Using Access Control to Protect Your Resources
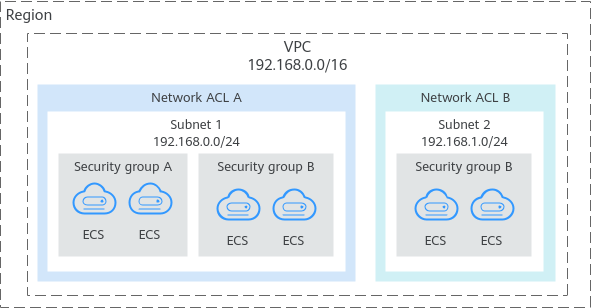
- A security group protects the instances in it.
- A network ACL protects associated subnets and all the resources in the subnets.
As shown in Figure 1, security groups A and B protect the network security of ECSs. Network ACLs A and B add an additional layer of defense to ECSs in subnets 1 and 2.
- Security group: Allowing Traffic from Given IP Addresses or a Security Group
- Security group: Allowing Traffic from a Virtual IP Address
- Security group: Allowing Communications Between Instances in Two VPCs Connected by a VPC Peering Connection
- Network ACL: Allowing Traffic from Specific IP Addresses to the Instances in a Subnet
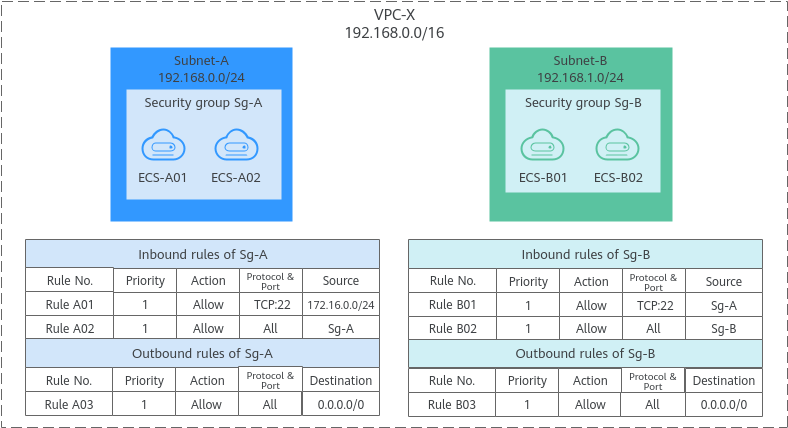
Allowing Traffic from Given IP Addresses or a Security Group
- Add inbound rule A01 to Sg-A to allow traffic from IP addresses in 172.16.0.0/24 to access SSH port 22 on the ECSs in Sg-A for remotely logging in to these ECSs.
- Add inbound rule B01 to Sg-B to allow the ECSs in Sg-A to access SSH port 22 on the ECSs in Sg-B for remotely logging in to the ECSs in Subnet-B.
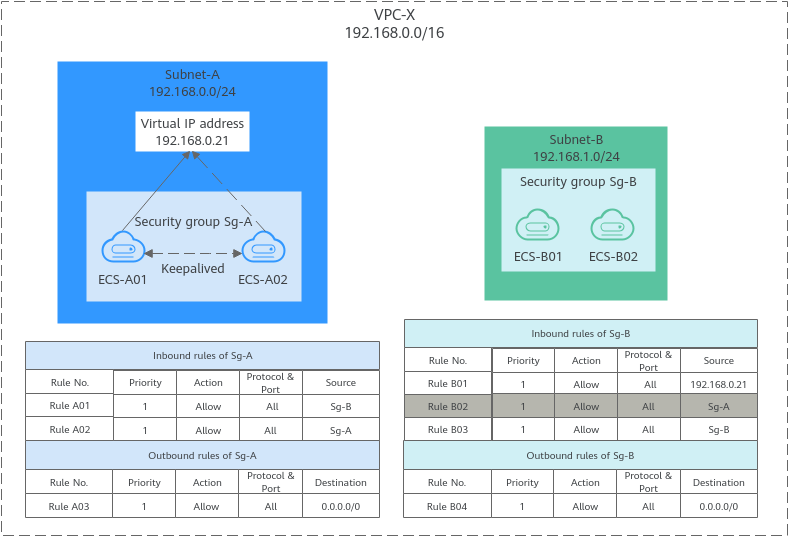
Allowing Traffic from a Virtual IP Address
- Add inbound rule A01 to Sg-A to allow the ECSs in Sg-B to access the ECSs in Sg-A using private IP addresses.
- Add inbound rule B01 to Sg-B to allow traffic from virtual IP address 192.168.0.21 to the ECSs in Sg-B using any protocol over any port. You can also set the source to the CIDR block of Subnet-A (192.168.0.0/24).
Do not add rules like rule B02. This rule allows the ECSs in Sg-A to access the ECSs in Sg-B using private IP addresses but not virtual IP address 192.168.0.21.
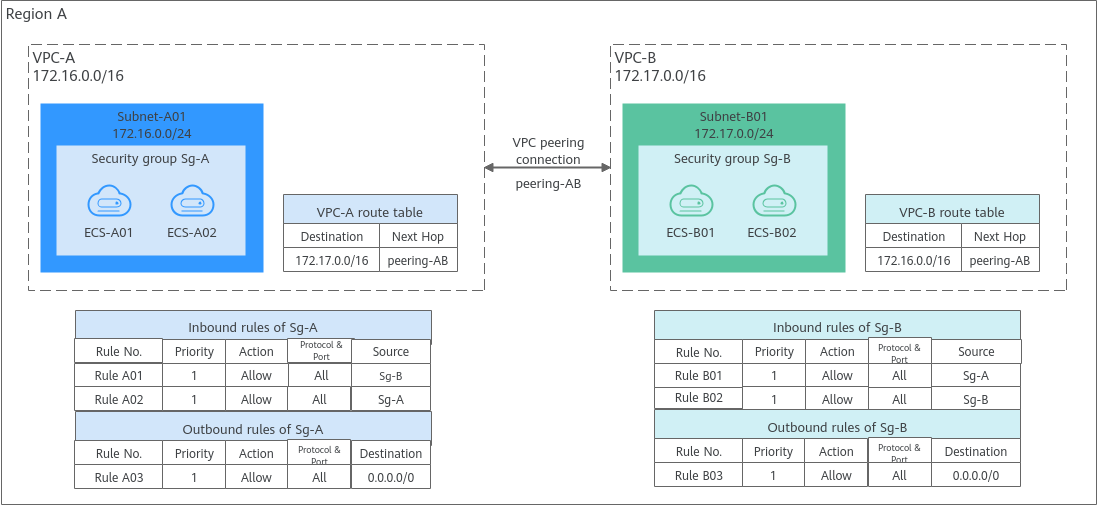
Allowing Communications Between Instances in Two VPCs Connected by a VPC Peering Connection
- Rule A01 with Source to Sg-B to allow ECSs in Sg-B to access ECSs in Sg-A.
- Rule B01 with Source to Sg-A to allow ECSs in Sg-A to access ECSs in Sg-B.
Allowing Traffic from Specific IP Addresses to the Instances in a Subnet
- Inbound rule A01 of security group Sg-A allows traffic from any IP address to the ECSs in Sg-A over SSH port 22.
- To enhance security, add inbound rule A01 to network ACL Fw-A to allow traffic from 10.0.1.0/24 to the ECSs in Subnet-A over SSH port 22.
The default inbound rule of Fw-A denies all traffic to the ECSs in Subnet-A. So you need to add custom rules to allow access from specific IP addresses. If you associate Subnet-A with Fw-A, the instances in Subnet-A can still communicate with each other.

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot