Functions
IAM provides a variety of functions for you to secure access to your resources.
Refined Permissions Management
Secure Access
Instead of sharing your password with others, you can create IAM users for employees or applications in your organization and generate identity credentials for them to securely access specific resources based on assigned permissions.
Critical Operation Protection
IAM provides login protection and critical operation protection, making your account and resources more secure. When you or users created using your account log in to the console or perform a critical operation, you and the users need to complete authentication by email, SMS, or virtual MFA device.
User Group–based Permissions Assignment
With IAM, you do not need to assign permissions to single users. Instead, you can manage users by group and assign permissions to the specified group. Each user then inherits permissions from their groups. To change the permissions of a user, you can remove the user from the original groups or add the user to other groups.
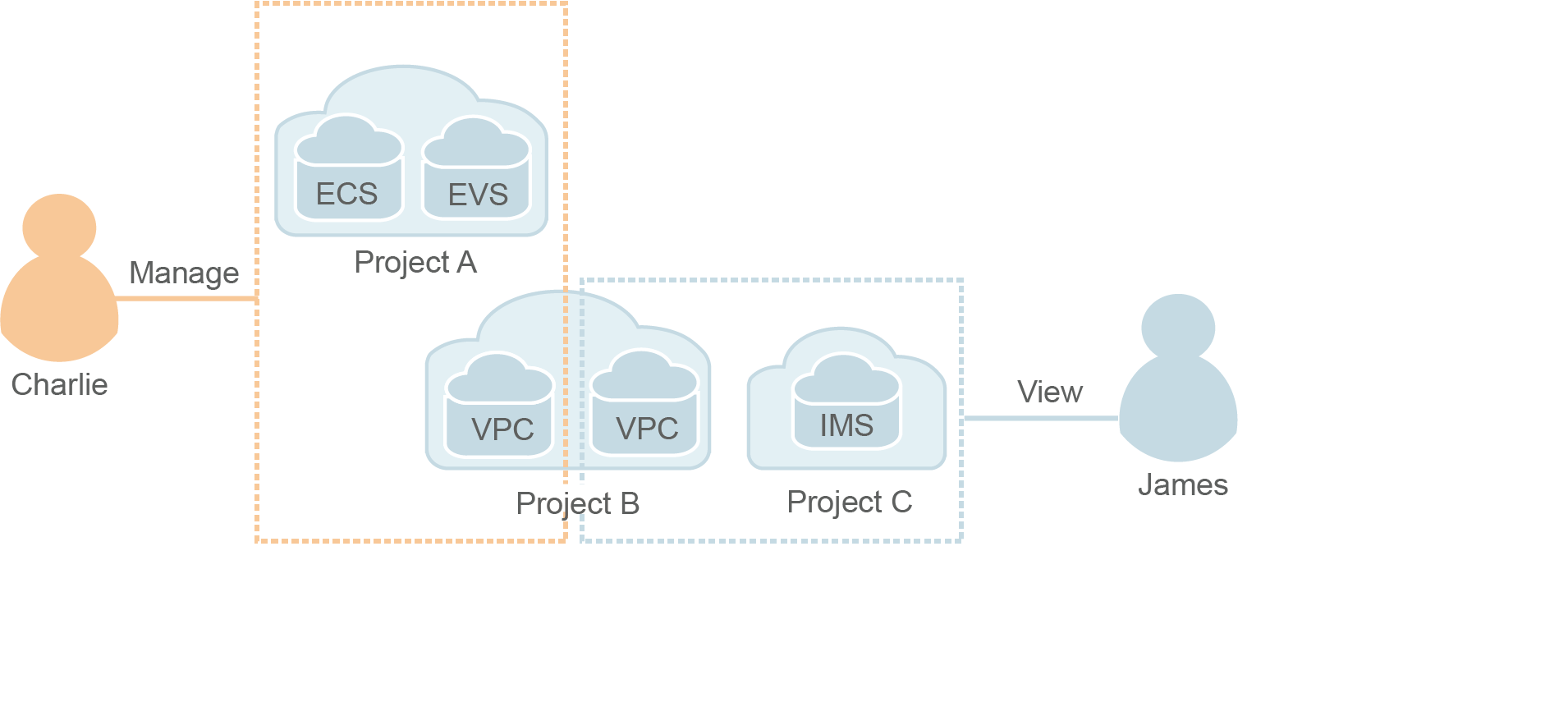
Project-based Resource Isolation
You can create subprojects in a region so that resources in that region can be isolated from each other.
Federated Identity Authentication
Enterprises with identity authentication systems can access the cloud platform through single sign-on (SSO), eliminating the need to create users on the cloud platform.
Resource Management Delegation
You can delegate more professional, efficient accounts or other cloud services to manage specific resources in your account.
Account Security Settings
Login authentication and password policies and access control list (ACL) improve security of user information and system data.
Eventual Consistency
Results of your IAM operations, such as creating users and user groups and assigning permissions, may not take effect immediately because data is replicated across different servers in the cloud platform's data centers around the world. Ensure that the operation results have taken effect before you perform any other operations that depend on them.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





