Route Table and Route Overview
What Is a Route Table?
A route table contains a set of routes that are used to control the traffic in and out of your subnets in a VPC. Each subnet must be associated with a route table. A subnet can only be associated with one route table, but a route table can be associated with multiple subnets.
There are default route tables and custom route tables. You can add IPv4 and IPv6 routes to them.

- Default route table: Each VPC comes with a default route table. If you create a subnet in a VPC, the subnet is automatically associated with the default route table. The default route table ensures that subnets in a VPC can communicate with each other.
- You can add routes to, delete routes from, and modify routes in the default route table, but cannot delete the table.
- When you create a VPC endpoint, VPN, or Direct Connect connection, the default route table automatically delivers a route that cannot be deleted or modified.
- Custom route table: If you do not want to use the default route table, you can create a custom route table and associate it with the subnet. Custom route tables can be deleted if they are no longer required.
The custom route table of a subnet only controls outbound traffic. The default route table of the VPC that the subnet belongs to controls inbound traffic, for example, traffic from VPC peering connections, Direct Connect, and VPN connections to the VPC.
By default, there is no quota for custom route tables. To create custom route tables, apply for a quota increase first.
Route
You can add routes to both default and custom route tables and configure the destination, next hop type, and next hop for the routes to determine where network traffic is directed. Routes are classified into system routes and custom routes.
- System route: A system route is automatically added by the VPC service or other services (such as VPN and Direct Connect) and cannot be deleted or modified.
Each route table comes with routes whose next hops are Local. Table 1 shows details about local routes.
Table 1 Local routes Local Route Destination
Destination Description
100.64.0.0/10
Used by public services on the cloud. This local route allows instances in a subnet to access public services on the cloud, such as the DNS servers.
198.19.128.0/20
Used by internal services, such as VPC Endpoint.
127.0.0.0/8
Provides local loopback addresses.
Subnet CIDR block
Subnet CIDR block in a VPC. This local route allows different subnets in the VPC to communicate with each other.
When you create a subnet, you can specify an IPv4 CIDR block for the subnet. If you select IPv6 CIDR Block when creating a subnet, the system automatically assigns an IPv6 CIDR block to the subnet. Then, you can view IPv6 routes in its route table. The following are examples:- IPv4 CIDR block of a subnet: 192.168.2.0/24
- IPv6 CIDR block of a subnet: 2407:c080:802:be7::/64
- Custom route: After a route table is created, you can add custom routes and configure information such as the destination and next hop in the route to determine where network traffic is directed. In addition to manually added custom routes, there are custom routes added by other cloud services, such as Cloud Container Engine (CCE) or NAT Gateway.
Route tables include default route tables and custom route tables. They support the next hop types described in Table 2 and Table 3.
Table 2 Next hop types supported by the default route table Next Hop Type
Description
Server
Traffic intended for the destination is forwarded to an ECS in the VPC.
Extension NIC
Traffic intended for the destination is forwarded to the extended network interface of an ECS in the VPC.
NAT gateway
Traffic intended for the destination is forwarded to a NAT gateway.
VPC peering connection
Traffic intended for the destination is forwarded to a VPC peering connection.
Virtual IP address
Traffic intended for the destination is forwarded to a virtual IP address and then sent to active and standby ECSs to which the virtual IP address is bound.
VPC endpoint
Traffic intended for the destination is forwarded to a VPC endpoint.
Cloud container
Traffic intended for the destination is forwarded to a cloud container.
Enterprise router
Traffic intended for the destination is forwarded to an enterprise router.
Cloud firewall
Traffic intended for the destination is forwarded to a cloud firewall.
Table 3 Next hop types supported by a custom route table Next Hop Type
Description
Server
Traffic intended for the destination is forwarded to an ECS in the VPC.
Extension NIC
Traffic intended for the destination is forwarded to the extended network interface of an ECS in the VPC.
BMS user-defined network
Traffic intended for the destination is forwarded to a BMS user-defined network.
Direct Connect gateway
Traffic intended for the destination is forwarded to a Direct Connect gateway.
NAT gateway
Traffic intended for the destination is forwarded to a NAT gateway.
VPC peering connection
Traffic intended for the destination is forwarded to a VPC peering connection.
Virtual IP address
Traffic intended for the destination is forwarded to a virtual IP address and then sent to active and standby ECSs to which the virtual IP address is bound.
VPC endpoint
Traffic intended for the destination is forwarded to a VPC endpoint.
Cloud container
Traffic intended for the destination is forwarded to a cloud container.
Enterprise router
Traffic intended for the destination is forwarded to an enterprise router.
Cloud firewall
Traffic intended for the destination is forwarded to a cloud firewall.
Generally, the routes that are automatically added to a VPC route table by a service cannot be modified or deleted. In some specific scenarios, if a service specifies the destination when adding a route, the route can be modified or deleted.
For example, when a NAT gateway is created, a custom route without a specific destination (0.0.0.0/0 is used by default) will be automatically added. In this case, you can change the destination. When you create a VPN gateway, you can specify the remote subnet as the route destination. The VPN service will then add a system route with the remote subnet as the destination. Do not modify the route destination on the Route Tables page of the VPC console. If you do, the destination will be inconsistent with the configured remote subnet on the VPN console. To modify the route destination, go to the VPN console to modify the remote subnet, then the route destination will be changed accordingly.
You cannot add a route whose next hop type is VPC endpoint or Cloud container to a route table. These routes are automatically added by VPC Endpoint or CCE.
How Route Tables Work
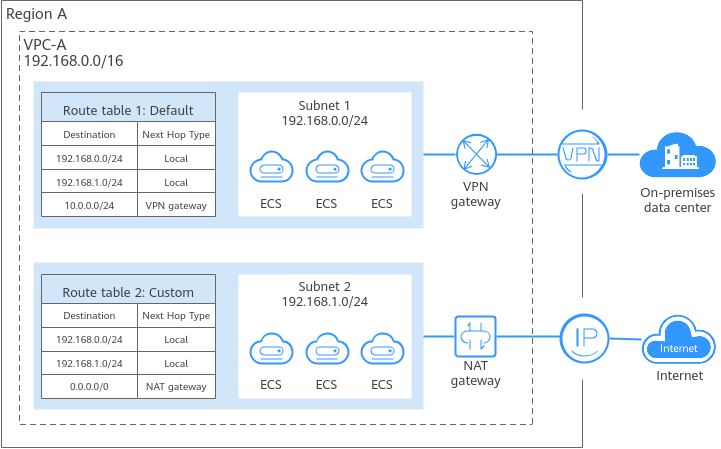
Each subnet in a VPC must have a route table associated. A subnet can be associated with the default route table or a custom route table. For details about the association between a subnet and a route table, see Changing the Route Table Associated with a Subnet.
- Subnet 1 is associated with the default route table that contains a route pointing to the VPN gateway. This route allows ECSs in subnet 1 to access the on-premises data center through VPN.
- Subnet 2 is associated with a custom route table that contains a route pointing to the NAT gateway. This route allows ECSs in subnet 2 to access the Internet through the NAT gateway and EIP.
Route Priority
|
No. |
Route Type |
Description |
|---|---|---|
|
1 |
Local route |
Local routes are system routes used for communications within a VPC and have the highest priority. Table 5 provides examples of local routes. |
|
2 |
Specific route |
Excepting local routes, if there are multiple routes that match the request destination, the longest prefix match is used. This means that the route with the longest subnet mask is preferentially used to determine the next hop. For example, if the destination of traffic entering a VPC is 192.168.1.12/32, the VPC route table has the following routes:
According to the longest prefix match, the request preferentially matches route B and will be forwarded to the VPC peering connection. |
|
3 |
EIP route |
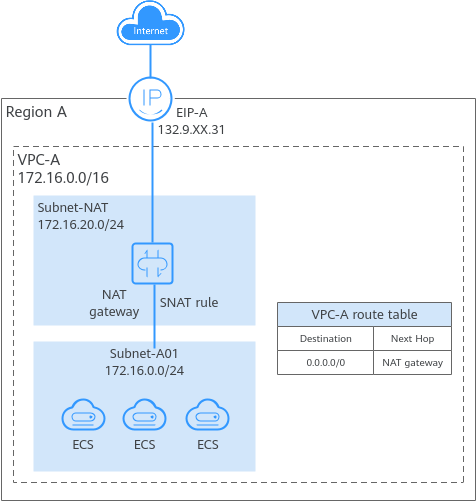
If an ECS in a subnet has an EIP bound, the EIP route takes precedence over the default route (destination: 0.0.0.0/0) in the route table. In this case, the EIP is used to access the Internet.
Example:
In this case, ECS-A will use the EIP to access the Internet instead of the NAT gateway. |
|
4 |
Default route |
The route with the destination 0.0.0.0/0 is the default route, which can match any traffic. According to the longest prefix match, 0.0.0.0/0 has the lowest priority. |
Route Table Configuration
You can configure routes with different next hop types in a VPC route table to meet specific network access requirements. For example, you can set the next hop to a VPC peering connection to enable communications between VPCs, or set the next hop to a NAT gateway to access the Internet.
Constraints
- A VPC can be associated with a maximum of five route tables, including the default route table and four custom route tables.
- All route tables in a VPC can have a maximum of 1,000 routes, excluding system routes.
- Generally, the destination of a custom route cannot overlap with that of a local route. The destination of a local route can be a subnet CIDR block or CIDR blocks that are used for internal communications.
For example, if VPC-A has a subnet that supports IPv4/IPv6 dual stack. Its IPv4 CIDR block is 192.168.2.0/24 and IPv6 CIDR block is 2407:c080:802:be7::/64. The system automatically adds the local routes in Table 5 to the route table of VPC-A. In this case, the destinations of the custom routes you set cannot overlap with those of the existing local routes.
Table 5 VPC-A local routes Local Route Destination
Description
192.168.2.0/24
IPv4 CIDR block of the subnet
2407:c080:802:be7::/64
IPv6 CIDR block of the subnet
100.64.0.0/10
Network used by public services on the cloud, such as DNS
198.19.128.0/20
Network used by internal services, such as VPC Endpoint
127.0.0.0/8
Loopback address
- You cannot add two routes with the same destination to a VPC route table even if their next hop types are different.
Custom Route Table Configuration Process

|
No. |
Step |
Description |
Reference |
|---|---|---|---|
|
1 |
Create a custom route table. |
If the default route table cannot meet your service requirements, you can create a custom route table. |
|
|
2 |
Add a custom route. |
You can add a custom route and configure information such as the destination and next hop in the route to determine where network traffic is directed. |
|
|
3 |
Associate the route table with a subnet. |
After a route table is associated with a subnet, the routes in the route table control the routing for all cloud resources in the subnet. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.