Encrypting Data in EVS
KMS encrypts created cloud disks to ensure data security.
- The encryption attribute of a disk cannot be changed after the disk is created.
- For details about how to create an encrypted disk, see Purchasing an EVS Disk.
- Disk encryption is used for data disks only. System disk encryption relies on the image. For details, see Encrypting Data in IMS.
Scenario
You can use the key provided by KMS to encrypt data on the disk as required during EVS disk creation. You do not need to build or maintain the key management infrastructure, ensuring security and convenience.
KMS keys include default keys, custom keys, and shared keys.
- Default key: The key that is automatically created by EVS through KMS and named evs/default.
The default key cannot be disabled and does not support scheduled deletion.
- Custom key: Keys created by users. You can select an existing key or create one. For details, see "Key Management Service" > "Creating a Key" in Data Encryption Workshop (DEW) User Guide.
You will be billed for the custom keys you use. If pay-per-use keys are used, ensure that you have sufficient account balance. If yearly/monthly keys are used, renew your order timely. Or, your services may be interrupted and data may never be restored if encrypted disks become inaccessible.
- Shared key: You can create KMS resources using DEW to share your keys with other accounts. For details, see "Permission Management" > "Sharing" > "Shared KMS" in Data Encryption Workshop (DEW) User Guide.
When an encrypted disk is attached, EVS accesses KMS, and KMS sends the data key (DK) to the host memory for use. The disk uses the DK plaintext to encrypt and decrypt disk I/Os. The DK plaintext is only stored in the memory of the host housing the ECS and is not stored persistently on the media. If the custom key is deleted or disabled in KMS, the disk encrypted using the key can still use the DK plaintext stored in the host memory. However, if the disk is detached, the DK plaintext will be deleted from the memory, and the disk cannot be read or written. Before you re-attach this encrypted disk, ensure that the key is enabled.
If disks are encrypted using a custom key, which is then disabled or scheduled for deletion, the disks can no longer be read or written, and data on these disks may never be restored. For details, see Table 1.
|
Custom Key Status |
Impact on Encrypted Disks |
Restoration Method |
|---|---|---|
|
Disabled |
|
Enable the CMK. For details, see Enabling a Key. |
|
Scheduled deletion |
Cancel the scheduled deletion for the CMK. For details, see Canceling the Scheduled Deletion of One or More CMKs. |
|
|
Deleted |
Data on the disks can never be restored. |
Resource and Cost Planning
|
Resource |
Description |
Monthly Fee |
|---|---|---|
|
EVS |
|
For details about billing rules, see Billing for Disks. |
|
KMS |
|
For details about billing rules, see Billing Items. |
User Permissions
- Security administrators (users having Security Administrator rights) can grant the KMS access rights to EVS for using disk encryption.
- When a common user who does not have the Security Administrator rights needs to use the disk encryption feature, the condition varies depending on whether the user is the first one ever in the current region or project to use this feature.
- If the user is the first, the user must contact a user having the Security Administrator rights to grant the KMS access rights to EVS. Then, the user can use the disk encryption feature.
- If the user is not the first, the user can use the disk encryption function directly.
From the perspective of a tenant, as long as the KMS access rights have been granted to EVS in a region, all users in the same region can directly use the disk encryption feature.
If there are multiple projects in the current region, the KMS access permissions need to be granted to each project in this region.
Using KMS to Encrypt a Disk (on the Console)
- Log in to the EVS console.
- Click Buy Disk in the upper right corner of the EVS console.
- Select the Encryption check box.
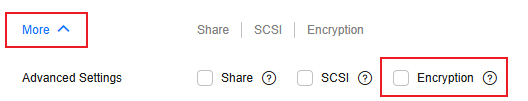
- Click More. The Encryption check box is displayed.
Figure 1 More
- Create an agency.
Select Encryption. If EVS is not authorized to access KMS, the Create Agency dialog box is displayed. In this case, click Yes to authorize it. After the authorization, EVS can obtain KMS keys to encrypt and decrypt disks.
Before you use the disk encryption function, KMS access rights need to be granted to EVS. If you have the right for granting, grant the KMS access rights to EVS directly. If you do not have the permission, contact a user with the Security Administrator permission for authorization, and then try again.
- Select Encryption. The Encryption Settings dialog box is displayed.
Figure 2 Encryption Settings dialog box
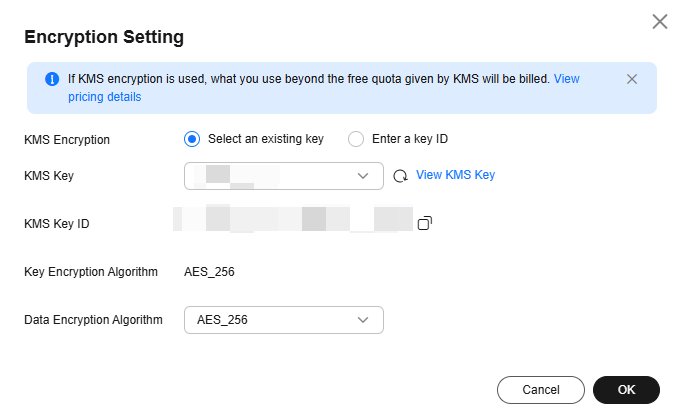
- Set KMS Encryption.
- Select an existing key.
- Click
 and select the key used for encryption.
The key name identifies a key. You can select the following keys:
and select the key used for encryption.
The key name identifies a key. You can select the following keys:- Default keys: After the KMS access permission is granted to EVS, the system automatically creates a default key evs/default.
- Custom keys: Keys you already have or just created. For details, see Creating a Key.
- Click View KMS Key to view all keys.
- Click OK.
- Click
- Enter a key ID.
Figure 3 Entering a key ID
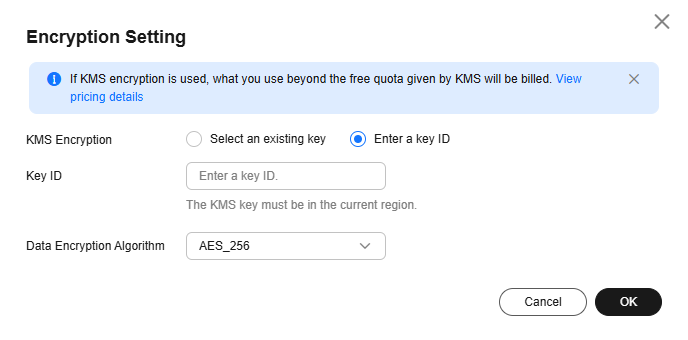
- Enter the ID of the key used for encryption.
- Click OK.
- Select an existing key.
- Click More. The Encryption check box is displayed.
- Configure other parameters and click Buy now.
Using KMS to Encrypt a Disk (Through an API)
You can call the required API of EVS to purchase an encrypted EVS disk. For details, see Elastic Volume Service API Reference.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






