Configuring Playbooks
Scenarios
This topic describes how to configure the playbook. After you configure this playbook, once this playbook discovers that attacks are approaching servers, it notifies operations personnel.
Prerequisites
- You have enabled access to HSS and WAF alerts on the page.
You have enabled the function of automatically converting logs into alerts for HSS. For details, see Enabling Log Access.
- On the Resource Manager page in the current SecMaster workspace, click an asset name. On the asset details page displayed, associate the website asset with the server asset.
- SecMaster has obtained the SMN FullAccess permission, which specifies all permissions of SMN.
Table 1 Description Permission
Description
Principal
Usage
SMN FullAccess
All permissions for SMN.
SecMaster_Agency
SecMaster uses SMN to send playbook execution notifications.
Perform the following steps to check whether SecMaster has obtained the SMN FullAccess permission: If the permission is not allocated, allocate it to SecMaster by referring to Authorizing SecMaster.
- Log in to the SecMaster console as an administrator.
- Click
 in the upper left corner of the page and choose Management & Governance > Identity and Access Management.
in the upper left corner of the page and choose Management & Governance > Identity and Access Management. - In the navigation pane on the left, choose Agencies. On the Agencies page, click SecMaster_Agency and then click the Permissions tab to view all authorization records of SecMaster_Agency.
Step 1: Create and Subscribe to a Topic
- Log in to the SecMaster console.
- In the upper left corner of the page, click
 and choose .
and choose . - Create a topic.
- In the navigation pane on the left, choose . In the upper right corner of the displayed page, click Create Topic.
- In the Create Topic dialog box displayed, configure topic information and click OK.
- Topic Name: Set it to SecMaster-Notification.
- Display Name: SecMaster notification topic is recommended.
- Retain the default settings for other parameters.
Topic Name must be to SecMaster-Notification, or playbooks may fail to be executed.
- Add a subscription.
- On the Topics page, locate the row that contains the SecMaster-Notification topic and click Add Subscription in the Operation column.
- On the displayed Add Subscription slide-out panel, configure subscription information and click OK.
- Protocol: Select Email.
- Endpoint: Enter the email address of the subscription endpoint, for example, username@example.com.
- Confirm the subscription.
After a subscription is added, a confirmation email will be sent to the email address set in 4. Click the subscription confirmation link in the email. A page for a successful subscription will be displayed.
Step 2: Configure and Enable the Playbook
- Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose Security Orchestration > Playbooks.
Figure 2 Accessing the Playbooks tab
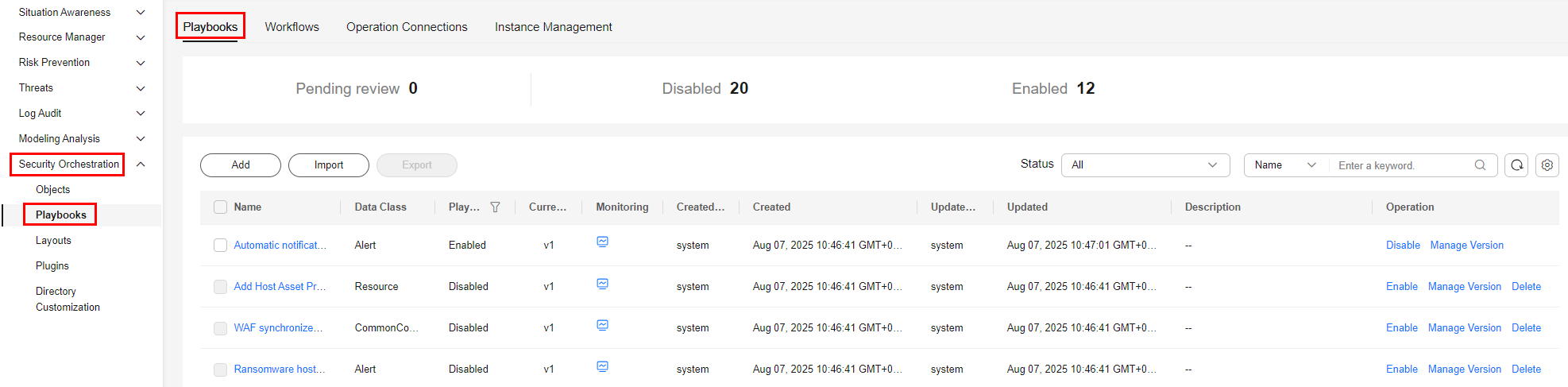
- On the Playbooks page, locate the row that contains the Attack link analysis alert notification playbook and click Enable in the Operation column.
- In the dialog box displayed, select the initial playbook version v1 and click OK.
Implementation Effect
After the attack link analysis notification playbook is executed, server assets and the website assets will be associated based on corresponding HSS and WAF alerts.

Comments on the corresponding alert added to the playbook

Alert notification email sent to specified personnel

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






