Configuring LDAP-based sudo Authentication
Overview
sudo is an application that allows users to obtain root or administrator permissions on Linux. sudo can be configured in multiple ways. You can set up a sudo on a local computer or server, or set up a centralized sudo via third-party software. In this section, an OpenLDAP server is used to set up a centralized sudo. In this way, you can manage users and sudo permissions centrally on the OpenLDAP server to allow faster installation on the client side. Any SSSD service on the client configured with a sudo authentication source allows OpenLDAP users to execute sudo.
Prerequisites
- A yum repository has been configured. For details about how to configure a yum repository accessed over the Internet, see Configuring Repositories and Installing Software for HCE.
- The OpenLDAP server and client have been deployed.
- The SSSD service has been installed and configured on the client.
Procedure
- Import the sudo schema.
- Create the /etc/openldap/schema/sudo.schema file on the OpenLDAP server and write the following content to the file:
# OpenLDAP schema file for Sudo # Save as /etc/openldap/schema/sudo.schema and restart slapd. # For a version that uses online configuration, see schema.olcSudo. # attributetype ( 1.3.6.1.4.1.15953.9.1.1 NAME 'sudoUser' DESC 'User(s) who may run sudo' EQUALITY caseExactIA5Match SUBSTR caseExactIA5SubstringsMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.2 NAME 'sudoHost' DESC 'Host(s) who may run sudo' EQUALITY caseExactIA5Match SUBSTR caseExactIA5SubstringsMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.3 NAME 'sudoCommand' DESC 'Command(s) to be executed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.4 NAME 'sudoRunAs' DESC 'User(s) impersonated by sudo (deprecated)' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.5 NAME 'sudoOption' DESC 'Options(s) followed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.6 NAME 'sudoRunAsUser' DESC 'User(s) impersonated by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.7 NAME 'sudoRunAsGroup' DESC 'Group(s) impersonated by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 ) attributetype ( 1.3.6.1.4.1.15953.9.1.8 NAME 'sudoNotBefore' DESC 'Start of time interval for which the entry is valid' EQUALITY generalizedTimeMatch ORDERING generalizedTimeOrderingMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.24 ) attributetype ( 1.3.6.1.4.1.15953.9.1.9 NAME 'sudoNotAfter' DESC 'End of time interval for which the entry is valid' EQUALITY generalizedTimeMatch ORDERING generalizedTimeOrderingMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.24 ) attributetype ( 1.3.6.1.4.1.15953.9.1.10 NAME 'sudoOrder' DESC 'an integer to order the sudoRole entries' EQUALITY integerMatch ORDERING integerOrderingMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.27 ) objectclass ( 1.3.6.1.4.1.15953.9.2.1 NAME 'sudoRole' SUP top STRUCTURAL DESC 'Sudoer Entries' MUST ( cn ) MAY ( sudoUser $ sudoHost $ sudoCommand $ sudoRunAs $ sudoRunAsUser $ sudoRunAsGroup $ sudoOption $ sudoOrder $ sudoNotBefore $ sudoNotAfter $ description ) ) - Create a conversion configuration file.
cat > ./schema_conv.conf << EOL include /etc/openldap/schema/sudo.schema EOL
- Convert the schema into an LDIF file.
mkdir /tmp/ldif slaptest -f ./schema_conv.conf -F /tmp/ldif/
- Copy the LDIF file to the schema directory.
cp /tmp/ldif/cn\=config/cn\=schema/cn\=\{0\}sudo.ldif /etc/openldap/schema/sudo.ldif - Open sudo.ldif and change the values of dn and cn, as shown in the following figure.
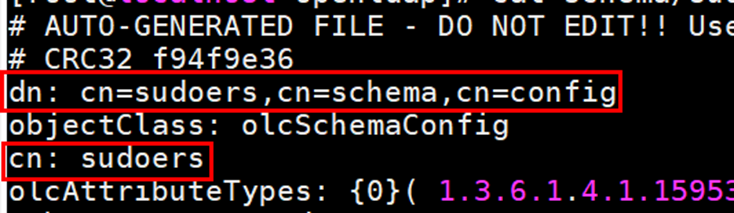 Delete the following lines at the end of the file (the line content is for reference only):
Delete the following lines at the end of the file (the line content is for reference only):structuralObjectClass: olcSchemaConfig entryUUID: b1d84e62-d5fa-103f-92ae-45f3b9c81bd2 creatorsName: cn=config createTimestamp: 20250605014651Z entryCSN: 20250605014651.004275Z#000000#000#000000 modifiersName: cn=config modifyTimestamp: 20250605014651Z
- Modify the file permissions.
chown ldap:ldap /etc/openldap/schema/sudo.ldif
- Import the schema to LDAP so that LDAP can support sudo configuration.
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/sudo.ldif systemctl restart slapd
- Create the /etc/openldap/schema/sudo.schema file on the OpenLDAP server and write the following content to the file:
- Create an organizational unit sudoers.
- On the OpenLDAP client, create the sudoers.ldif file and write the following content to the file:
dn: ou=sudoers,dc=huawei,dc=com objectClass: organizationalUnit objectClass: top ou: sudo description: Default ou for SUDO dn: cn=defaults,ou=sudoers,dc=huawei,dc=com objectClass: sudoRole objectClass: top cn: defaults sudoHost: ALL sudoOption: secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
An organizational unit sudoers will be created, with default settings.

The domain name and default sudo settings are examples only. You can modify the file content as needed.
- Add sudoers settings to the LDAP server.
ldapadd -x -D cn=Manager,dc=huawei,dc=com -W -f sudoers.ldif

Change the administrator account in the command based on the actual OpenLDAP deployment.
- On the OpenLDAP client, create the sudoers.ldif file and write the following content to the file:
- Add an OpenLDAP user to the sudoers organizational unit.
- To add an existing OpenLDAP user (for example, test1) to sudoers, create the user_add.ldif file and write the following content to the file:
dn: cn=test1,ou=sudoers,dc=huawei,dc=com objectClass: sudoRole objectClass: top cn: test1 sudoCommand: ALL sudoHost: ALL sudoRunAsUser: ALL sudoUser: test1
To add a new OpenLDAP user (for example, test2) to sudoers by default when the user is created, create the user_add.ldif file and write the following content to the file:dn: uid=test2,ou=People,dc=huawei,dc=com objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount cn: test2 sn: temp userPassword: {SSHA}cDG5NuQd+rYn6rWh1r5UnysUOwJlt1uk loginShell: /bin/bash uidNumber: 2000 gidNumber: 2000 homeDirectory: /home/test2 shadowLastChange: 0 shadowMax: 0 shadowWarning: 0 dn: cn=test2,ou=Group, dc=huawei,dc=com objectClass: posixGroup cn: test2 gidNumber: 2000 memberUid: test2 dn: cn=test2,ou=sudoers, dc=huawei,dc=com objectClass: sudoRole objectClass: top cn: test2 sudoCommand: ALL sudoHost: ALL sudoRunAsUser: ALL sudoUser: test2
Change the home directory, username, uidNumber, gidNumber, userPassword, sudo configuration items, and other information as needed. You can run slappasswd to generate a value for userPassword.
- Add configurations to the OpenLDAP server.
ldapadd -x -D cn=Manager,dc=huawei,dc=com -W -f user_add.ldif
- To add an existing OpenLDAP user (for example, test1) to sudoers, create the user_add.ldif file and write the following content to the file:
- Perform configurations on the client.
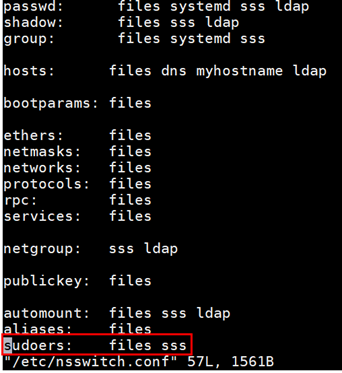
- Add the following configuration to /etc/nsswitch.conf so that the SSSD service can manage sudoers configurations:
sudoers: files sss
Result:
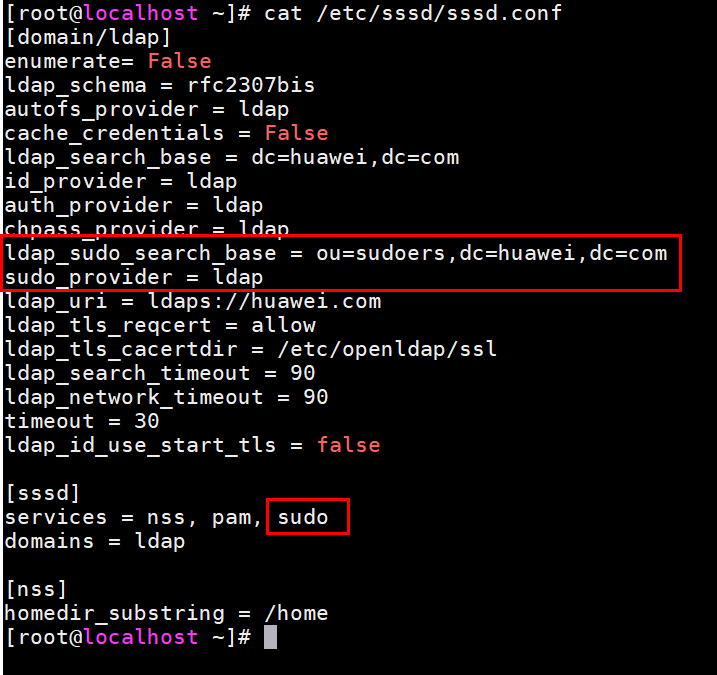
- Modify the following information in bold in the /etc/sssd/sssd.conf file:
[domain/ldap] enumerate= False ldap_schema = rfc2307bis autofs_provider = ldap cache_credentials = False ldap_search_base = dc=huawei,dc=com id_provider = ldap auth_provider = ldap chpass_provider = ldap ldap_sudo_search_base = ou=sudoers,dc=huawei,dc=com sudo_provider = ldap ldap_uri = ldaps://huawei.com ldap_tls_reqcert = allow ldap_tls_cacertdir = /etc/openldap/ssl ldap_search_timeout = 90 ldap_network_timeout = 90 timeout = 30 ldap_id_use_start_tls = false [sssd] services = nss, pam, sudo domains = ldap [nss] homedir_substring = /home
Result:

Modify the fields such as domains in the [domain/ldap] and sssd as needed.
- Clear the SSSD cache and restart the SSSD service.
systemctl stop sssd sss_cache -E systemctl restart sssd
- Add the following configuration to /etc/nsswitch.conf so that the SSSD service can manage sudoers configurations:
- Verify sudo commands.
- Log in using an OpenLDAP user (for example, test1) and run sudo -l. Expected result:
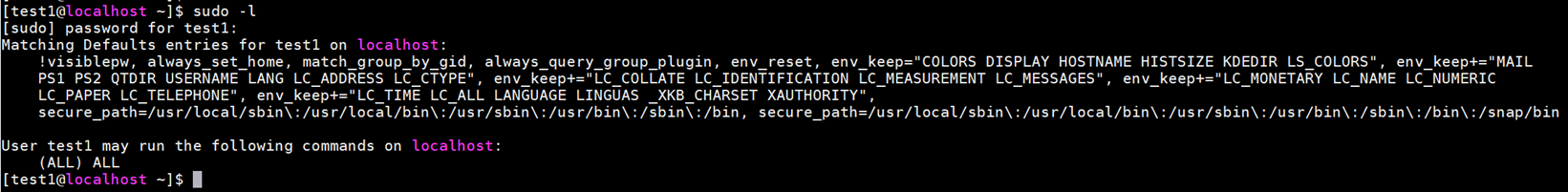
- Log in using an OpenLDAP user (for example, test1) and run sudo -l. Expected result:
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





