Overview
This topic describes the query and analysis syntax used during security analysis. SecMaster supports SQL retrieval syntax. Query and analysis statements are used in the area shown in the following screenshot on the SecMaster console.
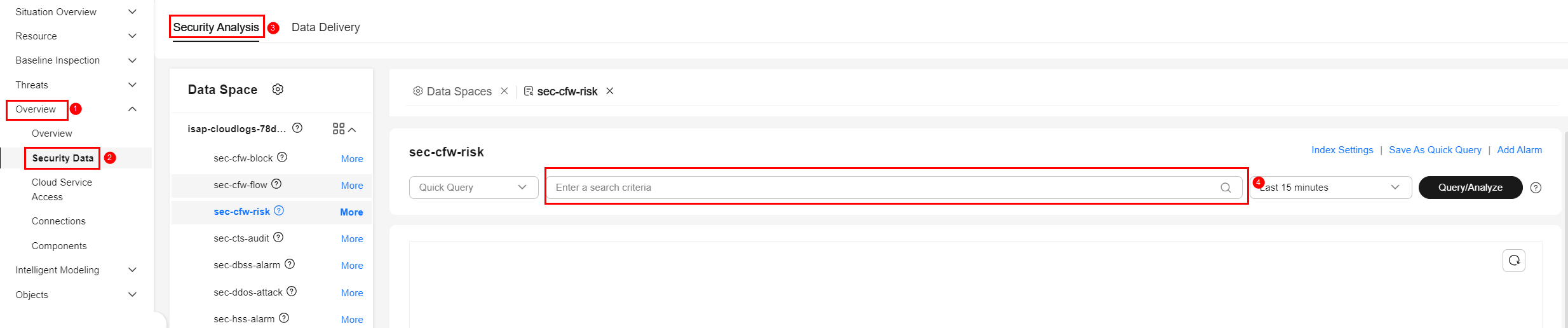
Basic Syntax
An SQL statement consists of a query statement and an analysis statement, which are separated by a vertical bar (|). Query statements can be used independently, but analysis statements must be used together with query statements.
Query Statement | Analysis Statement
|
Statement Type |
Description |
|---|---|
|
A query statement is used to specify the filter criteria for log query and return the logs that meet the filter criteria. By setting filter criteria, you can quickly query required logs. |
|
|
Analysis Statements |
An analysis statement is used to calculate and collect statistics on query results. |
Limitations and Constraints
- Query statements do not support mathematical operations, such as (age + 100) ≤ 1000.
- Aggregate functions support only fields and do not support expressions, for example, avg(log(age)).
- Multi-table association is not supported.
- Subqueries are not supported.
- A maximum of 500 records can be returned on the page.
- A maximum of 10,000 groups can be returned by GROUP BY.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






