Access Control Policy Overview
CFW allows all traffic by default. If no access control policies are configured, all the communication between internal servers and the Internet will be allowed. Unauthorized access or the lateral threat movement will go unchecked. You can configure access control policies in CFW to allow or block specific traffic and implement multi-dimensional protection.
Access Control Policy Types
Access control policies include protection rules, the blacklist, and the whitelist. Table 1 describes their differences. If traffic hits a policy, the action specified in the policy will be performed.
|
Type |
Protected Object |
Network Type |
Action |
Configuration Method |
|---|---|---|---|---|
|
Protection rules |
|
|
|
Configuring Protection Rules to Block or Allow Internet Border Traffic |
|
Blacklist |
|
|
Traffic is blocked directly. |
Adding Blacklist or Whitelist Items to Block or Allow Traffic |
|
Whitelist |
Traffic is allowed by CFW and not checked by other functions. |
Priority of Access Control Policies
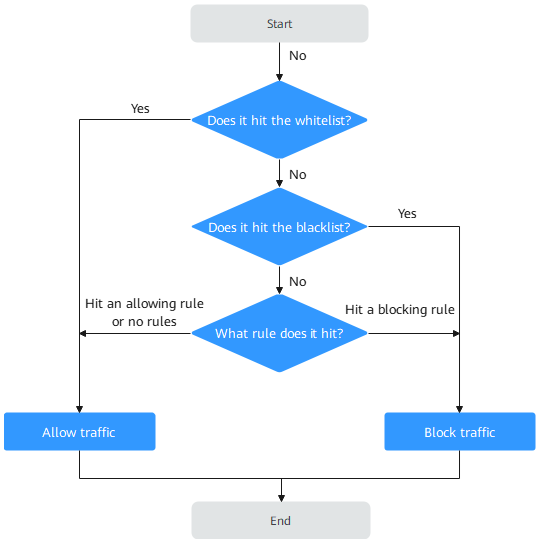
For details about the protection sequence of all CFW policies, see What Are the Priorities of the Protection Settings in CFW?
Specification Limitations
To enable VPC border protection and NAT protection, use the CFW professional edition and enable the VPC border firewall.
Precautions for Configuring a Blocking Policy
The precautions for configuring a protection rule or a blacklist item for blocking IP addresses are as follows:
- You are advised to preferentially configure specific IP addresses (for example, 192.168.10.5) to reduce network segment configurations and avoid improper blocking.
- Exercise caution when configuring protection rules to block reverse proxy IP addresses, such as the WAF back-to-source IP addresses. You are advised to configure protection rules or whitelist to permit reverse proxy IP addresses.
- Blocking forward proxy IP addresses (such as company egress IP addresses) can have a large impact. Exercise caution when configuring protection rules to block forward proxy IP addresses.
- When configuring region protection, take possible EIP changes into consideration.
A protection rule with its source or destination set to a region (geographical location) takes effect only for IPv4 protected objects.
Elements in a Protection Rule
Protection rules can identify and match different traffic elements to allow or block related traffic.
Example configuration:
|
Parameter |
Input |
Description |
|---|---|---|
|
Source/Destination |
0.0.0.0/0 |
All IP addresses |
|
Domain name |
www.example.com |
Domain name www.example.com |
|
*.example.com |
All domain names ending with example.com, for example, test.example.com |
|
|
Service - Source port or destination port |
1-65535 |
All ports |
|
80-443 |
All ports in the range 80 to 443 |
|
|
Ports 80 and 443 |
References
- For details about how to add a protection rule to protect traffic, see Configuring Protection Rules to Block or Allow Internet Border Traffic.
- For details about how to add a blacklist or whitelist item to protect traffic, see Adding Blacklist or Whitelist Items to Block or Allow Traffic.
- For details about how to add protection policies in batches, see Importing and Exporting Protection Policies.
- Follow-up operations after adding a policy:
- Policy hits: For details about the protection overview, see Viewing Protection Information Using the Policy Assistant. For details about logs, see Access Control Logs.
- For details about the traffic trend and statistics, see Traffic Analysis. For details about traffic records, see Traffic Logs.
- If your traffic is incorrectly blocked by a protection policy, troubleshoot the problem by referring to What Do I Do If Service Traffic is Abnormal?
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






