Scenario
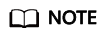
The Certificate Authority Service only issues identity certificates for network management software and devices. It does not issue personal certificates for authentication and signature for individual users.
NetEco CA Independent Networking
As shown in the figure, in the CA independent networking scenario, after the Certificate Authority Service is deployed on the NetEco and a CA is created, end entity certificates can be issued to the NetEco and services or devices. The NetEco and services or devices can apply for certificates from the NetEco CA through CMP or privacy CA protocol, and other devices, such as security gateways, can apply for certificates in offline mode.
This networking applies to small-scale networks where the number of network devices does not exceed the NetEco CA specifications. It does not apply to networks where different devices need to be divided into multiple subdomains.
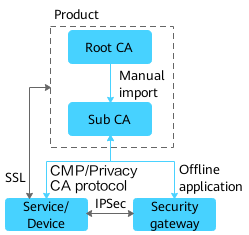
NetEco CA and Operator PKI Co-Networking
As shown in the figure, in the NetEco CA and operator PKI co-networking scenario, the NetEco subordinate CA issues end entity certificates to the NetEco and services or devices, and the operator subordinate CA issues end entity certificates to other devices such as security gateways. The operator PKI root CA certificate needs to be installed offline for services or devices, and the NetEco root CA certificate needs to be installed for other devices such as security gateways so that the mutual authentication can be successful.
This networking applies to the scenario where different subdomains are isolated from each other.
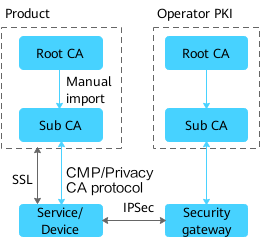
NetEco CA and Operator PKI Co-Networking, with NetEco CA Serving as Operator CA's Subordinate CA
As shown in the figure, in the NetEco CA and operator PKI co-networking scenario where the NetEco CA functions as the operator CA's subordinate CA, the NetEco subordinate CA issues end entity certificates to the NetEco and services or devices; and the operator subordinate CA issues end entity certificates to other devices such as security gateways. The operator PKI root CA certificate needs to be installed offline for services or devices, and also need to be installed on other devices such as security gateways so that the mutual authentication can be successful.
This networking applies to the scenario where a single root CA is used on the entire network, the root CA and subordinate CAs are deployed separately, and subordinate CAs are used to divide subdomains.

NetEco CA and Operator PKI Co-Networking (Multi-Operator Scenario)
As shown in the figure, in the NetEco CA and operator PKI co-networking (multi-operator) scenario, the NetEco and services or devices can apply for certificates from multiple CAs, and different CAs can be deployed for different operators to isolate IPsec tunnels between operators. The NetEco and services or devices can automatically apply for certificates from the NetEco CA through CMP or privacy CA protocol. Other devices, such as security gateways, need to apply for certificates offline. The NetEco CA certificate chain and operator PKI certificate chain need to be installed on services or devices and security gateways. Services or devices support automatic application and manual import in offline mode during the application of end entity certificates through CMP or privacy CA protocol.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





