How Do I Use the New IAM Edition to Isolate Permissions by Enterprise Project?
IAM of the new edition does not support direct permission isolation by enterprise project. Instead, it uses resource tags to achieve such permission isolation. For example, by using resource tags to isolate enterprise project permissions, you can set IAM users with enterprise project A's permissions to access only test projects with the EnterpriseProject:Enterprise project A tag. This capability depends on the new IAM, requiring you to adopt the IAM 5.0 permission model. Exercise caution when selecting this capability.
Process of isolating permissions using resource tags:
- Configuring Custom Permission Policies for IAM Users on the IAM Console
- Configuring Resource Tags for the Target Project on the CodeArts PerfTest Console
Custom identity policies control permission types and access scopes. Specifically, actions are used to control permission types, while resource tags are used to control access scopes, implementing permission isolation at the enterprise project level.
Resource tags are in key:value format. You are advised to set them to EnterpriseProject:Enterprise project name. The user permissions isolation is as follows:

Configuring Custom Permission Policies for IAM Users on the IAM Console
- Click
 in the upper left corner of the console, and search for and click Identity and Access Management.
in the upper left corner of the console, and search for and click Identity and Access Management. - Click Go to New Console in the upper right corner.
- Create custom identity policies.
- In the navigation pane, choose Identity Policies.
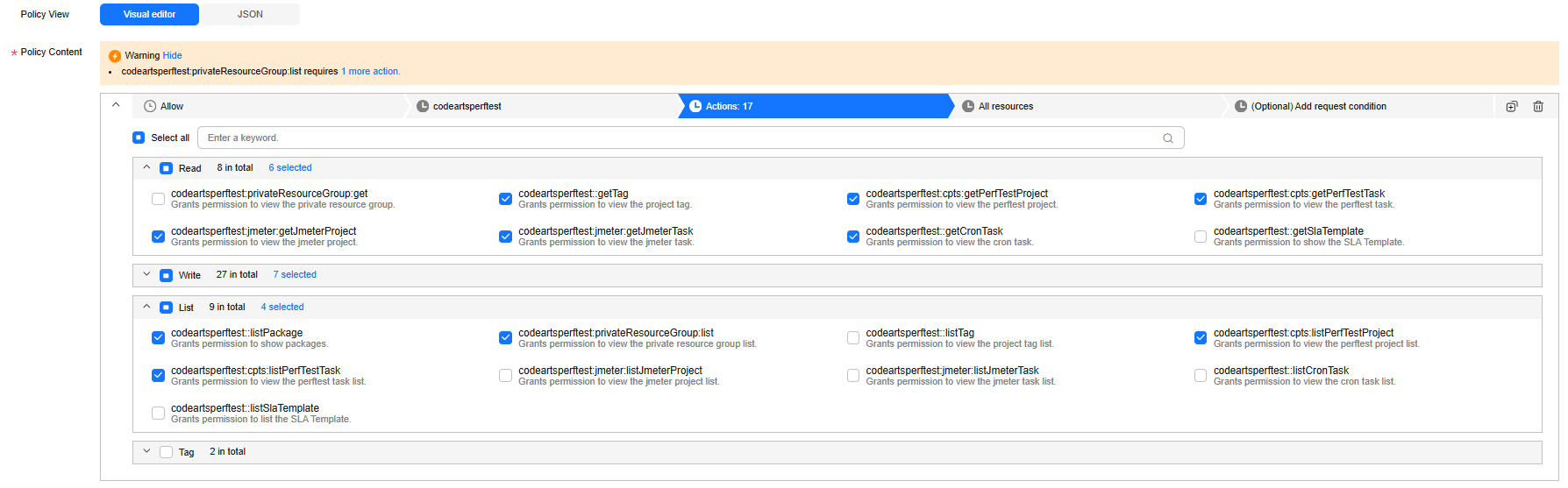
- Click Create Custom Policy in the upper right corner. Enter a policy name based on your enterprise project or authorization scope, for example, EnterpriseProjectA_policy. For Policy Content, select Allow, then click Select service and select CodeArts PerfTest (codeartsperftest). In the displayed action list, select the desired user permission policies.
Figure 3 User permission policies
- Still for Policy Content, click (Optional) Add request condition > Add Request Condition. In the displayed dialog box, set parameters as instructed in Table 1 and click OK.
- Click OK.
- Repeat 3.b to 3.d to create multiple custom identity policies and associate them with different enterprise project tags.
- Grant permissions to a user group. The following operations use a user group as an example. The operations for a user are similar.
- In the navigation pane, choose User Groups.
- Locate the user group to which you want to attach a custom identity policy, and click Authorize in the Operation column.
- Select a custom identity policy created in 3 and click OK.
- Repeat 4.b to 4.c to attach different custom identity policies to different user groups.
Configuring Resource Tags for the Target Project on the CodeArts PerfTest Console
- Log in to the CodeArts PerfTest console and locate the target test project.
- Click
 on the right and choose Modify Tag.
Figure 4 Modifying a tag
on the right and choose Modify Tag.
Figure 4 Modifying a tag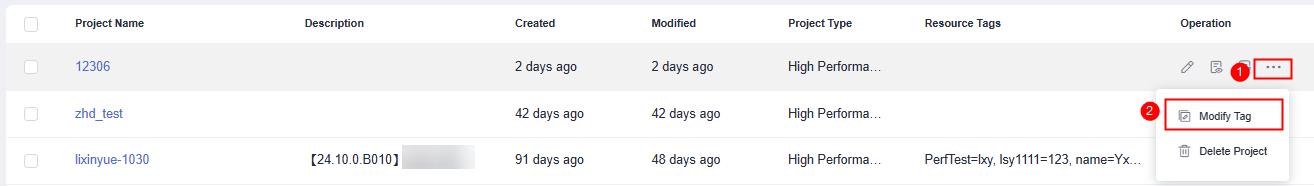
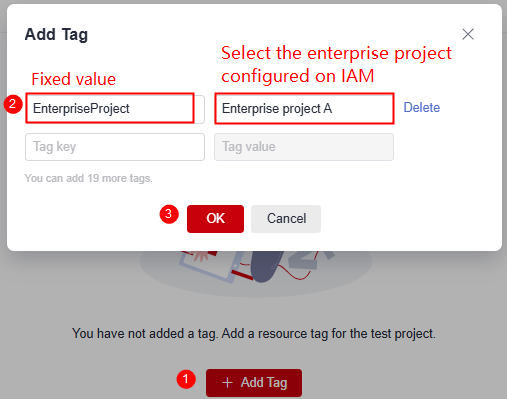
- Click Add Tag. In the displayed dialog box, enter EnterpriseProject for Tag Key, enter the enterprise project name configured in IAM (Enterprise project A in this example) for Tag Value, and click OK.
Figure 5 Adding a tag
Verifying Permission Configurations
After the preceding configurations are complete, when a user accesses the target test project, CodeArts PerfTest verifies if the enterprise project resource tag associated with that test project has been configured for the user on the IAM console. In this example, if a custom identity policy with the EnterpriseProject:Enterprise project A tag has been configured for user 1 in IAM, user 1 can access only the projects carrying this tag. If user 1 tries to access other projects, a message indicating insufficient permissions will be displayed.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





