Security Encryption Management/
Operation Guide for Audit Administrators/
Viewing System Device Logs
Updated on 2025-11-27 GMT+08:00
Viewing System Device Logs
The system stores all device messages. The audit administrator can periodically check the device logs to ensure system security and compliance.
Procedure
- Log in to a database encryption and access control system as the audadmin user.
- In the navigation pane on the left, choose .
- (Optional) Set the filtering criteria and search for the related device logs.
Figure 1 Setting filter criteria
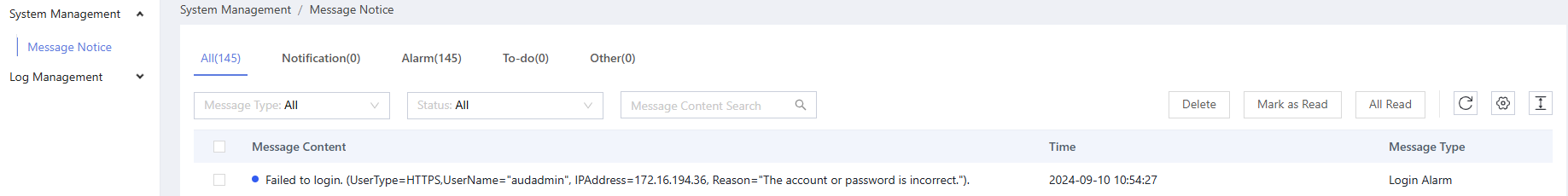
- View the logs in the list.
Parent topic: Operation Guide for Audit Administrators
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
The system is busy. Please try again later.
For any further questions, feel free to contact us through the chatbot.
Chatbot





