Example 1: Allowing the Inbound Traffic from a Specified IP Address
This section describes how to allow access traffic from a specified IP address in the inbound direction. For more parameter settings, see Configuring Protection Rules to Block or Allow Internet Border Traffic.
Allowing the Inbound Traffic from a Specified IP Address
Configure two protection rules. One of them blocks all traffic. Its priority is the lowest. The other allows the traffic of a specified IP address, and its priority is the highest. Configure other parameters as needed.
- One of them blocks all traffic and has the lowest priority. Configure the following parameters and set the rest of the parameter as needed:
Figure 1 Blocking all traffic
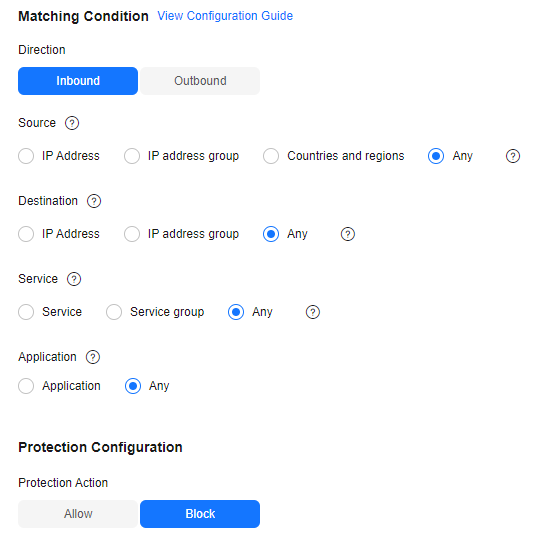
Table 1 Blocking all traffic Parameter
Example Value
Description
Direction
Inbound
Direction of the protected traffic.
Source
Any
Origin of network traffic.
Destination
Any
Receiver of network traffic.
Service
Any
Protocol, source port, and destination port of network traffic.
Action
Block
Action taken when traffic passes through the firewall.
- The other rule allows traffic from a specified IP address to pass through and has the highest priority. Configure the following parameters and set the rest of the parameter as needed:
Figure 2 Allowing a specified IP address
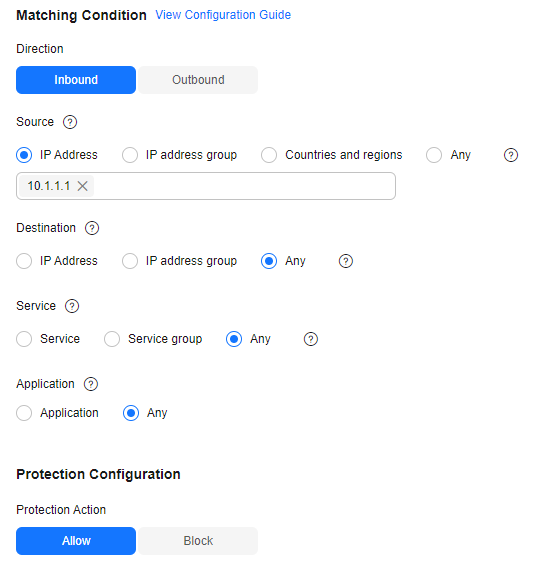
Table 2 Allowing a specified IP address Parameter
Example Value
Description
Direction
Inbound
Direction of the protected traffic.
Source
IP Address
192.168.0.0
Origin of network traffic.
Destination
Any
Receiver of network traffic.
Service
Any
Protocol, source port, and destination port of network traffic.
Action
Allow
Action taken when traffic passes through the firewall.
Follow-up Operations
- Policy hits: For details about the protection overview, see Viewing Protection Information Using the Policy Assistant. For details about logs, see Access Control Logs.
- For details about the traffic trend and statistics, see Traffic Analysis. For details about traffic records, see Traffic Logs.
References
- For details about protection rule parameters, see Configuring Protection Rules to Block or Allow Internet Border Traffic.
- For details about blacklist and whitelist configuration, see Adding Blacklist or Whitelist Items to Block or Allow Traffic.
- For details about how to batch add protection policies, see Importing and Exporting Protection Policies.
- For details about how to block network attacks, see Configuring Basic IPS Protection.
- For details about antivirus, see Configuring Virus Defense.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






