DCS Data Security
Security is a shared responsibility between Huawei Cloud and you. Huawei Cloud is responsible for the security of cloud services to provide a secure cloud. As a tenant, you should properly use the security capabilities provided by cloud services to protect data, and securely use the cloud. For details, see Shared Responsibilities.
This section provides actionable guidance for enhancing the overall security of using DCS. You can continuously evaluate the security status of your DCS resources, enhance their overall security defense by combining multiple security capabilities provided by DCS, and protect data stored in DCS from leakage and tampering both at rest and in transit.
Make security configurations from the following dimensions to meet your service needs.
- Protecting Data Through Access Control
- Encrypting Data Before Storage
- Data Restoration and Disaster Recovery
- Transmission Encryption with SSL
- Checking for Abnormal Data Access
- Using the Latest SDKs for Better Experience and Security
- Using Other Cloud Services for Additional Data Security
Protecting Data Through Access Control
Correctly use the access control capability provided by DCS to prevent your data from being stolen or damaged.
- Set only the minimum permissions for IAM users with different roles to prevent data leakage or misoperations caused by excessive permissions.
To better isolate and manage permissions, you are advised to configure an independent IAM administrator and grant them the permission to manage IAM policies. The IAM administrator can create different user groups based on your service requirements. User groups correspond to different data access scenarios. By adding users to user groups and binding IAM policies to user groups, the IAM administrator can grant different data access permissions to employees in different departments based on the principle of least privilege. For details, see Permissions Management.
- Configure a whitelist or security group to protect your data from abnormal reads or other operations.
By configuring an IP address whitelist or inbound and outbound security group rules, you can control the network range for connecting to your instance and prevent exposure to untrusted third parties.
DCS Redis 4.0 and later basic edition instances are controlled by whitelists. For details, see Managing IP Address Whitelist.
Enterprise edition DCS Redis 6.0 instances are controlled by security group rules. For details, see How Do I Configure a Security Group? Do not set the source to 0.0.0.0/0 in the inbound rules of a security group.
- Do not use high-risk commands, to prevent attackers from directly damaging Redis.
You can rename high-risk commands to disable them if they are not used in your service. Learn more about disabled commands and commands that can be renamed.
- Use a non-default port to prevent scanning attacks.
The default listening port of the Redis server is 6379, which is vulnerable to scanning attacks. You can use a port in the range from 1 to 65535. For details, see Customizing a Port.
- Limit the maximum number of client connections to avoid resource exhaustion and DoS risks.
The maxclients parameter of Redis determines the maximum number of clients that can be concurrently connected to an instance. The default value is 10000, and the value can range from 1000 to 50000. Excess connection requests will be rejected.
Set a proper client connection limit based on your application scenario. For details about how to modify the maxclients parameter, see Modifying Configuration Parameters.
- Limit the idle time of Redis connections based on service requirements.
To prevent idle client connections from occupying resources for a long time, you can set the timeout parameter on the console. Client connections that remain idle for the period specified by this parameter will be closed. The default value of timeout is 0, indicating that the server does not proactively disconnect idle clients. The value ranges from 0 to 7200, in seconds.
You are not advised to set it to 0. For example, you can set it to 3,600 seconds. For details about how to modify the timeout parameter, see Modifying Configuration Parameters.
- Configure a password for accessing your DCS instance to prevent unauthorized clients from operating it by mistake. In this way, clients can be authenticated for access, improving instance security.
You can set a password when buying an instance, or reset the password of an existing instance.
- Configure ACL permissions for your DCS instance.
As a DCS administrator, you can create read-only accounts and read/write accounts for DCS instances to implement refined access control in different service scenarios.
Figure 1 Instance ACL user management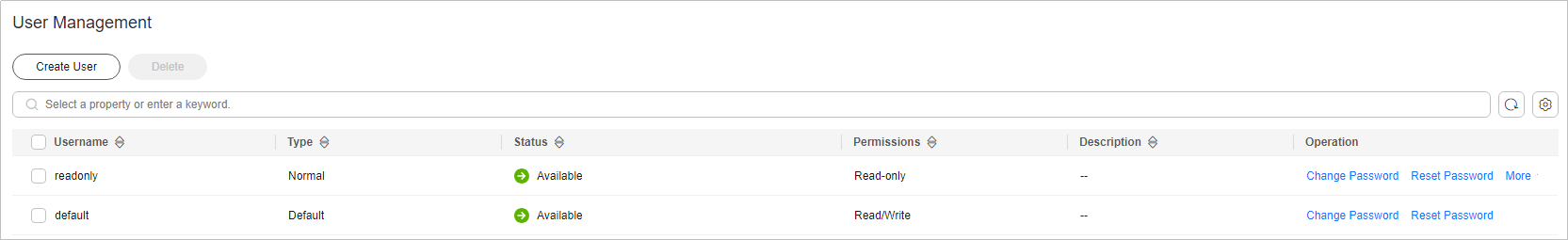
- Use different DCS instances for different services to prevent instance faults from affecting multiple services.
Encrypting Data Before Storage
RDB and AOF persistent files in open-source Redis do not support encryption. Therefore, DCS does not support data encryption. If you have sensitive data, please encrypt it before writing it to DCS.
Data Restoration and Disaster Recovery
Build restoration and disaster recovery (DR) capabilities in advance to prevent data from being deleted or damaged by mistake in abnormal data processing scenarios.
- Enable automated instance backup to quickly restore data in abnormal scenarios.
DCS instances can be backed up automatically or manually. The automated backup function is disabled by default. After it is enabled, you can restore backup data to the instance. Backup data of an instance is stored for a maximum of 7 days. For details about automated backup, see Configuring a Backup Policy.
Manual backups are user-initiated full backups of instances. The backup data is stored in Huawei Cloud OBS buckets and removed upon deletion of the corresponding instance.
- Use cross-AZ replication for data DR.
A master/standby or cluster DCS instance can be deployed within an AZ or across multiple AZs for HA. For cross-AZ deployment, DCS initiates and maintains data synchronization. High availability is achieved by having a standby node take over in the event that a failure occurs on the master node. When operations are read-heavy, you can use DCS Redis 4.0 or later instances that support read/write splitting, or cluster instances that have multiple replicas. DCS maintains data synchronization between the master and replicas. You can connect to different addresses of an instance to isolate read and write operations.
Figure 2 Selecting a primary and standby AZ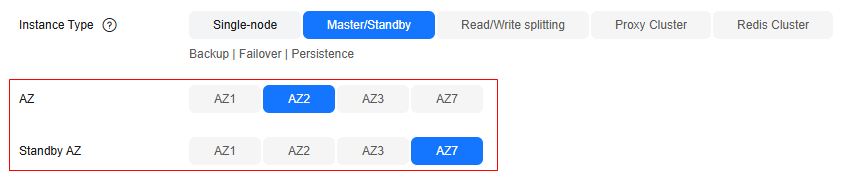
For cross-AZ deployment, DCS initiates and maintains data synchronization. High availability is achieved by having a standby node take over in the event that a failure occurs on the master node.
Transmission Encryption with SSL
To prevent data from being stolen or damaged during transmission, use SSL encryption to access DCS.
Currently, only DCS for Redis 6.0/7.0 basic edition supports SSL encryption. You are advised to use DCS Redis 6.0/7.0 basic edition instances and enable SSL for them. For details, see Transmitting DCS Redis Data with Encryption Using SSL

Checking for Abnormal Data Access
- Enable Cloud Trace Service (CTS) to record all DCS access operations for future audit.
CTS records operations on the Huawei Cloud resources in your account. You can use the logs generated by CTS to perform security analysis, track resource changes, audit compliance, and locate faults.
After you enable CTS and configure a tracker, CTS can record management and data traces of DCS for auditing. For details, see Viewing DCS Audit Logs .
- Use Cloud Eye for real-time monitoring and alarm reporting on security events.
When using DCS, you may encounter error responses from the server. Huawei Cloud provides the Cloud Eye service to automatically monitor your DCS instances in real time, generate alarms, and send notifications, so that you can learn about the requests, traffic, and error responses of your DCS instances in real time.
Cloud Eye is enabled automatically after you create a DCS instance. For details, see DCS Metrics and Configuring DCS Monitoring and Alarms.
Using the Latest SDKs for Better Experience and Security
Upgrade SDKs to the latest version to better protect your data and DCS usage. Download the latest SDK in your desired language from SDK Overview.
Using Other Cloud Services for Additional Data Security
Ensuring DCS resource security using SecMaster
SecMaster provides you with built-in checks that are included in Cloud Security Compliance Check 1.0, DJCP 2.0 Level 3 Requirements, and Network Security, to check key configurations of DCS, generate alarms for configurations with security risks, and provide hardening suggestions and guidelines. You can use the resource management function of SecMaster to quickly learn about the DCS security status and locate security risks. For details, see Baseline Inspection Overview.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





