How Do I Do If the Datasource Connection Is Successfully Created but the Network Connectivity Test Fails?
Symptom
failed to connect to specified address
Fault Locating
The issues here are described in order of how likely they are to occur.
Troubleshoot the issue by ruling out the causes described here, one by one.
- Check Whether a Port Number Is Added to the End of the Domain Name or IP Address
- Check Whether the Information of the Peer VPC and Subnet Are Correct.
- Check Whether the CIDR Block of the Queue Overlaps with That of the Data Source
- Check Whether the DLI Datasource Connections Agency Access Permission Is Granted to DLI
- Check Whether the Destination Security Group Allows Access from the CIDR Block of the Queue
- Check the Route Information of the VPC Peering Connection Corresponding to an Enhanced Datasource Connection
- Check Whether VPC Network ACL Rules Are Configured to Restrict Network Access
Check Whether a Port Number Is Added to the End of the Domain Name or IP Address
The port number is required for the connectivity test.
The following example tests the connectivity between a queue and a specified RDS DB instance. The RDS DB instance uses port 3306.
The following figure shows how you should specify the IP address.

Check Whether the Information of the Peer VPC and Subnet Are Correct.
When you create an enhanced datasource connection, you need to specify the peer VPC and subnet.
For example, to test the connectivity between a queue and a specified RDS DB instance, you need to specify the RDS VPC and subnet information.

Check Whether the CIDR Block of the Queue Overlaps with That of the Data Source
The CIDR block of the DLI queue bound with a datasource connection cannot overlap the CIDR block of the data source.
You can check whether they overlap by viewing the connection logs.
Figure 3 shows an example where the CIDR block conflicts of queue A and queue B. In this example, queue B is bound to an enhanced datasource connection to data source C. Therefore, a message is displayed, indicating that the network segment of queue A conflicts with that of data source C. As a result, a new enhanced datasource connection cannot be established.
Solution: Modify the CIDR block of the queue or create another queue.
Planing the CIDR blocks for your queues helps you to avoid this problem.
Check Whether the DLI Datasource Connections Agency Access Permission Is Granted to DLI
You can determine if a connection failure is due to insufficient permissions by checking the connection logs.
Figure 4 and Figure 5 show the logs when subnet ID and route ID of the destination cannot be obtained because there is no permission.
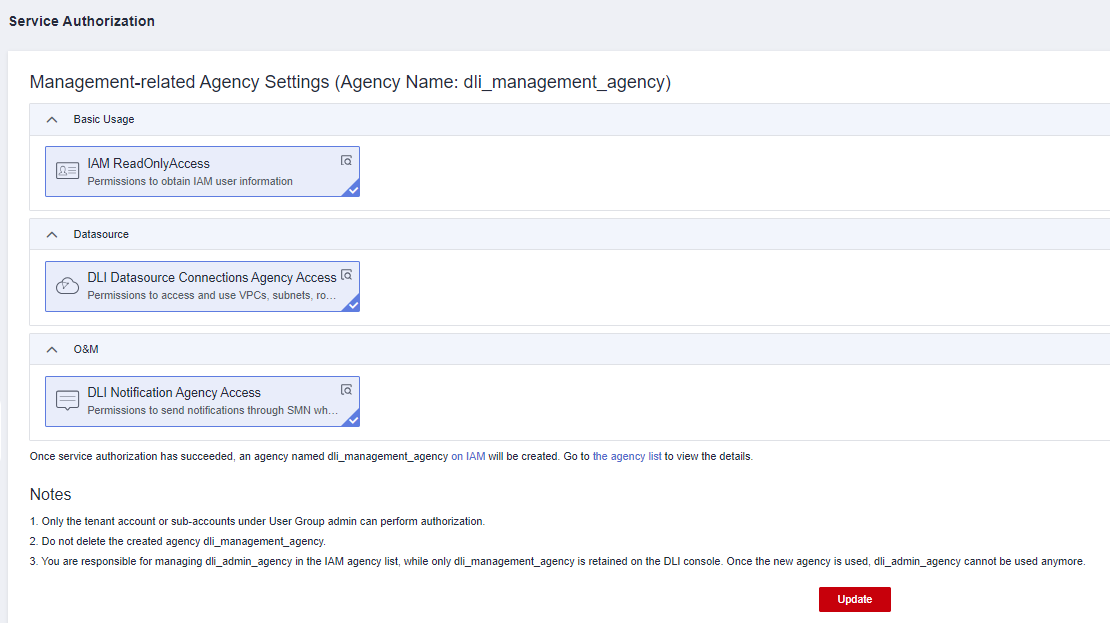
Solution: Add the DLI Datasource Connections Agency Access authorization on the Global Configuration > Service Authorization page.
Check Whether the Destination Security Group Allows Access from the CIDR Block of the Queue
- Log in to the DLI console, choose Resources > Queue Management in the navigation pane on the left. On the displayed page, select the target queue, and click
 to expand the row containing the target queue to view its CIDR block.
to expand the row containing the target queue to view its CIDR block. - On the Instance Management page of the RDS console, click the instance name. In the Connection Information area, locate Database Port to obtain the port number of the RDS DB instance.
- In the Connection Information area locate the Security Group and click the group name to switch to the security group management page. Select the Inbound Rules tab and click Add Rule. Set the priority to 1, protocol to TCP, port to the database port number, and source to the CIDR block of the DLI queue. Click OK.
Figure 7 VPC security group rules

Check the Route Information of the VPC Peering Connection Corresponding to an Enhanced Datasource Connection
Check the routing table of the VPC peering connection corresponding to the enhanced datasource connection. Check whether the CIDR block of the queue overlaps other CIDR blocks in the routing table. If it does, the forwarding may be incorrect.
- Obtain the ID of the VPC peering connection created for the enhanced datasource connection.
Figure 8 Obtaining the VPC peering connection ID

- View the information about the VPC peering connection on the VPC console.
Figure 9 Viewing a VPC peering connection
 Figure 10 Viewing the CIDR block of the queue
Figure 10 Viewing the CIDR block of the queue
- View the route table information of the VPC corresponding to the queue.
Figure 11 Viewing the destination addresses in the routing table

Check Whether VPC Network ACL Rules Are Configured to Restrict Network Access
Check whether an ACL is configured for the subnet corresponding to the datasource connection and whether the ACL rules restrict network access.
For example, if you set a CIDR block whose security group rule allows access from a queue and set a network ACL rule to deny access from that CIDR block, the security group rule does not take effect.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.









