Encrypting EVS Disks
Encrypting cloud disks ensures data privacy and control, making it ideal for scenarios that demand high security or compliance standards. This section describes how to use the keys managed by Data Encryption Workshop (DEW) to encrypt EVS disks.
Prerequisites
- You have created a cluster and installed the CCE Container Storage (Everest) add-on in the cluster.
- An available key has been created in DEW. For details, see Creating a Key.
- To create a cluster using commands, ensure kubectl is used. For details, see Accessing a Cluster Using kubectl.
Automatically Creating an Encrypted EVS Volume
CCE allows you to dynamically create encrypted EVS volumes using the console or kubectl to protect data privacy and autonomy.
- Log in to the CCE console and click the cluster name to access the cluster console.
- Dynamically create a PVC and PV.
- Choose Storage in the navigation pane and click the PVCs tab. Click Create PVC in the upper right corner. In the dialog box displayed, configure PVC parameters.
- Select EVS for the StorageClass, enable encryption, and choose a key. Configure other parameters based on service requirements. For details, see Using an EVS Disk Through a Dynamic PV.
Figure 1 Encrypted storage volume
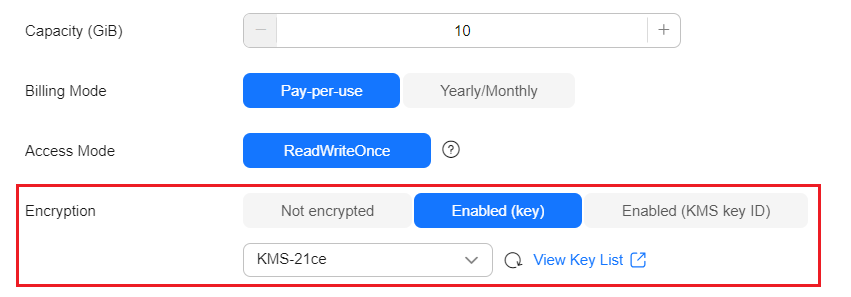
- Click Create.
- Go to the PVCs tab and check whether the PVC of the encrypted EVS disk is created and whether the disk is encrypted.
Figure 2 Encrypted PVC
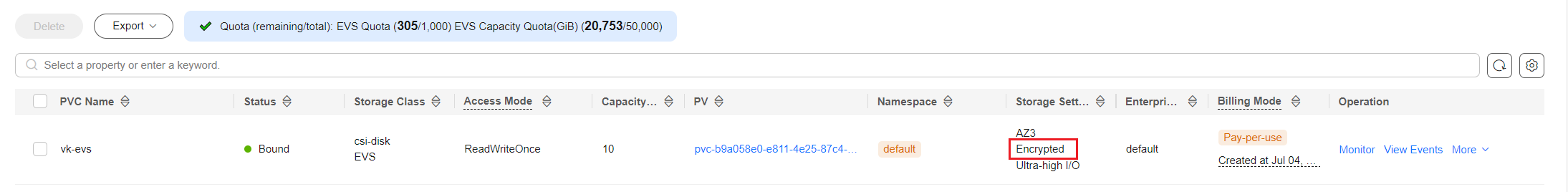
- The method of using an encrypted PVC is the same as that of using a regular PVC.
- Use kubectl to access the cluster.
- Create the pvc-evs-auto.yaml file. For details, see Using kubectl.
apiVersion: v1 kind: PersistentVolumeClaim metadata: name: pvc-evs-auto namespace: default annotations: everest.io/disk-volume-type: SAS # EVS disk type everest.io/crypt-key-id: 37f202db-a970-4ac1-a506-e5c4f2d7ce69 # Encryption key ID, which can be obtained from DEW labels: failure-domain.beta.kubernetes.io/region: <your_region> # Region of the node where the application is to be deployed failure-domain.beta.kubernetes.io/zone: <your_zone> # AZ of the node where the application is to be deployed spec: accessModes: - ReadWriteOnce # The value must be ReadWriteOnce for EVS disks. resources: requests: storage: 10Gi # EVS disk capacity, ranging from 1 to 32768 storageClassName: csi-disk # The StorageClass is EVS.Table 1 Encryption parameters Parameter
Example Value
Description
everest.io/crypt-key-id
37f202db-a970-4ac1-a506-e5c4f2d7ce69
ID of an encryption key, which can be obtained from DEW.
- Run the following command to create a PVC:
kubectl apply -f pvc-evs-auto.yaml
- Go to the PVCs tab and check whether the PVC of the encrypted EVS disk is created and whether the disk is encrypted.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






