Updated on 2025-09-16 GMT+08:00
Example Scenario
User-Integrated KMS to Applications
Figure 1 Principles of user-integrated KMS to applications
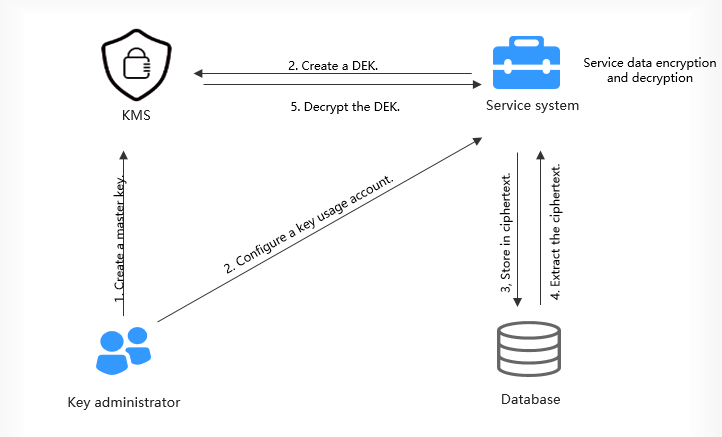

- You can use KMS to encrypt and decrypt data. Integrated SDKs need to be used. For details, see SDK Overview.
- When KMS is used in a service system, you can call APIs to enable functions such as signing data and authenticating a signature
Encrypting and Decrypting a Cloud Service Integrated with KMS
Figure 2 Principles of a cloud service integrated with KMS
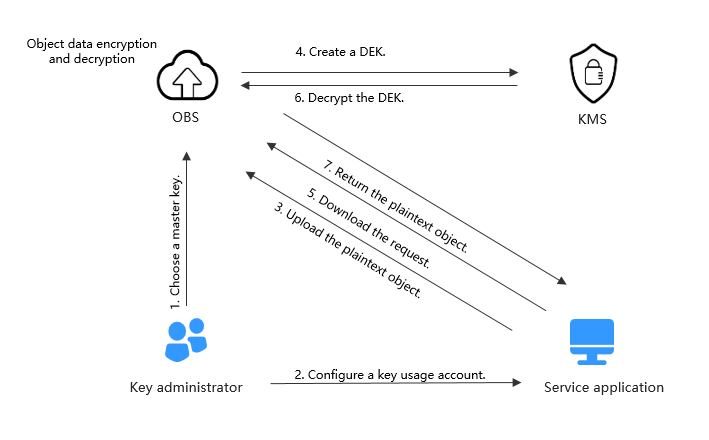

- For details about how to use KMS, see Using KMS to Encrypt and Decrypt Data for Cloud Services.
- For details about how to encrypt or decrypt a large amount of data, see Encrypting or Decrypting a Large Amount of Data.
Parent topic: KMS
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.
The system is busy. Please try again later.






