VPC and Subnet Planning Suggestions
Before creating your VPCs, determine how many VPCs, the number of subnets, and what IP address ranges or connectivity options you will need.
- How Do I Determine How Many VPCs I Need?
- How Do I Plan Subnets?
- How Do I Plan Routing Policies?
- How Do I Connect to an On-Premises Data Center?
- How Do I Access the Internet?
How Do I Determine How Many VPCs I Need?
VPCs are region-specific. By default, networks in VPCs in different regions or even in the same region are not connected.
- One VPC
If your services do not require network isolation, a single VPC should be enough.
- Multiple VPCs
If you have multiple service systems in a region and each service system requires an isolated network, you can create a separate VPC for each service system.
- If two VPCs are in the same region, use a VPC peering connection.
- If two VPCs are in different regions, use Cloud Connect.
By default, you can create a maximum of five VPCs in each region. If this cannot meet your service requirements, request a quota increase. For details, see How Do I Apply for a Higher Quota?
- Number of IP addresses: Reserve sufficient IP addresses in case of business growth.
- IP address range: Avoid IP address conflicts if you need to connect a VPC to an on-premises data center or connect two VPCs.
VPC CIDR Block |
IP Address Range |
Maximum Number of IP Addresses |
|---|---|---|
10.0.0.0/8-24 |
10.0.0.0-10.255.255.255 |
2^24-2=16777214 |
172.16.0.0/12-24 |
172.16.0.0-172.31.255.255 |
2^20-2=1048574 |
192.168.0.0/16-24 |
192.168.0.0-192.168.255.255 |
2^16-2=65534 |

Table 1 describes the primary IPv4 CIDR blocks available for a VPC. After a VPC is created, its primary CIDR block cannot be modified. If the primary CIDR block is insufficient, you can add a secondary IPv4 CIDR block for the VPC.
How Do I Plan Subnets?
- After a subnet is created, its CIDR block cannot be modified. Subnets in the same VPC cannot overlap.
When you create a VPC, a default subnet will be created together. If you need more subnets, see Creating a Subnet for the VPC.
A subnet mask can be between the netmask of its VPC CIDR block and /28 netmask. If a VPC CIDR block is 10.0.0.0/16, its subnet mask can be between 16 and 28.
For example, if the CIDR block of VPC-A is 10.0.0.0/16, you can specify 10.0.0.0/24 for subnet A01, 10.0.1.0/24 for subnet A02, and 10.0.2.0/24 for subnet A03.
By default, you can create a maximum of 100 subnets in each region. If this cannot meet your service requirements, request a quota increase by referring to How Do I Apply for a Higher Quota?
When planning subnets, consider the following:
- You create different subnets for different modules in a VPC. For example, in VPC-A, you can create subnet A01 for web services, subnet A02 for management services, and subnet A03 for data services. You can leverage network ACLs to control access to each subnet.
- If your VPC needs to communicate with an on-premises data center through VPN or Direct Connect, ensure that the VPC subnet and the CIDR block used for communication in the data center do not overlap.
How Do I Plan Routing Policies?
When you create a VPC, the system automatically generates a default route table for the VPC. If you create a subnet in the VPC, the subnet automatically associates with the default route table. A route table contains a set of routes that are used to determine where network traffic from your subnets in a VPC is directed. The default route table ensures that subnets in a VPC can communicate with each other.
If you do not want to use the default route table, you can now create a custom route table and associate it with the subnets. The custom route table associated with a subnet affects only the outbound traffic. The default route table controls the inbound traffic.
You can add routes to default and custom route tables and configure the destination, next hop type, and next hop in the routes to determine where network traffic is directed. Routes are classified into system routes and custom routes.
- System routes: Routes that are automatically added by the system and cannot be modified or deleted. System routes allow instances in a VPC to communicate with each other.
- Custom routes: Routes that can be modified and deleted. The destination of a custom route cannot overlap with that of a system route.
You cannot add two routes with the same destination to a VPC route table even if their next hop types are different, because the destination determines the route priority. According to the longest match routing rule, the destination with a higher matching degree is preferentially selected for packet forwarding.
How Do I Connect to an On-Premises Data Center?
If you require interconnection between a VPC and an on-premises data center, ensure that the VPC does not have an overlapping IP address range with the on-premises data center to be connected.
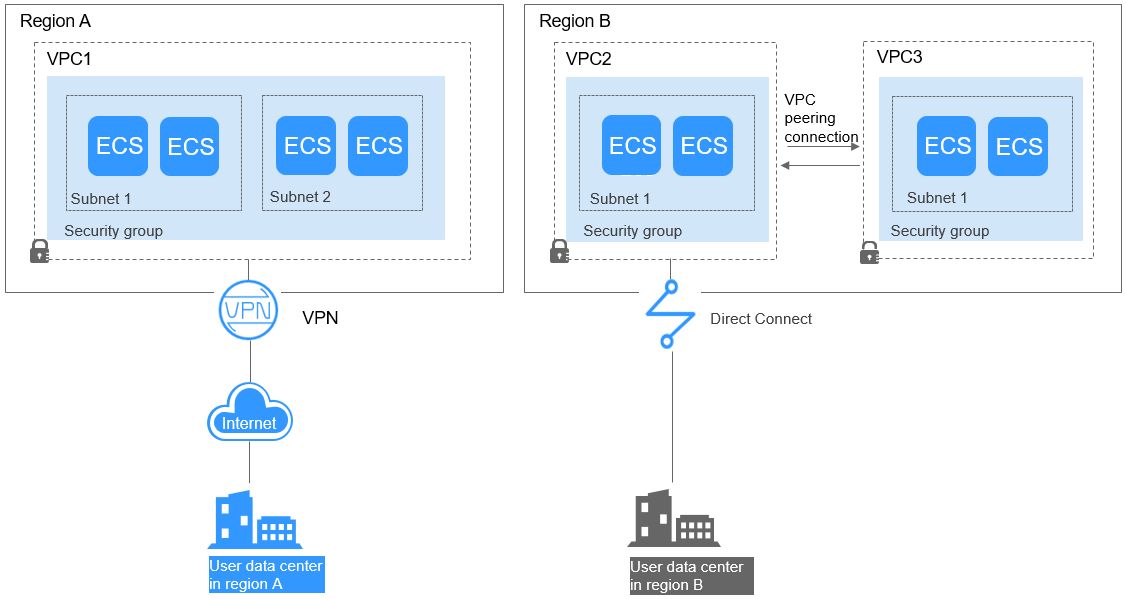
As shown in Figure 1, you have VPC 1 in region A and VPC 2 and VPC 3 in region B. To connect to an on-premises data center, they can use a VPN, as VPC 1 does in Region A; or a Direct Connect connection, as VPC 2 does in Region B. VPC 2 connects to the data center through a Direct Connect connection, but to connect to another VPC in that region, like VPC 3, a VPC peering connection must be established.
When planning CIDR blocks for VPC 1, VPC 2, and VPC 3:
- The CIDR block of VPC 1 cannot overlap with the CIDR block of the on-premises data center in Region A.
- The CIDR block of VPC 2 cannot overlap with the CIDR block of the on-premises data center in Region B.
- The CIDR blocks of VPC 2 and VPC 3 cannot overlap.
How Do I Access the Internet?
Use EIPs to enable a small number of ECSs to access the Internet.
When only a few ECSs need to access the Internet, you can bind the EIPs to the ECSs. This will provide them with Internet access. You can also dynamically unbind the EIPs from the ECSs and bind them to NAT gateways and load balancers instead, which will also provide Internet access. The process is not complicated.
For more information about EIP, see EIP Overview.
Use a NAT gateway to enable a large number of ECSs to access the Internet.
When a large number of ECSs need to access the Internet, the public cloud provides NAT gateways for your ECSs. With NAT gateways, you do not need to assign an EIP to each ECS. NAT gateways reduce costs as you do not need so many EIPs. NAT gateways offer both source network address translation (SNAT) and destination network address translation (DNAT). SNAT allows multiple ECSs in the same VPC to share one or more EIPs to access the Internet. SNAT prevents the EIPs of ECSs from being exposed to the Internet. DNAT can implement port-level data forwarding. It maps EIP ports to ECS ports so that the ECSs in a VPC can share the same EIP and bandwidth to provide Internet-accessible services.
For more information, see NAT Gateway User Guide.
Use ELB to access the Internet If there are a large number of concurrent requests.
In high-concurrency scenarios, such as e-commerce, you can use load balancers provided by the ELB service to evenly distribute incoming traffic across multiple ECSs, allowing a large number of users to concurrently access your business system or application. ELB is deployed in the cluster mode. It provides fault tolerance for your applications by automatically balancing traffic across multiple AZs. You can also take advantage of deep integration with Auto Scaling (AS), which enables automatic scaling based on service traffic and ensures service stability and reliability.
For more information, see Elastic Load Balance User Guide.
Helpful Links
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot