Adding an Application
Scenarios
If your applications support SAML 2.0, you can associate your applications with IAM Identity Center through SAML 2.0 and use IAM Identity Center to manage user access to those applications. You can set additional SAML attribute mappings for an application that requires identity federation in IAM Identity Center. IAM Identity Center uses these mappings to populate SAML 2.0 assertions for your application.
This section describes how to set up a SAML 2.0 trust relationship between IAM Identity Center and your application.
Prerequisites
You have obtained the certificate and metadata required by the application for trust verification.
Procedure
- Log in to the Huawei Cloud management console.
- Click
 in the upper left corner of the page and choose Management & Governance > IAM Identity Center.
in the upper left corner of the page and choose Management & Governance > IAM Identity Center. - In the navigation pane, choose Applications.
- Click Add Application in the upper right corner.
- On the displayed page, set Display Name and Description for the application. The description does not appear on the user portal. It will only be visible in the IAM Identity Center console and when IAM Identity Center APIs are called.
Figure 1 Setting the name and description

- Configure IAM Identity Center as an identity provider in either of the following ways. For details, see the description of the application to be interconnected.
- Click Download Metadata File to download the metadata of IAM Identity Center. Configure the metadata of IAM Identity Center in your application.
Figure 2 Downloading metadata

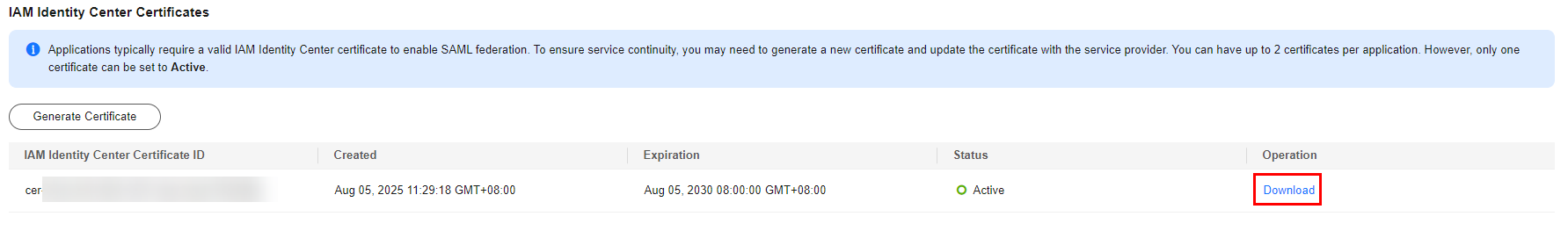
- Locate the target certificate and click Download in the Operation column and then configure this certificate in your application.
Figure 3 Downloading the certificate
- Click Download Metadata File to download the metadata of IAM Identity Center. Configure the metadata of IAM Identity Center in your application.
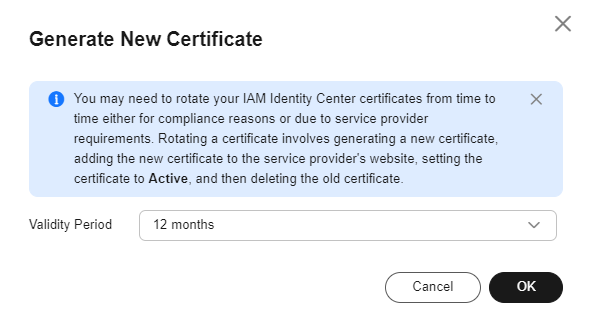
- (Optional) If you do not need the default certificate (valid for five years), click Generate Certificate and select a certificate validity period ranging from 6 months to 60 months. Then, click OK.
Figure 4 Generating a new certificate
- Configure the application metadata. IAM Identity Center requires specific application metadata to trust this application.
- If you already have a metadata file, select Upload application SAML metadata file and click Add to upload the file.
- If you do not have a metadata file, select Manually enter your metadata values and enter the application ACS URL and the SAML audience.
- (Optional) Configure application properties.
- Application Startup URL: You use an application startup URL to start the federation process with your application. The typical use is for an application that supports only SP-initiated binding.
For example, a user's browser redirects the authentication request using the value of the application startup URL. The application sends an HTML POST with a SAMLRequest to IAM Identity Center. IAM Identity Center then sends an HTML POST with a SAMLResponse back to the application.
- Relay State: During the federation authentication, the relay state redirects users within the application. For SAML 2.0, this value is passed to the application as it is. After the application properties are configured, IAM Identity Center sends the relay state value along with a SAML response to the application.
- Session Duration: Session duration is the length of time for which an application user session is valid. The duration ranges from 1 hour to 12 hours.
- Application Startup URL: You use an application startup URL to start the federation process with your application. The typical use is for an application that supports only SP-initiated binding.
- Click OK. The configured application is displayed in the list, and the application status is Active.
If the application configuration is not completed, the task remains in the list and the application's status is Incomplete.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





