Configuring Connection Protection

The connection protection function is still in the open beta test (OBT) phase. This function is supported only by Unlimited Protection Advanced Edition instances in North China regions. You can submit a service ticket to enable this function.
If an origin server IP address frequently sends suspicious packets, you can configure connection protection to block the IP address. After the blocking period expires, the access from the IP address will be allowed.
Procedure
- Log in to the management console.
- Select a region in the upper part of the page, click
 in the upper left corner of the page, and choose . The Anti-DDoS Service Center page is displayed.
in the upper left corner of the page, and choose . The Anti-DDoS Service Center page is displayed. - In the navigation pane on the left, choose . The Protection Policies page is displayed.
- Click Create Protection Policy.
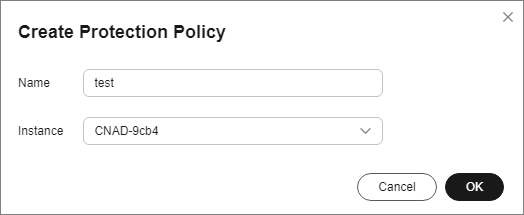
- In the displayed dialog box, set the policy name, select an instance, and click OK.
Figure 1 Creating a policy
- In the row containing the target policy, click Set Protection Policy in the Operation column.
- In the Connection Protection area, click Set.
Figure 2 Connection Protection
- Enable TCP Flood Attack Defense and set other parameters.
Figure 3 Connection Protection Settings
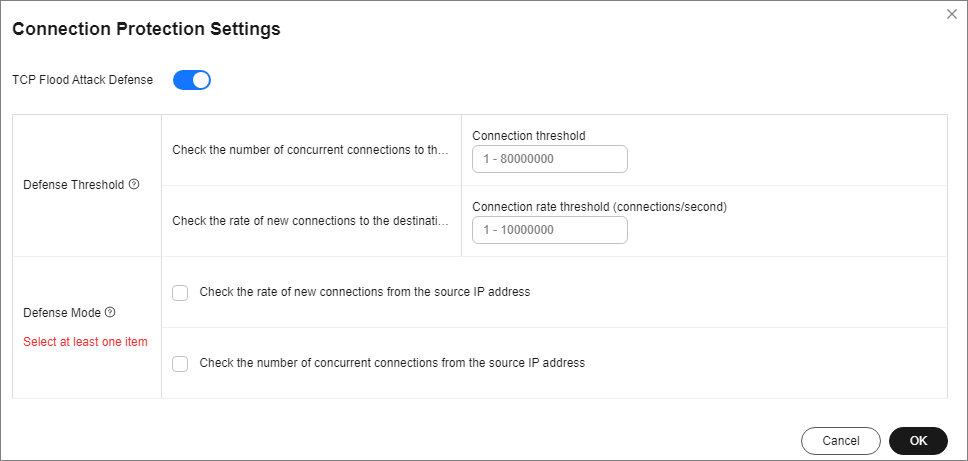
Table 1 Parameter description Parameter
Description
Check the number of concurrent connections to the destination IP address.
When the number of the concurrent TCP connections of a destination IP address exceeds Threshold, defense against connection flood attacks is started. After the defense is started, the source IP address starts to be checked. The value ranges from 1 to 80000000.
Check the rate of new connections to the destination IP address.
When the number of the new TCP connections per second of a destination IP address exceeds Threshold, defense against connection flood attacks is started. After the defense is started, the source IP address starts to be checked. The value ranges from 1 to 10000000.
Check the rate of new connections from the source IP address.
After defense against connection flood attacks is enabled, if the number of the TCP connections initiated by a source IP address within Check Cycle exceeds Threshold, the source IP address is regarded as the attack source and is reported to the ATIC management center. The values range from 1 to 60 (s) and 1 to 80000000, respectively.
Check the number of concurrent connections from the source IP address.
After defense against connection flood attacks is enabled, if the number of the concurrent TCP connections of a source IP address exceeds Threshold, the source IP address is regarded as the attack source and is reported to the ATIC management center. The value ranges from 1 to 80000000.
- Click OK.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.









