Yearly/Monthly Billing
Yearly/Monthly billing is a prepaid billing mode in which you pay before using resources. It is suitable when your resource requirements are fixed because you can pay less by using longer. In the yearly/monthly billing mode, we offer discounts to you. This topic describes the billing rules of yearly/monthly SecMaster resources.
Application Scenarios
In yearly/monthly billing mode, you need to pay for a required duration in advance. This mode is suitable for long-term and relatively fixed service requirements. The yearly/monthly billing mode is recommended for the following scenarios:
- Long-term workloads with stable resource requirements, such as official websites, online malls, and blogs.
- Long-term projects, such as scientific research projects and large-scale events
- Workloads with predictable traffic bursts, for example, e-commerce promotions or festivals.
- Workloads with high data security requirements
Billing Items
The following billing items support yearly/monthly billing:
|
Billing Item |
Description |
|
|---|---|---|
|
Edition |
SecMaster edition, including basic, standard, and professional editions. |
|
|
Quota |
The quantity of the ECS quota. |
|
|
Value-added package |
Large screen |
If you have purchased a yearly/monthly SecMaster edition, the large screen service you buy separately is also billed on a yearly/monthly basis. |
|
Log audit |
If you have purchased a yearly/monthly SecMaster edition, the security data collection and retention services you buy separately are also billed on a yearly/monthly basis. |
|
|
Security analysis |
If you have purchased a yearly/monthly SecMaster edition, the security analysis package you buy separately is also billed on a yearly/monthly basis. |
|
|
Security orchestration |
If you have purchased a yearly/monthly SecMaster edition, the security orchestration service you buy separately is also billed on a yearly/monthly basis. |
|
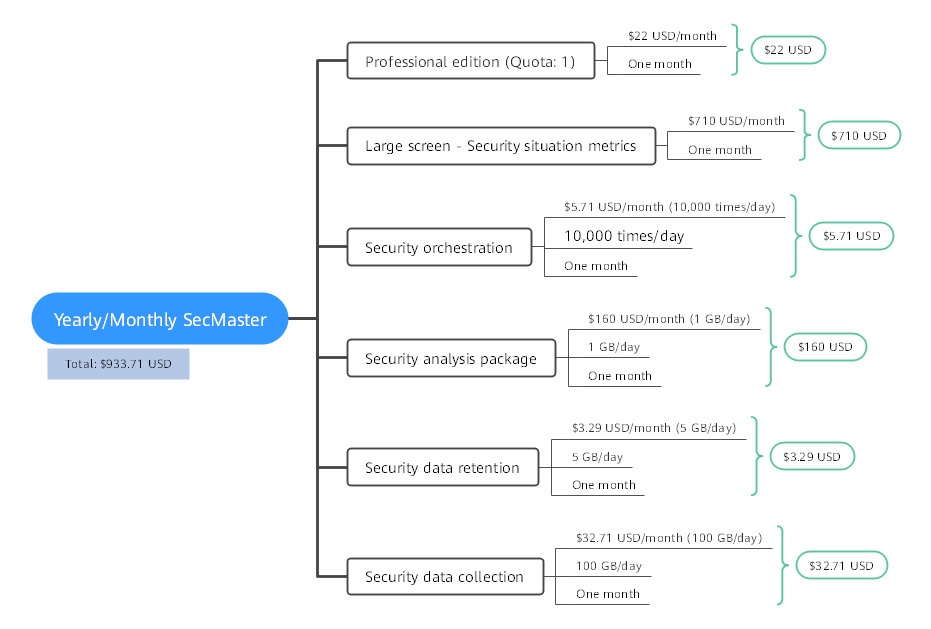
If you plan to purchase the professional edition SecMaster with one quota, as well as the large screen, security data collection (5 GB/month), security data retention (100 GB/month), security analysis (1 GB/day), security orchestration (10,000 operations/day), and select the yearly/monthly billing mode (the required duration is one month), at the bottom of the SecMaster purchase page, you can view the fee details.
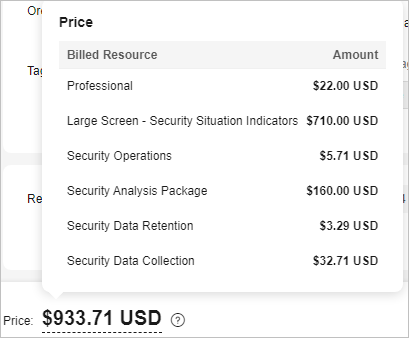
The price includes:
- Professional edition: the fees for the professional edition and the quota you specify.
- Large screen - security situation metrics: the fee for SecMaster large screen.
- Security orchestration: the fee for the playbooks execution quota you specify.
- Security analysis package: the fee for security analysis data volume you specify.
- Security data collection: the fee for daily data collection volume you specify.
- Security data retention: the fee for daily log retention volume you specify.
Billing Period
The billing period of yearly/monthly SecMaster is determined by the required duration (UTC+8:00). The billing period starts from the time you activate or renew your subscription (precise to seconds), and ends at 23:59:59 on the expiration date.
For example, if you purchase the SecMaster professional edition with one quota for one month at 15:50:04 on June 30, 2024 (no value-added package is purchased), the billing period is from 15:50:04 on June 30, 2024 to 23:59:59 on July 30, 2024.
Billing Examples
Assume that you purchased a yearly/monthly SecMaster professional edition (Quota: 1) at 15:50:04 on June 30, 2024, as well as the value-added package, including large screen, security data collection (5 GB/month), security data retention (100 GB/month), security analysis (1 GB/day), and security orchestration (10,000 operations/day). Billing resources include the professional edition, quota, and value-added package. Your subscription is one month and you manually renew the subscription for another month before the subscription expires. The billing details are as follows:
- The first billing period is from 15:50:04 on June 30, 2024 to 23:59:59 on July 30, 2024.
- The second billing period is from 23:59:59 on July 30, 2024 to 23:59:59 on Aug. 30, 2024.
You must prepay for each billing period. Table 2 shows the billing formula.
|
Resource Type |
Billing Formula |
|---|---|
|
Service edition + Quota |
(Service edition + Quota) x Required duration |
|
Security data collection |
Security data collection package price x Required duration |
|
Security data retention |
Security data retention package price x Required duration |
|
Large screen |
Large screen - Security situation metric price x Required duration |
|
Security analysis |
Price of security analysis data volume per day x Required duration |
|
Security orchestration |
Number of execution times of workflow nodes (including the start and end nodes, but excluding judgment nodes) per day during playbook execution x Required duration |
Figure 2 shows how the price is calculated.
Impact on Billing After Specification Changes
If you change the current specifications of your yearly/monthly SecMaster to meet your service changes, the following pricing rules are used:
Upgrading the edition or specifications: You need to pay the price difference.
Increasing the quota: You need to pay the price difference.
Currently, SecMaster does not support changing the edition in use to a one with lower specifications. If you want to use SecMaster of an earlier edition, unsubscribe from the one you are using first and subscribe to the one you want.
Assume that you purchased the standard yearly/monthly SecMaster (ECS quota: 1) edition for one month on June 8, 2024 without any discount and you changed SecMaster to the professional edition on June 18, 2024. The price of the old configuration is $2.2 USD/month, and that of the new configuration is $22 USD/month. The formula is as follows:
Specification upgrade fee = New specification price × Remaining period - Old specification price × Remaining period
The remaining period in the formula is the remaining days of each calendar month divided by the maximum days of corresponding calendar month. In this example, the remaining period = 12 (Remaining days in June)/30 (Maximum number of days in June) + 8 (Remaining days in July)/31 (Maximum number of days in July) = 0.6581. Price difference = 22 x 0.6581 – 2.2 x 0.6581 = $13.03 USD
For more information, see Pricing of a Changed Specification.
Impacts of Expiration
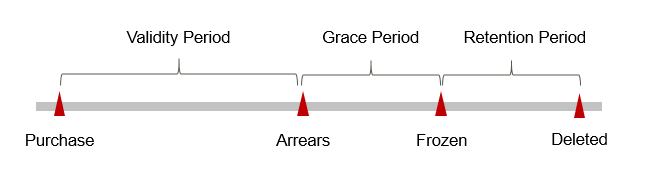
Figure 3 describes the status of yearly/monthly SecMaster resources in each phase. After you buy a resource, it enters the valid period and runs normally during this period. If the resource is not renewed after it expires, before being deleted, it first enters a grace period and then a retention period.
Expiration reminder
The system will send expiration reminders to you before your yearly/monthly SecMaster resources expire. to the creator of the account by email, SMS, and internal message.
- For a yearly subscription, a reminder will be sent 30 days, 15 days, 7 days, 3 days, and 1 day before the resource expires.
- For a monthly subscription, a reminder will be sent 15 days, 7 days, 3 days, and 1 day before the resource expires.
Impact of expiration
If your yearly/monthly SecMaster resources expire and are not renewed, the resources enter the grace periods. During the grace period, you can use the SecMaster service.
If you do not renew your yearly/monthly SecMaster before the grace period ends, it goes into the retention period and its status turns to Frozen. You cannot perform any operations on such instances in the retention period.
For details, see Retention Period.
If the yearly/monthly SecMaster resources are still not renewed after the grace period ends, the SecMaster resources will be released, and data cannot be restored.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot