Viewing Vulnerability Details
Scenarios
This section describes how to view vulnerability details, including the vulnerability type distribution, vulnerability list, top assets affected by vulnerabilities, and vulnerability details.
Prerequisites
- Your SecMaster professional edition is available.
- You have installed HSS agent. For details, see Installing an Agent.
- HSS logs have been connected to SecMaster and the function of automatically converting logs into alerts has been enabled. For details, see Cloud Service Access. If access to HSS vulnerability scan results has been enabled but the automatic alert conversion is disabled, the vulnerability scan results will not be displayed on the Vulnerabilities page in SecMaster.
Viewing Vulnerability Details
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose Risk Prevention > Vulnerabilities.
Figure 2 Accessing the Vulnerabilities page
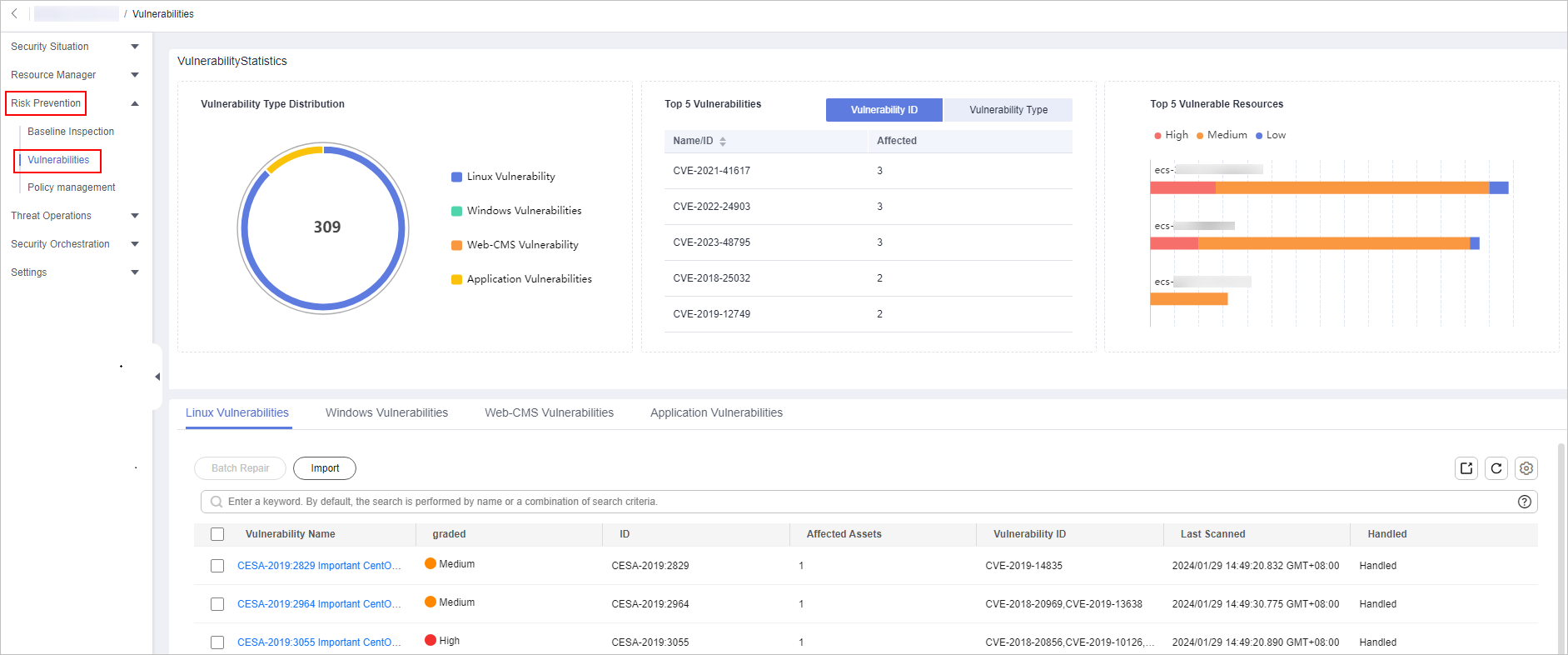
- View vulnerability information on the Vulnerabilities page. You can enter a keyword in the search box above the vulnerability list to filter vulnerabilities.
Table 1 Viewing vulnerability information Parameter
Description
Vulnerability Type Distribution
This graph displays the total number of vulnerabilities and the distribution of vulnerabilities by type.
By default, the system displays the distribution of five types of vulnerabilities: Linux, Windows, Web-CMS, application, and website vulnerabilities. For more details about vulnerabilities, see Overview.
Top 5 Vulnerabilities
The Top 5 Vulnerabilities area lists the five vulnerabilities with the most affected assets. The more affected assets, the higher the vulnerability ranking is.
- The Vulnerability ID tab displays the IDs and the affected asset quantity for the top 5 vulnerabilities.
- The Vulnerability Type tab displays the names, severity levels, and affected asset quantity for the top 5 vulnerabilities.
Top 5 Vulnerable Resources
This metric displays the five assets affected most by vulnerabilities. You can view the proportion of vulnerabilities of each severity for each risky asset in a bar chart.
Vulnerability List
- In the vulnerability list, click the tab of a vulnerability type (for example, Linux Vulnerabilities) to go to the corresponding page. For details about the vulnerability parameters, see Table 2.
- To view details about a vulnerability, click the vulnerability name and view the details on the page displayed on the right.
- You can view the total number of vulnerabilities below the vulnerability list. You can view a maximum of 10,000 vulnerability records page by page. To view more than 10,000 records, optimize the filter criteria.
Table 2 Vulnerability parameters Parameter
Description
Vulnerability Name
Name of the scanned vulnerability.
Click a vulnerability name to view vulnerability description and vulnerability library information.
Severity
Severity level of the vulnerability. There are four risk severity levels: high, medium, low, and informational.
Affected Assets
Total number of assets affected by a vulnerability.
Vulnerability ID
ID of a vulnerability.
Last Scanned
Time of the last scan
Handled
The status of the vulnerability. The value can be Handled or Unhandled.
SecMaster aggregates the vulnerability scan results from HSS and displays vulnerabilities on the Vulnerabilities page in SecMaster. HSS supports automatic, scheduled, and manual scans.
- Automatic scan
By default, the system automatically scans for Linux, Windows, and Web-CMS vulnerabilities every day and scans for application vulnerabilities every Monday. The time of an automatic application vulnerability scan changes with the middleware asset scan time. If a manual or scheduled vulnerability scan has been performed on a day, HSS will not automatically scan for vulnerabilities on that day.
- Scheduled scan
By default, a full server vulnerability scan is performed once a week. To protect workloads, you are advised to set a proper scan period and scan server scope to periodically scan server vulnerabilities.
- Manual scan
If you want to view the vulnerability fixing status or vulnerabilities of a server in real time, manual scans are recommended.
For newly purchased ECSs, if scheduled vulnerability scan and manual scan are not configured in HSS, HSS automatically scans for Linux, Windows, and Web-CMS vulnerabilities in the early morning every day. So, you can view vulnerabilities for newly purchased ECSs on the Vulnerabilities page in SecMaster the next day. Before collecting HSS logs, make sure you have enabled HSS protection for ECSs during the purchase, installed HSS agent, and enabled access to HSS logs and the function of converting logs to alerts in SecMaster.
For more details, see Vulnerability Scan.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






