Viewing Baseline Check Results
Scenarios
After a check plan is set, you can perform an immediate check on the Baseline Inspection page. It takes about 10 minutes for the check results to be displayed on the result page. For details about how to perform an immediate check, see Starting an Immediate Baseline Check.
If you do not perform an immediate check, the system performs the check at the specified time according to the check plan. For example, the system performs the check every three days by default, and the check is performed from 00:00 to 06:00 each time. You can view the check results on the Check Result page.
This topic describes where to view results of a baseline check plan.
Prerequisites
- Cloud service baseline scanning has been performed.
- Only SecMaster professional edition supports OS Configuration Baseline, Common Weak Password Detection, Password Complexity Policy Detection compliance packs. Before using these packs, you need to enable HSS baseline log access and Automatically converts alarms for HSS baseline logs in SecMaster. For details about how to enable access to logs, see Enabling Log Access.
Viewing Baseline Check Results
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- (Optional) In the navigation pane on the left, choose . On the displayed page, locate the row where SecMaster is located and enable the log access to compliance baseline logs in the Logs column.
SecMaster synchronizes all security data within a region to the first workspace in the region. For non-first workspaces, you need to configure log access manually.
This topic describes how to enable log access to SecMaster manually.
After the setting is complete, you can start an immediate check on the Baseline Inspection page. It takes about 10 minutes for the check results to be displayed on the result page. For details about how to perform an immediate check, see Starting an Immediate Baseline Check.
If you do not perform an immediate check, the system performs the check at the specified time according to the check plan. For example, the system performs the check every three days by default, and the check is performed from 00:00 to 06:00 each time. You can view the check results on the Check Result page.
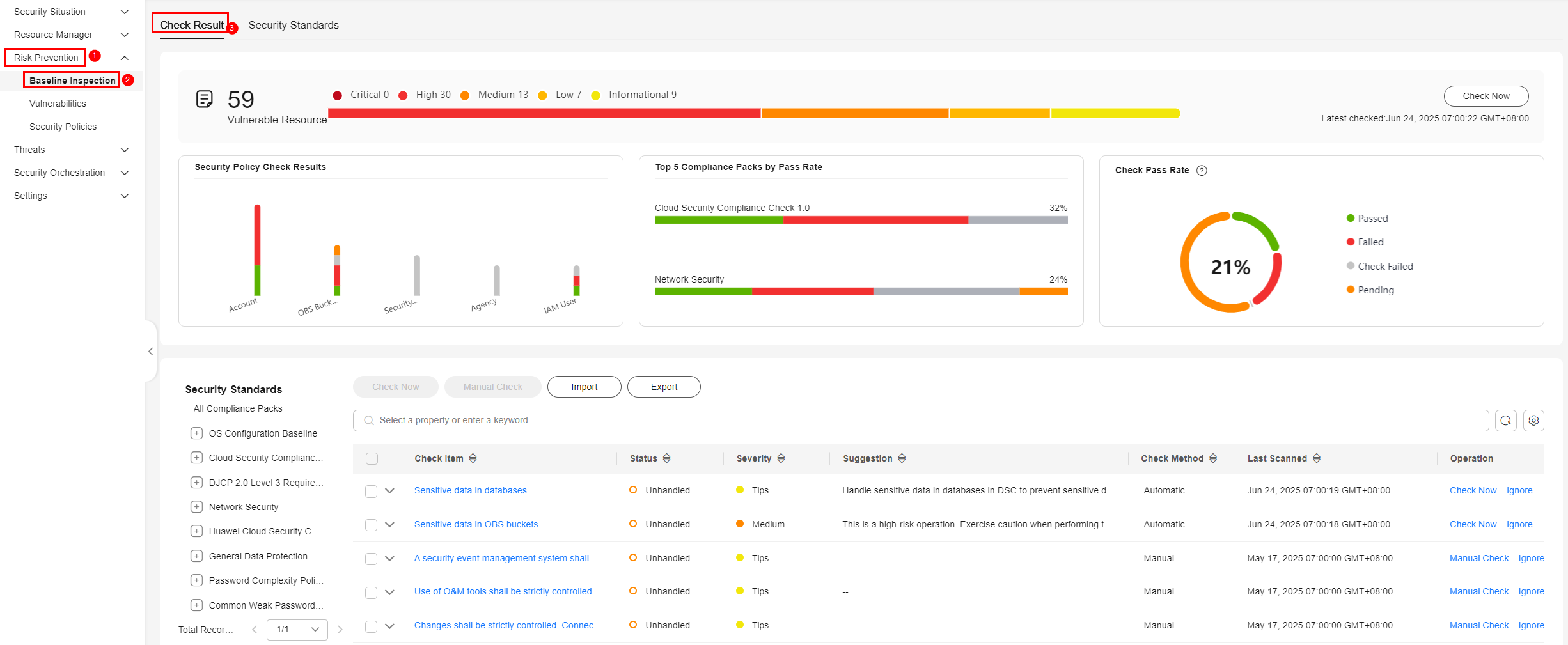
- In the navigation pane on the left, choose Risk Prevention > Baseline Inspection.
- On the Check Result tab, view the check results of check items. For details about the parameters, see Table 1.
Figure 2 Viewing baseline check results
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






