Viewing Detected Threats
MTD detects IAM, DNS, CTS, OBS, and VPC logs of global services in the target region. MTD detects potential malicious activities and unauthorized behavior through IP addresses and domain names in service logs in real time and generates alarms. You can perform the following steps to quickly detect threats, and check and handle them in descending order of alarm severity to secure running of your services.
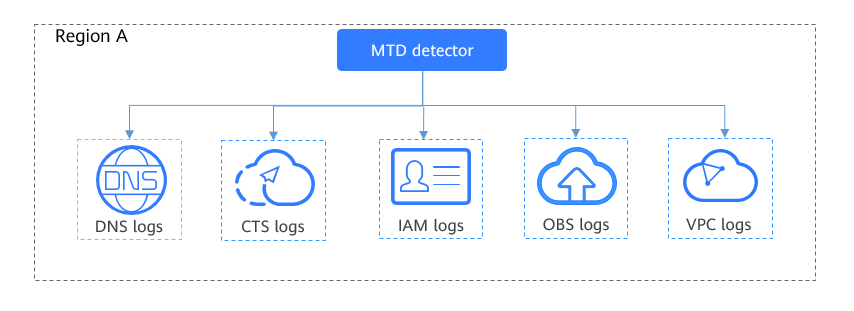
Detection Result
- Log in to the management console.
- Click
 and choose Security & Compliance > Managed Threat Detection.
Figure 2 MTD console
and choose Security & Compliance > Managed Threat Detection.
Figure 2 MTD console
- Choose Detection Result in the navigation pane on the left.
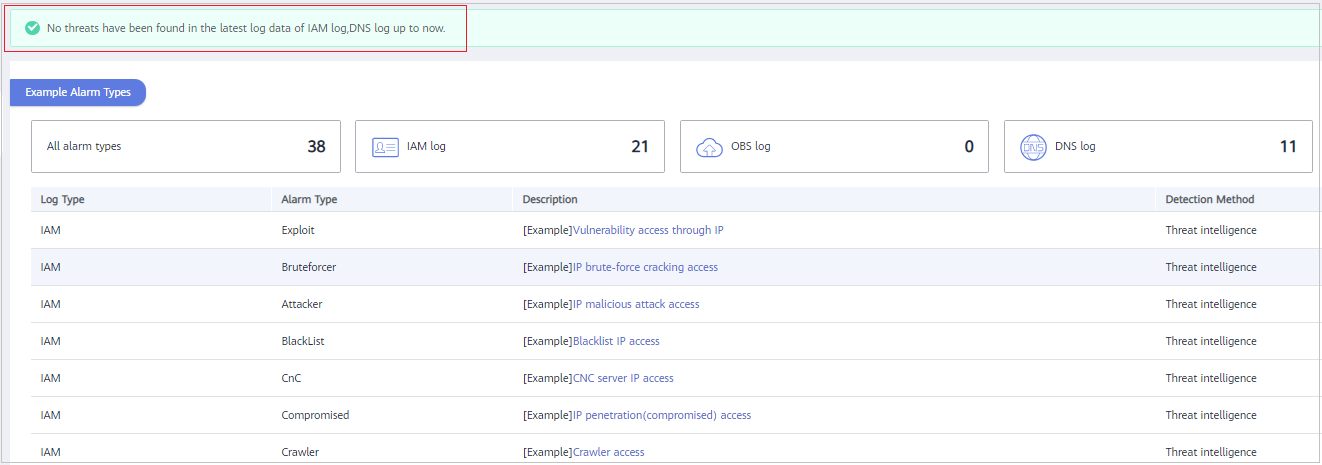
- If there are no alarms, a message is displayed, indicating that no threats have been found in the latest log data of your service up to now. The alarm types are displayed.
Figure 3 No threats found
- If there are alarms, the alarm list is displayed.
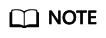
- Click Currently, xx alarm types are supported. In the displayed pane, you can view examples of all alarm types for logs of different services. For details, see Example Alarms and Statistics.
- It takes about three months to train the AI detection model based on your actual data after the model is brought online. The detection result in the training phase may be inaccurate. To improve the accuracy, you can click Report Alarm Accuracy in the Operation column of the alarm list.
- Alarms are sorted in descending order of the latest occurrence time. Table 1 describes information about the alarm list.
Table 1 Alarm information Parameter
Description
Log Type
Service logs for which the alarm is generated
- IAM
- VPC
- DNS
- CTS
- OBS
Alarm Type
Multiple types of alarms are supported. For details, see Viewing Alarm Types.
Alarm Title
Description of an alarm
Severity
Severity of an alarm
- Critical
- High
- Medium
- Low
- Informational
Currently, alarm must be manually checked and handled. You are advised to view alarm types and handle the alarms in descending order of the alarm severity.
Affected Resources
Number of resources that may be under threats
Alarms Triggered
Number of times that an alarm is generated. You can click
 to switch the sorting order.
to switch the sorting order.First Occurrence
Time when the alarm is generated for the first time. You can click
 to switch the sorting order.
to switch the sorting order.Last Occurrence
Time when the alarm was generated last time. You can click
 to switch the sorting order.
to switch the sorting order. - Click an alarm title to view details. You can come up with a handling method of the potential threats based on attack information such as the resource name, ID, type, and region.
- Report alarm accuracy.
You can report the detection accuracy to help MTD improve.
- Report a single alarm. Click Report Alarm Accuracy in the Operation column. In the dialog box that is displayed, click Accurate or Inaccurate.
- Report alarms in batches. Select multiple alarms and click Report Alarm Accuracy above the check boxes. In the dialog box that is displayed, click Accurate or Inaccurate.
- If there are no alarms, a message is displayed, indicating that no threats have been found in the latest log data of your service up to now. The alarm types are displayed.
Alarm Type Details
MTD integrates three detection models: detection policy, threat intelligence, and AI detection engine. Table 2 describes the details, covering 71 alarm types.
A single alarm can be of one or more severities based on evaluation methods and risk coefficients.
|
Model |
Description |
Log Types and Quantity |
|---|---|---|
|
AI detection engine |
Machine learning is used to explore suspicious access behavior to detect potential threats. |
|
|
Detection policy |
The logs are checked based on existing standards and fixed policies. |
OBS logs: 11 types |
|
Threat intelligence |
Correlation analysis and detection on log information are performed based on the historical valid intelligence collected by third parties. The third-party intelligence is updated once a day. |
|
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





