Possible Causes of Sidecar Injection Failures
Common scenarios and solutions:
- Possible cause: The number of pods managed by a service mesh has reached the limit, so no more sidecars can be injected.
Check method: Check whether the number of pods injected into the service mesh reaches the limit.
Log in to the ASM console and check whether the number of pods displayed in your service mesh card reaches the service mesh scale. If yes, the number of pods injected to the service mesh has reached the limit.
Solution: Contact O&M engineers or submit a service ticket.
- Possible cause: The control plane component istiod is abnormal.
Check method: Check whether the istiod component in the istio-system namespace is abnormal.
Log in to the CCE console and click the cluster name to go to the cluster console. In the navigation pane, choose Workloads. Then, select the istio-system namespace, and check whether the status of istiod-1-18-7-r4 is Running in the Status column. If the status is not Running, the component may be abnormal.

1-18-7-r4 indicates the service mesh version. The service mesh version is specified by Version on the Basic Information tab (Mesh Configuration > Basic Information). The displayed version number here is combined with hyphens (-).
Solution: If the component is abnormal, contact O&M engineers or submit a service ticket.
- Possible cause: The automatic injection label is not added to the namespace.
Check method: Run the following command to view the webhook's namespaceSelector:
kubectl get mutatingwebhookconfiguration istio-sidecar-injector-1-18-7-r4 -o yaml | grep "rev.namespace.sidecar-injector.istio.io" -A20 | grep "namespaceSelector:" -A7

Replace 1-18-7-r4 in the preceding command with the service mesh version in the current format (combined with hyphens). The service mesh version is specified by Version on the Basic Information tab (Mesh Configuration > Basic Information).
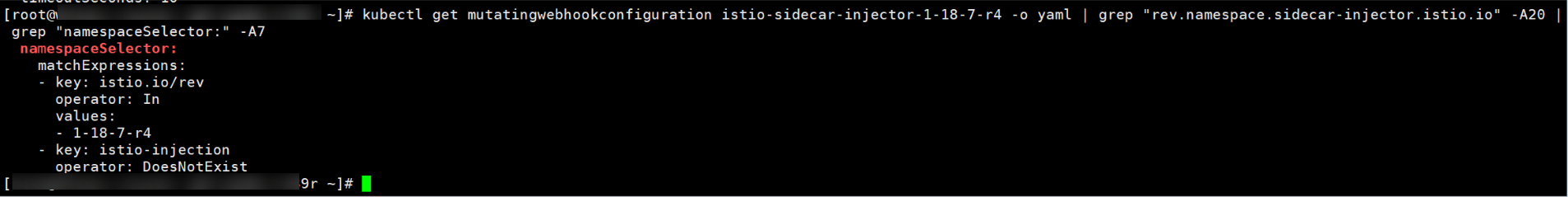
For example, the command output in the preceding figure indicates that the istio.io/rev=1-18-7-r4 label is required and the istio-injection label is not allowed.
Run the following command to check whether the target namespace is included in the webhook:
kubectl get {namespace} --show-labelsSolution: Add the obtained injection label to the namespace.
- Possible cause: The default injection policy is not set to enabled for the namespace.
Check method: Run the following command to check the default policy, and ensure that the policy value is enabled.
kubectl -n istio-system get configmap istio-sidecar-injector-1-18-7-r4 -o jsonpath='{.data.config}' | grep policy:
Replace 1-18-7-r4 in the preceding command with the service mesh version in the current format (combined with hyphens). The service mesh version is specified by Version on the Basic Information tab (Mesh Configuration > Basic Information).
Solution: Refer to How Do I Enable Namespace Injection for a Cluster?
- Possible cause: There is the sidecar.istio.io/inject: 'false' label.
Check method: Check the workload label.
Log in to the CCE console and click the cluster name to go to the cluster console. In the navigation pane, choose Workloads. Then, select the corresponding namespace, locate your workload, and choose More > View YAML in the Operation column. Find the spec.template.metadata.labels field and ensure that the sidecar.istio.io/inject: 'false' label does not exist.

Replace 1-18-7-r4 in the preceding command with the service mesh version in the current format (combined with hyphens). The service mesh version is specified by Version on the Basic Information tab (Mesh Configuration > Basic Information).
Solution: If there is the sidecar.istio.io/inject: 'false' label, delete it. For details, see How Do I Disable Sidecar Injection for Some Workloads?
- Possible cause: The pod cannot be created.
Solution: Run the following command to check the error information and rectify the fault based on the error information:
kubectl describe -n {namespace} {deployment name} - Possible cause: Ensure that your pod is not in the kube-system or kube-public namespace.

Automatic sidecar injection will be ignored for pods in these namespaces.
- Possible cause: Ensure that the pod specification does not contain hostNetwork: true.

Automatic sidecar injection will be ignored for pods with hostNetwork: true.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





