Accessing Huawei Cloud over a Public Network (Different Regions)
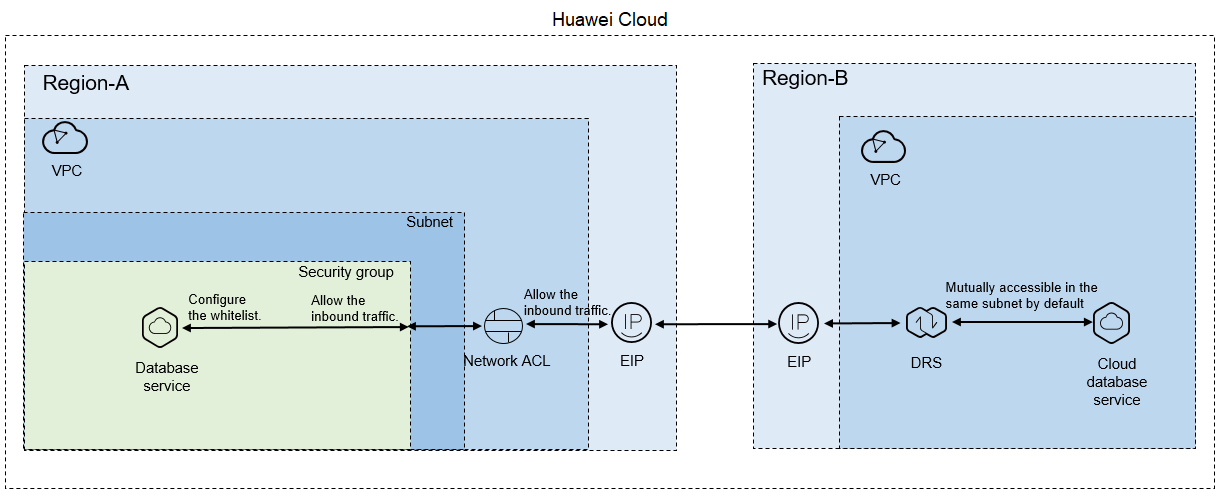
Figure 1 shows how to use DRS to migrate data from an ECS database to a database in different regions over a public network on Huawei Cloud.
You can use an ECS database as the source. If the source and destination databases are in different regions and DRS uses a public network, bind an EIP to the ECS where the source database is located, configure the inbound rules for the network ACL and security group associated with the source database in Region-A to allow inbound traffic from the EIP of the DRS replication instance, add the EIP of the DRS replication instance to the whitelist of the source database, and configure the outbound rules for the network ACL and security group associated with the DRS replication instance in Region-B to allow outbound traffic. Figure 2 shows the process.
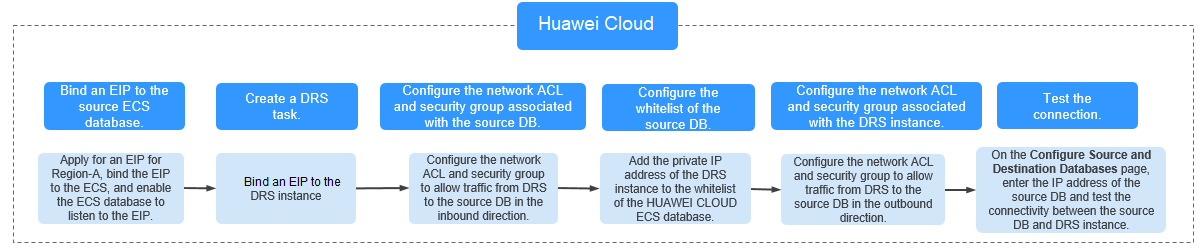
Network Configurations
- Bind an EIP to the source database.
For details, see the official documents of Huawei Cloud databases.
- Create a DRS task through a public network and bind an EIP to the DRS instance.
When creating a DRS task through a public network, you can bind an EIP to the DRS instance on the instance details page.
- Configure inbound rules for the network ACL and security group associated with the source database.
Security group: Add an inbound rule to allow traffic from the EIP of the DRS replication instance to the database listening port.
Network ACL: By default, a VPC does not have a network ACL. If you have a network ACL, add an inbound rule to allow traffic from the EIP and random port of the DRS replication instance to the IP address and listening port of the source database.
- Configure the IP address whitelist for the ECS database.
Add the private IP address of the DRS instance to the whitelist of the ECS database. The method for configuring the whitelist depends on the cloud database type. For details, see the official documents of the corresponding database.
- Configure outbound rules for the network ACL and security group associated with the replication instance.
By default, a VPC does not have a network ACL, and the default security group rules allow all outbound traffic. The replication instance and destination RDS database in the same security group can communicate with each other by default, so you do not need to configure a network ACL.
If you have configured a network ACL or security group, log in to the VPC management console and check the settings:
Security group: Ensure that the outbound traffic from the security group associated with the replication instance to the IP address and listening port of the source database is allowed.
Network ACL: Ensure that the outbound traffic from the VPC where the replication instance resides and the DRS random port to the IP address and listening port of the source database is allowed.
- Test the connection.
Log in to the DRS console, locate the created DRS task, and click Edit in the Operation column. On the Configure Source and Destination Databases page, enter the IP address, port, username, and password of the source database and then click Test Connection to check whether the connection is successful.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.