Origin Request Headers
You can configure HTTP headers in origin pull URLs.
Background
If the requested content is not cached on CDN PoPs, CDN PoPs pull that content from an origin server. You can configure HTTP headers on the CDN console to rewrite header details in origin pull URLs.
HTTP headers are part of an HTTP request or response message that defines the operating parameters of an HTTP transaction.

Precautions
- This setting only modifies HTTP messages for origin pull through CDN. It does not modify those in an HTTP message that CDN PoPs return to users.
- A request header cannot have two different values at the same time.
- If your domain name has special configurations, the origin request headers cannot be configured.
- You can add up to 10 headers.
Procedure
- Log in to the CDN console.
- In the navigation pane, choose .
- In the domain list, click the target domain name or click Configure in the Operation column.
- Click the Origin Settings tab.
- In the Origin Request Headers area, click Add.
- Configure the header details.
- Add: Add a header to CDN to rewrite HTTP headers in user request URLs.
Figure 1 Adding an origin request header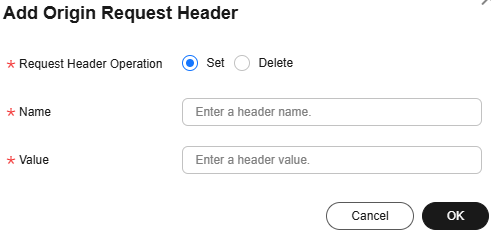
Table 1 Parameter description Parameter
Example
Description
Request Header Operation
Set
Add a specific header to an HTTP request of origin pull.
- If a request URL contains the X-test header and its value is 111, CDN will set X-test to aaa during origin pull.
- If a request URL does not contain the X-test header, CDN will add X-test and set its value to aaa during origin pull.
Delete
Delete the HTTP header that exists in a user request URL.
- If a request URL contains the X-test header, it will be deleted during origin pull.
Name
X-test
- Enter 1 to 100 characters.
- Start with a letter and use only letters, digits, and hyphens (-).
Value
aaa
- Enter 1 to 1,000 characters.
- Use only letters, digits, and these special characters: .-_*#!&+|^~'"/:;,=@?<>${}
- ${ and } must be used in pairs.
- Supported variables:
- ${arg_xxx}: obtains the value of request parameter xxx. xxx can contain letters, digits, hyphens (-), underscores (_), periods (.), and tildes (~). xxx is case sensitive. That is, ${arg_test} and ${arg_TEST} are different.
- ${http_xxx}: obtains the value of request header xxx. xxx can contain letters, digits, underscores (_), and periods (.).
- xxx is case insensitive. That is, ${http_test} and ${http_TEST} are the same.
- To obtain the value of request header xxx using a variable, replace the hyphen (-) with an underscore (_) when configuring the request header. For example, to obtain the value of request header X-CCDN-Test, set this parameter to ${http_X_CCDN_Test}.
- ${request_method}: obtains the request method.
- ${host}: obtains the acceleration domain name.
- ${remote_addr}: obtains the client IP address.
- You can concatenate variables, such as ${host}and${arg_name}, but you cannot nest them, such as ${${host}}.
- Edit: Modify the value or operation of a header during origin pull. Click Edit in the Operation column next to a header.
Figure 2 Editing an origin request header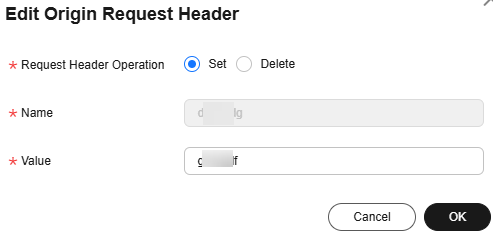
Parameter
Example
Description
Request Header Operation
Set
Add a specific header to an HTTP request of origin pull.
- If a request URL contains the X-test header and its value is 111, CDN will set X-test to aaa during origin pull.
- If a request URL does not contain the X-test header, CDN will add X-test and set its value to aaa during origin pull.
Delete
Delete the HTTP header that exists in a user request URL.
- If a request URL contains the X-test header, it will be deleted during origin pull.
Name
X-test
This parameter cannot be modified.
Value
aaa
- Enter 1 to 1,000 characters.
- Use only letters, digits, and these special characters: .-_*#!&+|^~'"/:;,=@?<>$%{}
- ${ and } must be used in pairs.
- Supported variables:
- ${arg_name}: obtains the value of request parameter name (changeable).
- ${http_name}: obtains the value of request header name (changeable).
- ${request_method}: obtains the request method.
- ${host}: obtains the acceleration domain name.
- ${remote_addr}: obtains the client IP address.
- Variables can be concatenated but cannot be nested. For example, ${host}and${arg_name} is supported, but ${${host}} is not.
- Delete: Delete the header settings. Click Delete in the Operation column of the request header to be deleted. In the displayed dialog box, select other domain names with the same header to be deleted and click OK.
- Click OK.
Examples
Assume that you have configured the following origin request headers for domain name www.example.com:

When a user requests the http://www.example.com/abc.jpg file that is not cached on CDN, CDN pulls that file from the origin server. The X-cdn header will be added and the X-test header will be deleted during origin pull.
Constraints
- If your domain name has special configurations, Content-Type, Cache-Control, and Expires cannot be configured.
- The following request headers can only be modified. You cannot set Request Header Operation to Delete for them.
Expires
Content-Disposition
Content-Type
Content-Language
Cache-Control
-
- The following standard headers cannot be added, deleted, or modified.
a_dynamic
cross-origin-embedder-policy
origin
strict-transport-security
accept
cross-origin-opener-policy
ping-from
te
accept-ch
cross-origin-resource-policy
ping-to
timing-allow-origin
accept-charset
date
pragma
tk
accept-ch-lifetime
device-memory
proxy-authenticate
trailer
accept-push-policy
dnt
proxy-authorization
transfer-encoding
accept-ranges
dpr
public-key-pins
upgrade
accept-signature
early-data
public-key-pins-report-only
upgrade-insecure-requests
access-control-allow-credentials
etag
push-policy
vary
access-control-allow-headers
expect
range
via
access-control-allow-methods
expect-ct
referer-policy
viewport-width
access-control-allow-origin
feature-policy
report-to
warning
access-control-expose-headers
forwarded
retry-after
width
access-control-max-age
from
save-data
www-authenticate
access-control-request-headers
host
sec-fetch-dest
x-client-ip
access-control-request-method
if-match
sec-fetch-mode
x-content-type-options
age
if-modified-since
sec-fetch-site
x-dns-prefetch-control
allow
if-none-match
sec-fetch-user
x-download-options
alt-svc
if-range
sec-websocket-accept
x-firefox-spdy
authorization
if-unmodified-since
sec-websocket-extensions
x-forwarded-for
clear-site-data
keep-alive
sec-websocket-key
x-forwarded-host
connection
large-allocation
sec-websocket-protocol
x-frame-options(xfo)
content-dpr
last-event-id
sec-websocket-version
x-permitted-cross-domain-policies
content-encoding
last-modified
server
x-pingback
content-length
link
server-timing
x-powered-by
content-location
location
service-worker-allowed
x-requested-with
content-range
max-age
signature
x-robots-tag
content-security-policy
max-forwards
signed-headers
x-ua-compatible
content-security-policy-report-only
nel
sourcemap
x-xss-protection
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






