CloudDCN Subnet Network ACL Overview
What Is a CloudDCN Subnet Network ACL?
A network ACL is an optional layer of protection for your CloudDCN subnets. After you add inbound and outbound rules to a network ACL and associate CloudDCN subnets with it, you can control traffic in and out of the subnets.
Network ACL Rules for CloudDCN Subnets
- CloudDCN network ACLs has inbound and outbound rules that are used to control traffic in and out of CloudDCN subnets.
- Inbound rules: control traffic sent to the instances in a CloudDCN subnet.
- Outbound rules: control traffic from the instances in a CloudDCN subnet to external networks.
- You need to define the protocol, source and destination ports, source and destination IP addresses, and other information for network ACL rules.
- Rule number: Network ACL rules are matched in ascending order, from the lowest to highest rule number.
The default network ACL rule is marked with an asterisk (*) and is the very last rule that will be used for matching.
- Status: Enabled or Disabled. Enabled rules are applied, while disabled rules are not.
- Action: Allow or Deny. If a request matches a network ACL rule, the action defined in the rule is taken to allow or deny the request.
- Protocol: The protocol to match traffic. The value can be TCP, UDP, or ICMP.
- Source/Destination: The source or destination of the traffic.
- Source Port Range/Destination Port Range: The source or destination port or port range, which ranges from 1 to 65535.
- Rule number: Network ACL rules are matched in ascending order, from the lowest to highest rule number.
How Network ACL Rules Work
- After a network ACL is created, you can associate it with one or more CloudDCN subnets to control traffic in and out of the subnets. A network ACL can be associated with multiple CloudDCN subnets. However, a CloudDCN subnet can be associated with only one network ACL.
- The network ACLs dedicated for CloudDCN subnets are stateful. If the network ACL rule allows outbound traffic from your instance, you also need to set the inbound rule's action to Allow so that responses to outbound traffic to flow in. Similarly, if inbound traffic is allowed, you need to set the outbound rule's action to Allow so that responses to such inbound traffic to flow out.
- Each network ACL has the default inbound and outbound rules, as shown in Table 1. If a network ACL has no custom rules, the default inbound and outbound rules are applied, denying all traffic in and out of a CloudDCN subnet. You can use the default rules only when there is no need for traffic to go in and out of a CloudDCN subnet. If the traffic needs to go in and out of the subnet, you need to add custom rules to control traffic as required.
- The default and custom rules of a network ACL does not block the traffic described in Table 2.
Table 2 Traffic not blocked by network ACL rules Direction
Description
Inbound
Traffic between the source and destination in the same CloudDCN subnet
Broadcast traffic to 255.255.255.255/32
Multicast traffic to 224.0.0.0/24
Outbound
Traffic between the source and destination in the same CloudDCN subnet
Broadcast traffic to 255.255.255.255/32
Multicast traffic to 224.0.0.0/24
TCP metadata traffic to 169.254.169.254/32 over port 80
Traffic to 100.125.0.0/16 that is reserved for public services on the cloud, such as the DNS server address and NTP server address
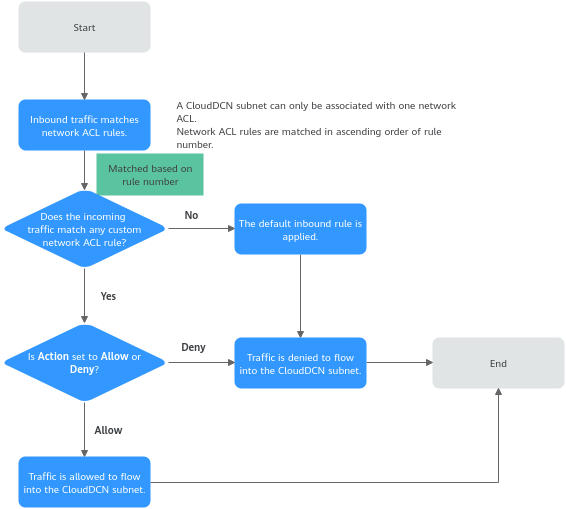
How Traffic Matches Network ACL Rules
A CloudDCN subnet can only be associated with one network ACL. If there are multiple rules on the network ACL, rules are matched in ascending order, from the lowest to highest rule number. The default network ACL rule is marked with an asterisk (*) and is the very last rule that will be used for matching.
- If a custom rule is matched:
- If Action is set to Deny, traffic is denied to flow into the CloudDCN subnet.
- If Action is set to Allow, traffic is allowed to flow into the CloudDCN subnet.
- If no custom rule is matched, the default rule is applied, denying traffic to flow into the CloudDCN subnet.
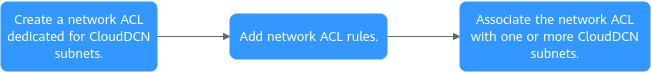
Network ACL Configuration Procedure
|
No. |
Step |
Description |
Procedure |
|---|---|---|---|
|
1 |
Create a network ACL dedicated for CloudDCN subnets. |
Each network ACL comes with default inbound and outbound rules that deny traffic in and out of a CloudDCN subnet. The default rules cannot be deleted or modified. |
|
|
2 |
Add network ACL rules. |
The default network ACL rules cannot be modified or deleted. You can add custom rules to control traffic in and out of a CloudDCN subnet. Traffic will be preferentially matched against the custom rules. |
|
|
3 |
Associate the network ACL with one or more CloudDCN subnets. |
You can associate the network ACL with one or more CloudDCN subnets. If it is enabled, it controls traffic in and out of the subnets. A CloudDCN subnet can be associated with only one network ACL. |
Constraints on Using Network ACLs
- By default, each account can have up to 5 network ACLs in a region.
- A network ACL can have no more than 40 rules in one direction, or performance will deteriorate.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





