Configuring Security Settings
To ensure system security, the security administrator can configure the security settings of platform login, account, and network access.
Procedure
- Log in to a database encryption and access control instance as the secadmin user.
- In the navigation tree on the left, choose System Management > System Settings.
- In the Platform Login Security Settings area, configure the parameters.
Figure 1 Platform login security settings
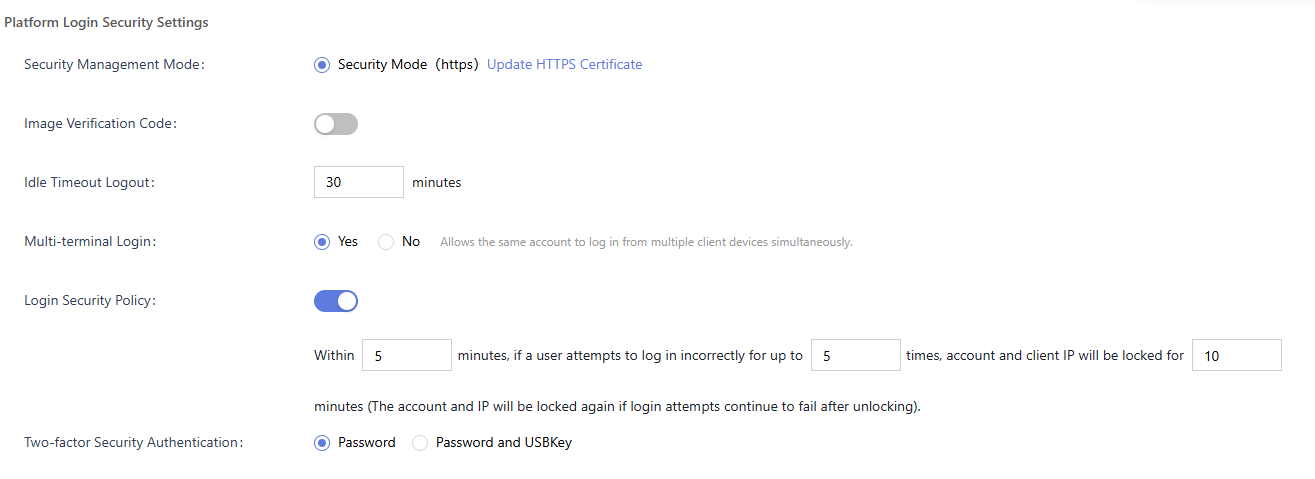
Table 1 Parameters of platform login security settings Parameter
Description
Security Management Mode
HTTPS security mode is supported with updatable certificates.
Image Verification Code
- You can choose whether to enable this function.
- Once enabled, an image verification code is required for system login to prevent brute-force attacks.
Idle Timeout Logout
Set the automatic logout interval.
Multi-terminal Login
You can choose whether to enable this function.
- Yes: An account can be logged in at different places.
- No: An account cannot be logged in at different places.
Login Security Policy
- You can choose whether to enable this function to prevent brute-force attacks.
- For example, if the login information is incorrect for three consecutive times within 3 minutes, the account is locked for 5 minutes.
Two-factor Security Authentication
Configure the login authentication mode.
- Password: Only password is required for login.
- Password and USBKey: You need to enter the password and insert the USBKey with the certificate to the device.
- In the Account and Password Security Settings area, set the password validity period.
- In the Network Access Security Settings area, set the access restrictions.
Figure 2 Network access security settings
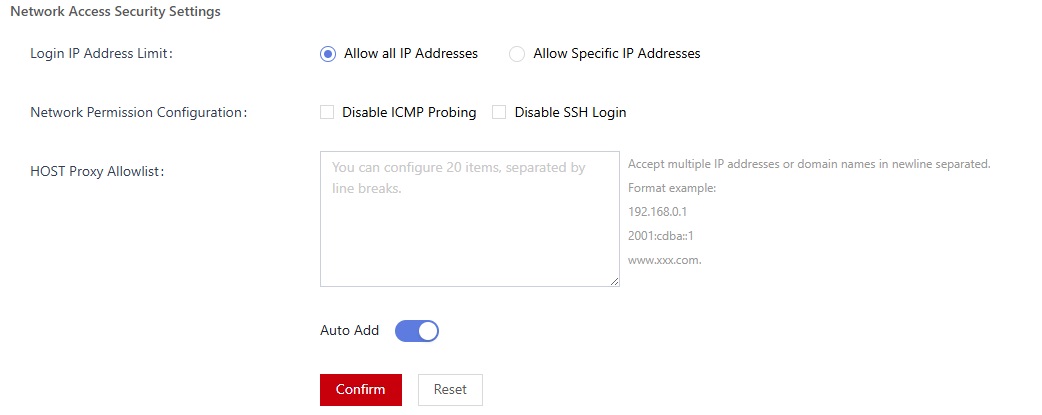
Table 2 Parameters of network access security settings Parameter
Description
Login IP Address Limit
Whether to restrict the access source.
- Accept All IP Addresses: All IP addresses can access the system.
- Allow Specific IP Addresses: Only IP addresses in the allowlist can access the console of database encryption and access control.
Allowed Login IP Addresses
Enter the allowed IP addresses and separate them with line breaks.
Network Permission Configuration
You choose whether to disable ICMP probing and SSH login.
- Disable ICMP Probing: If you enable this function, other devices cannot ping the system.
- Disable SSH Login: SSH login is disabled.
NOTE:If Disable SSH Login is enabled, O&M engineers cannot access the server background through SSH.
Host Proxy Whitelist
Enter the host proxy whitelist. The value can be an IP address or a domain name.
- Click Confirm.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





