Cross-Cloud, Cross-VPC O&M for Resources On and Off the Cloud
Application Scenarios
If you have servers deployed across VPCs, in on-premises data centers, and across multiple clouds, CBH is always a good choice for centralized O&M. With CBH, you can manage scattered servers centrally without establishing dedicated lines, making O&M of all workloads efficiently and securely.
This topic describes how to use the CBH system to manage and maintain your resources across VPCs, clouds, and on-premises environments. Before doing this, you need to enable communications between your CBH instance and the network where the resources to be managed with CBH locate. The following walks you through how to configure a proxy server in a target network and connect the proxy server to a CBH system.
Prerequisites and Preparations
- Your CBH instance is running properly.
- You have purchased an ECS, and the ECS is running properly.
- You have obtained a server from the peer network domain as the proxy server.
- An EIP has been bound to the proxy server. For details, see Binding an EIP to an Instance.
- The proxy server can communicate with the servers you want CBH to manage.
- You have downloaded the latest version 3proxy package.
Setting the Proxy Server
Before managing and maintaining servers across network domains, you need to configure a network proxy server in the peer network domain. Then connect the proxy server to service servers through the intranet, and connect the proxy server to the CBH network. In this way, the CBH system can communicate with the service servers across domains.
This operation is the prerequisite for a bastion host to manage host resources across networks.
- Enabling the Network Proxy Service for the Proxy Server
- Log in to the proxy server and set the proxy server (assume it is named 3proxy).
The commands in Step 2 to Step 4 are based on CentOS 7. For details about example commands for CentOS 8, see Example for Configuring a Proxy for CentOS 8.
- Upload and decompress the 3proxy package, go to the corresponding directory, and run the following command:
bash install.sh
- Enter the following command to add the 3proxy user:
/etc/3proxy/add3proxyuser.sh myuser mypassword
- Restart the proxy service 3proxy.
systemctl restart 3proxy
- The SOCKS5 proxy protocol (port: 1080) does not provide the encryption function. If an unencrypted protocol is used for O&M through the proxy server, disable access from unnecessary IP addresses in the security group settings.
- If encrypted transmission or data security is required, you can select an encrypted protocol when selecting an inbound or outbound rule. The protocol can be SSH, RDP, SFTP, SCP, or Rlogin.
- Configuring Security Group Rules for the Proxy Server
- Configure inbound rules to allow the bastion host to access the proxy server.
Figure 1 Inbound rule configuration
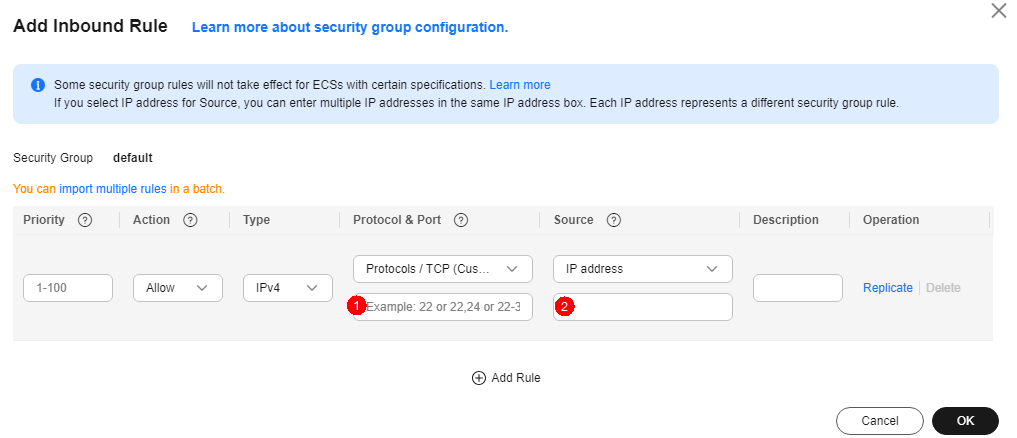
- Set Protocol & Port to the default port 1080 for the SOCKS5 proxy server.
- Enter the IP address of the bastion host in the Source text box.
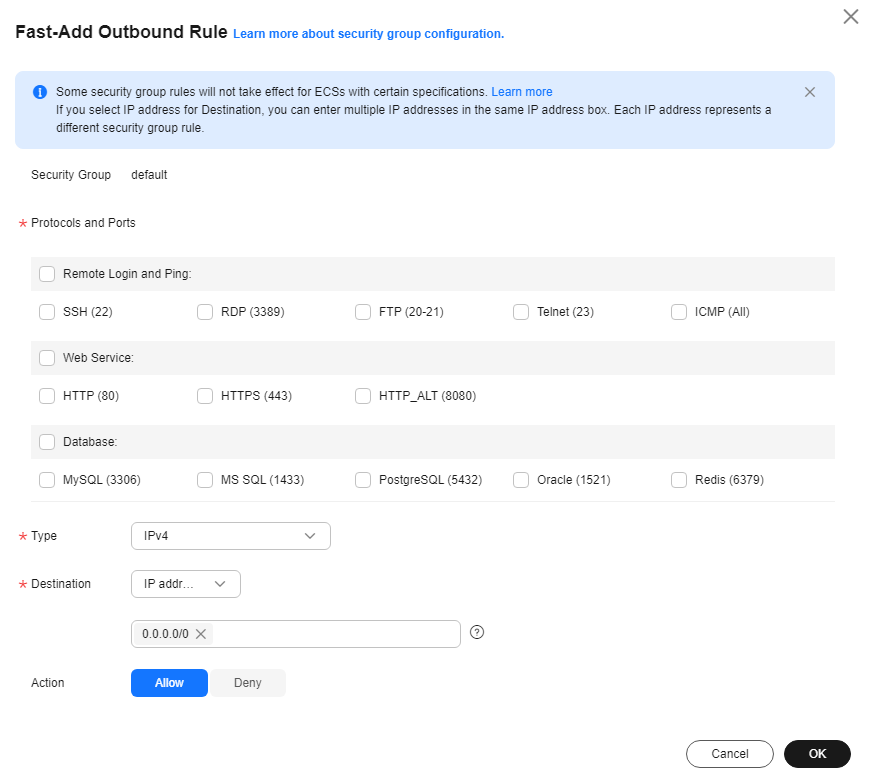
- Configure outbound rules for the proxy server to allow the proxy server to access the service servers managed with CBH.
Figure 2 Outbound rule configuration
Using CBH to Manage Cross-Domain Service Servers
- Log in to the network console and choose Access Control > Security Groups. On the Security Groups page, configure the inbound and outbound rules of the security group associated with the CBH instance.
Figure 3 Configuring an inbound rule for a CBH instance
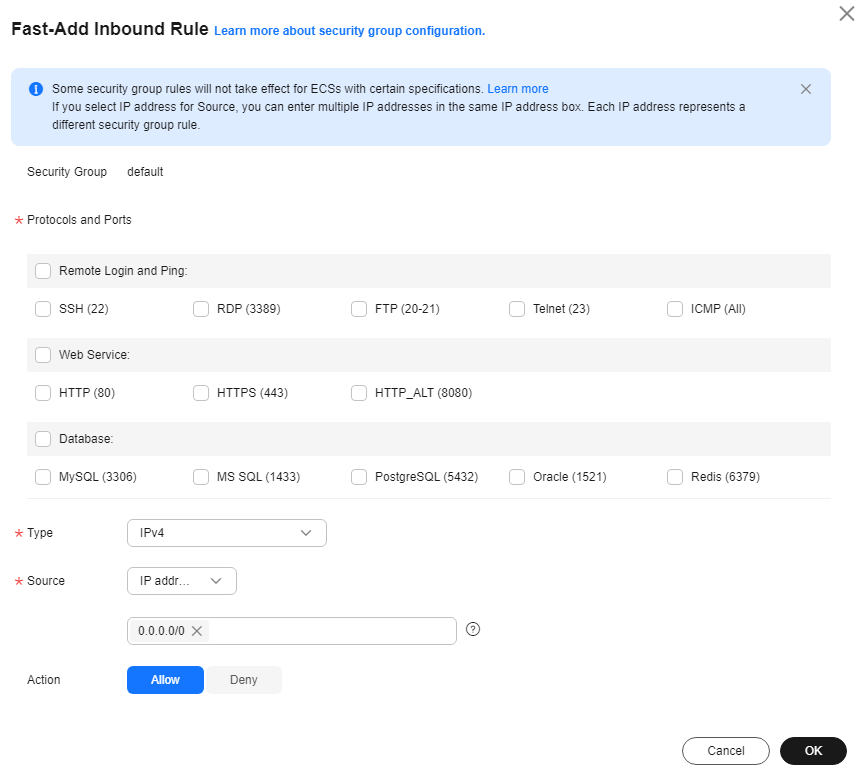 Figure 4 Configuring an outbound rule for a CBH instance
Figure 4 Configuring an outbound rule for a CBH instance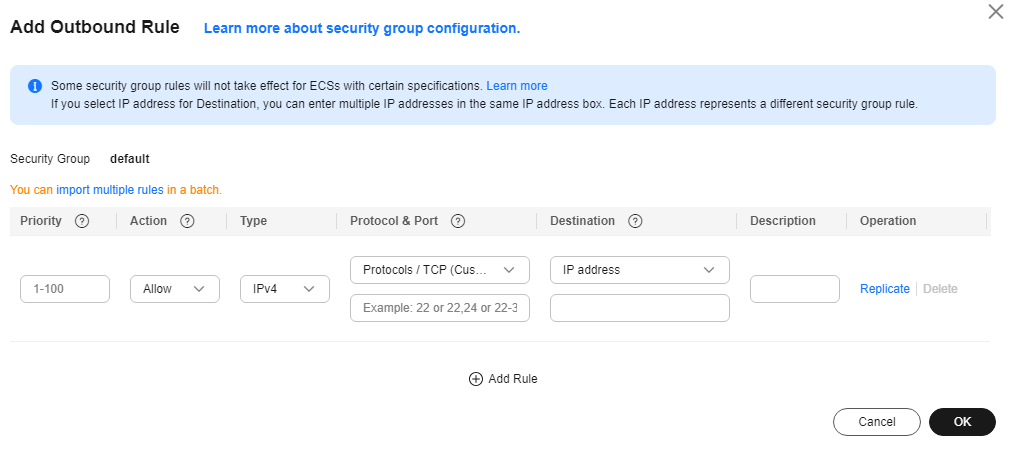
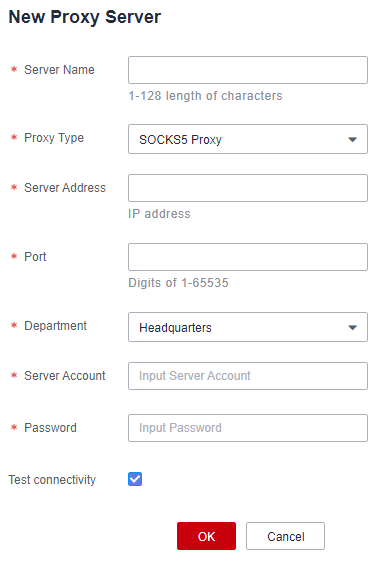
- Use CBH to manage proxy servers. Log in to the CBH system and add the proxy server. For details, see Adding a Host. On the Host page, click the Proxy Server tab and then New.
Figure 5 New Proxy Server
- Go back to the security group (the one you select in 1) your service servers belong to. On the Inbound Rules tab, click Fast-Add Rule.
You can also add some outbound rules as required.
- Use CBH to manage service servers. For details, see Adding Hosts.
Figure 6 New Host
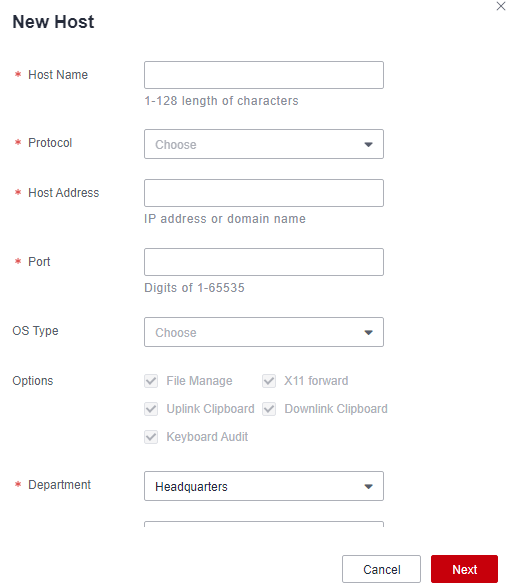
After the preceding operations are performed, you can perform O&M on the managed hosts across network domains using the host operation function in CBH. Similarly, the preceding methods can be applied to different network environments such as hybrid/heterogeneous clouds and offline IDCs to implement unified online and offline O&M across clouds and VPCs.
Example for Configuring a Proxy for CentOS 8
- Run the following command to install the 3proxy software package:
yum install -y epel-release
yum install -y 3proxy
- Run the following command to perform simplified configuration:
nscache 65536
timeouts 1 5 30 60 180 1800 15 60
# Set the username. Enter the username after the users command. Enter the username after the CL command. This section uses test as an example.
users test:CL:test
daemon
log /var/log/3proxy/3proxy.log
logformat "- +_L%t.%. %N.%p %E %U %C:%c %R:%r %O %I %h %T"
archiver gz /bin/gzip %F
rotate 30
external 0.0.0.0
internal 0.0.0.0
auth strong
allow test
maxconn 20
socks
flush
- Start the service.
systemctl start 3proxy
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





