Using a Client to Log In to Your Bastion Host
Your current client-based operation experience is still useful while using a bastion host for operations. Through your bastion host, you can use an SSH or Microsoft Terminal Services Client (MSTSC) client to directly log in to managed resources for operations.
- SSH client logins can be authenticated by static passwords, public keys, SMS messages, mobile OTPs, or OTP tokens.
- MSTSC client logins can only be authenticated by static passwords.
- SecureCRT 8.0 or later and Xshell 5 or later are recommended.
Using an SSH Client to Log In to Your Bastion Host
You can use an SSH client to log in to your authorized resources over your bastion host.
- Only host resources configured with the SSH, Telnet, or Rlogin protocols can be logged in through an SSH client.
- SecureCRT 8.0 or later and Xshell 5 or later are recommended.
- Start the local SSH client tool and choose File > New to create a user session.
- Configure session connections.
- Method 1
In the displayed dialog box, select a protocol type, enter the EIP and port number (2222) of the bastion host instance, and click OK. Enter the login name of your CBH system account and click Connect.
- Method 2
- In the newly opened blank session window, run a command in the following format: Protocol type User login name@System login IP address Port number, for example, ssh admin@10.10.10.10 2222. After the login, select the target server.
- In a newly opened blank session window, run a login command: {Protocol type} {Bastion host user login name}@{Host account username}@{Linux host IP address}@{Bastion host IP address} {Port}. For example, you can run ssh admin@10.10.10.10@10.10.10.101 2222 to log in to the target server.
- Method 3
- In a newly opened blank session window, run a login command: {Protocol type} {User login name}@{System login IP address} -p {Port number}, for example, ssh admin@10.10.10.10 -p 2222. After the login, select the target server.
- In a newly opened blank session window, run a login command: {Protocol type} {Bastion host user login name}@{Host account username}@{Linux host IP address}@{Bastion host IP address} -p {Port}. For example, you can run ssh admin@10.10.10.10@10.10.10.101 -p 2222 to log in to the target server.
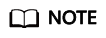
system login IP address indicates the private IP address or EIP of your bastion host. Make sure the network connection between the local PC and the IP address is normal.
- Method 1
- Authenticate user identities.
Enter your identity credentials as prompted.
- If an SSH client is used, passwords, SMS messages, mobile OTPs, and OTP tokens can be used for login identity authentication. To enable SMS, Mobile OTP, or OTP token authentication, you need to configure multi-factor authentication. For details, see Configuring Multifactor Verification.
- To configure an automatic logout timeout for inactive users, see Configuring Client Login.
Table 1 SSH client login authentication Login Type
Login Description
Configuration Description
Password
Enter the username and password of your bastion host account.
Default login method.
The login passwords in the AD, RADIUS, LDAP, or Azure AD authentication are the passwords of users on the remote server. For details, see Remote Authentication Management.
SSH Pubkey
Enter the private key and private key password for login authentication. After the login authentication is successful, next time the user can log in to the system over the SSH client without entering the password.
You need to generate a public and private key pair for login verification and add the SSH public key to the CBH system in the Profile center. For details, see Adding an SSH Public Key.
SMS
In SMS authentication, enter the Password or SSH Pubkey and the SMS verification code you will receive to complete the login authentication.
An available phone number has been configured for the account.
Mobile OTP
In Mobile OTP authentication, enter the Password or SSH Pubkey and the OTP token to complete the login authentication.
NOTE:Ensure that the CBH system time is the same as the mobile phone time (accurate to the second). Otherwise, a message indicating that the verification code is incorrect will be reported.
Bind your account to a mobile OTP and contact the administrator to configure multi-factor authentication. Otherwise, you cannot log in to the system. For details, see Configuring Mobile OTP Login Verification.
OTP token
After the Password or SSH Pubkey login is authenticated, select OTP token and enter the verification code.
A dynamic token must be issued to the user. For details, see OTP Token Management.
- After logging in to your bastion host, you can view system information and start O&M operations.
You can also use APIs to log in to resources managed by a bastion host. To do so, you need to obtain the specific URL.
Using an MSTSC Client to Log In to Your Bastion Host
You can use a Microsoft Terminal Services Client (MSTSC) client to log in authorized resources over your bastion host.
- Open the MSTSC dialog box.
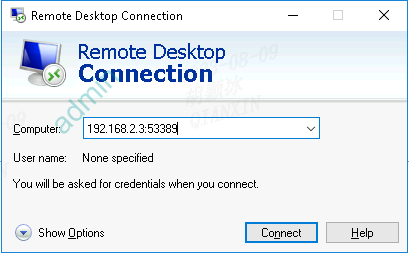
- In the displayed dialog box, enter your bastion host information in the Computer text box in the format of Bastion host IP address: 53389.
Figure 1 Configuring the computer
- Click Connect and provide the following information to complete the login:
- Username: Enter Login name of the bastion host user@Windows host resource account@Windows host resource IP address:Windows remote port (3389 by default), for example, admin@Administrator@192.168.1.1:3389.
The Windows host resource account must be a resource account that has been added to CBH and the login mode must be automatic login, or the resource account cannot be identified and O&M audit files cannot be generated. Real-time session O&M is not supported. For details, see Creating a Resource Account and Associating It with the Corresponding Resource.
- Password: Enter the password of the current bastion host user.
- Username: Enter Login name of the bastion host user@Windows host resource account@Windows host resource IP address:Windows remote port (3389 by default), for example, admin@Administrator@192.168.1.1:3389.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






