Notice of the NGINX Ingress Controller Vulnerabilities (CVE-2025-1974, CVE-2025-1097, CVE-2025-1098, CVE-2025-24513, and CVE-2025-24514)
The Kubernetes community recently identified five security vulnerabilities (CVE-2025-1974, CVE-2025-1097, CVE-2025-1098, CVE-2025-24513, and CVE-2025-24514) that could potentially allow attackers to run unauthorized code or interrupt services.
- CVE-2025-1974: This high-risk vulnerability was discovered in the NGINX Ingress Controller. It enables unauthenticated attackers to access the pod network under specific conditions and execute arbitrary code in the context of the NGINX Ingress Controller, potentially leading to sensitive information exposure.
- CVE-2025-1097: This high-risk vulnerability was discovered in the NGINX Ingress Controller where the auth-tls-match-cn annotation in the ingress objects can be used to inject configuration into nginx. This can lead to arbitrary code execution in the context of the NGINX Ingress Controller and disclosure of secrets accessible to the controller.
- CVE-2025-1098: This high-risk vulnerability was discovered in the NGINX Ingress Controller where the mirror-target and mirror-host annotations in the ingress objects can be used to inject configuration into nginx. This can lead to arbitrary code execution in the context of the NGINX Ingress Controller and disclosure of secrets accessible to the controller.
- CVE-2025-24513: This vulnerability was discovered in the NGINX Ingress Controller. It allows the malicious data provided by attackers to be included in a file name by the admission controller feature, potentially leading to directory traversal within containers. This could result in denial of service (DoS) or limited disclosure of secret objects when combined with other vulnerabilities.
- CVE-2025-24514: This high-risk vulnerability was discovered in the NGINX Ingress Controller where the auth-url annotation in the ingress objects can be used to inject configuration into nginx. This can lead to arbitrary code execution in the context of the NGINX Ingress Controller and disclosure of secrets accessible to the controller.
Description
|
Type |
CVE-ID |
Severity |
Discovered |
|---|---|---|---|
|
Code execution |
High |
2025-03-24 |
|
|
Code execution |
High |
2025-03-24 |
|
|
Code execution |
High |
2025-03-24 |
|
|
Code execution |
High |
2025-03-24 |
|
|
Denial of service |
Medium |
2025-03-24 |
Impact
These vulnerabilities affect the open source NGINX Ingress Controller of the following versions:
- < v1.11.0
- v1.11.0–v1.11.4
- v1.12.0
CCE NGINX Ingress Controller of version 3.0.32 or earlier is affected by these vulnerabilities. For details about the mapping between this add-on and open-source versions, see NGINX Ingress Controller Release History.
Identification Method
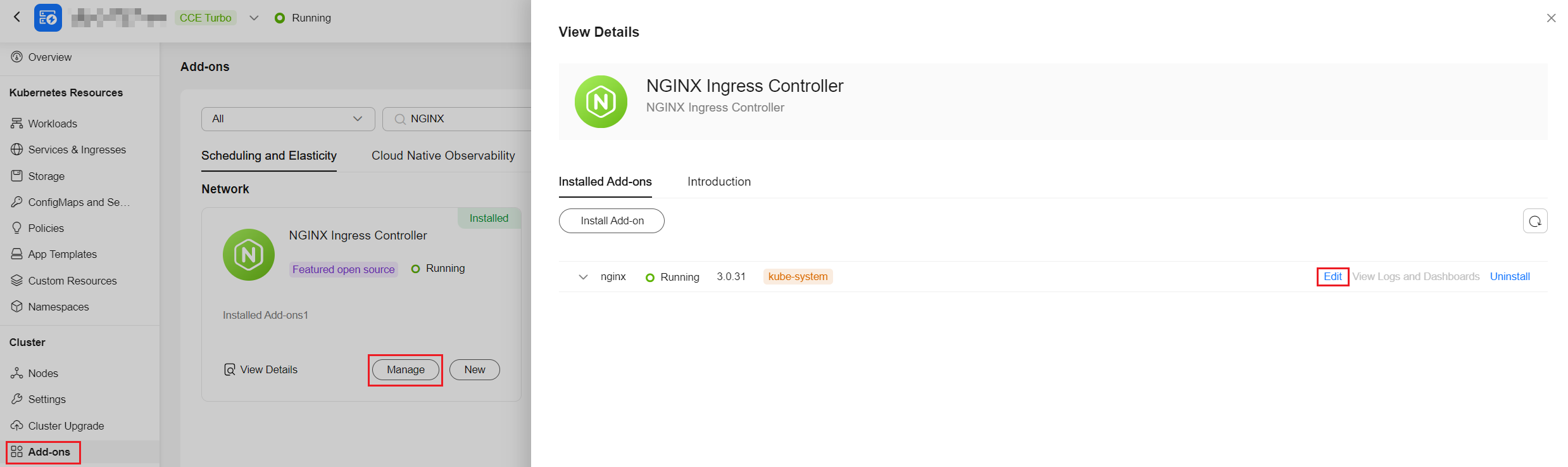
- Go to Add-ons and check whether the NGINX Ingress Controller add-on has been installed and its version.
Figure 1 Viewing the installed add-on version
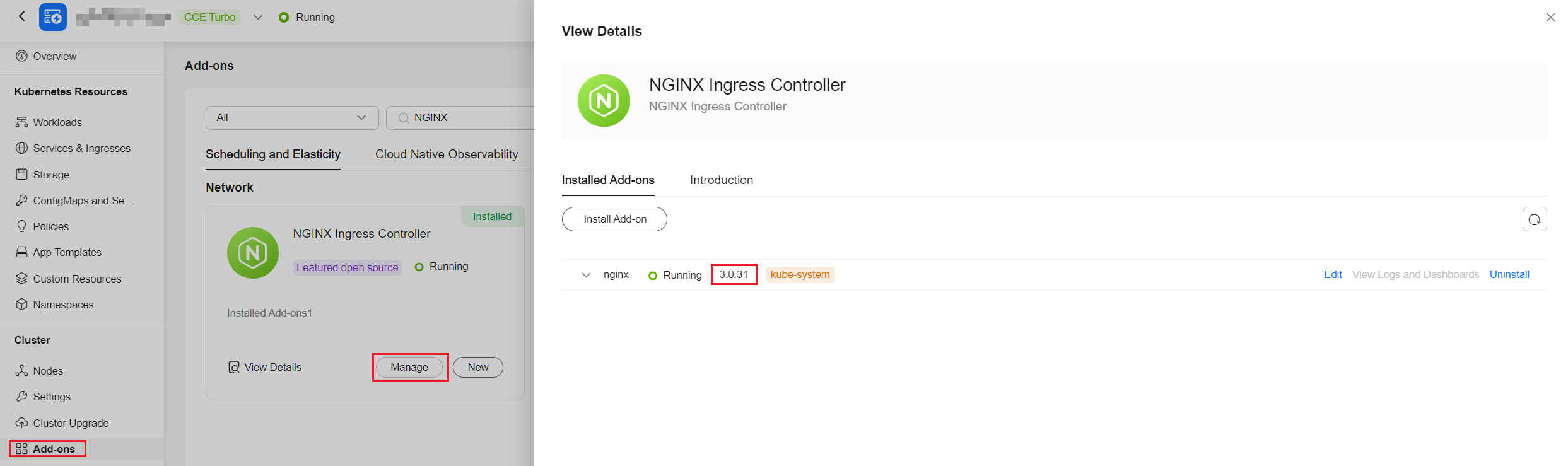
- If the add-on version is 3.0.32 or earlier, it is affected by these vulnerabilities. Otherwise, the add-on is safe from these vulnerabilities.
Solution
CCE has released a new NGINX Ingress Controller add-on to fix these vulnerabilities. Upgrade the add-on to v3.0.34 or later. For details, see NGINX Ingress Controller Release History.
The vulnerability fixing involves CCE clusters of versions ranging from v1.25 to v1.31. If your CCE cluster version is earlier than v1.25, upgrade the cluster and then NGINX Ingress Controller.
- To mitigate the risks associated with the CVE-2025-1974 vulnerability, disable admission check in NGINX Ingress Controller. To do so, do as follows:
- If the NGINX Ingress Controller version is earlier than 2.4.6, admission check is disabled by default. No additional action is required to mitigate the risks caused by these vulnerabilities.
- Disable admission check during off-peak hours.
- Log in to the CCE console and click the cluster name to access the cluster console.
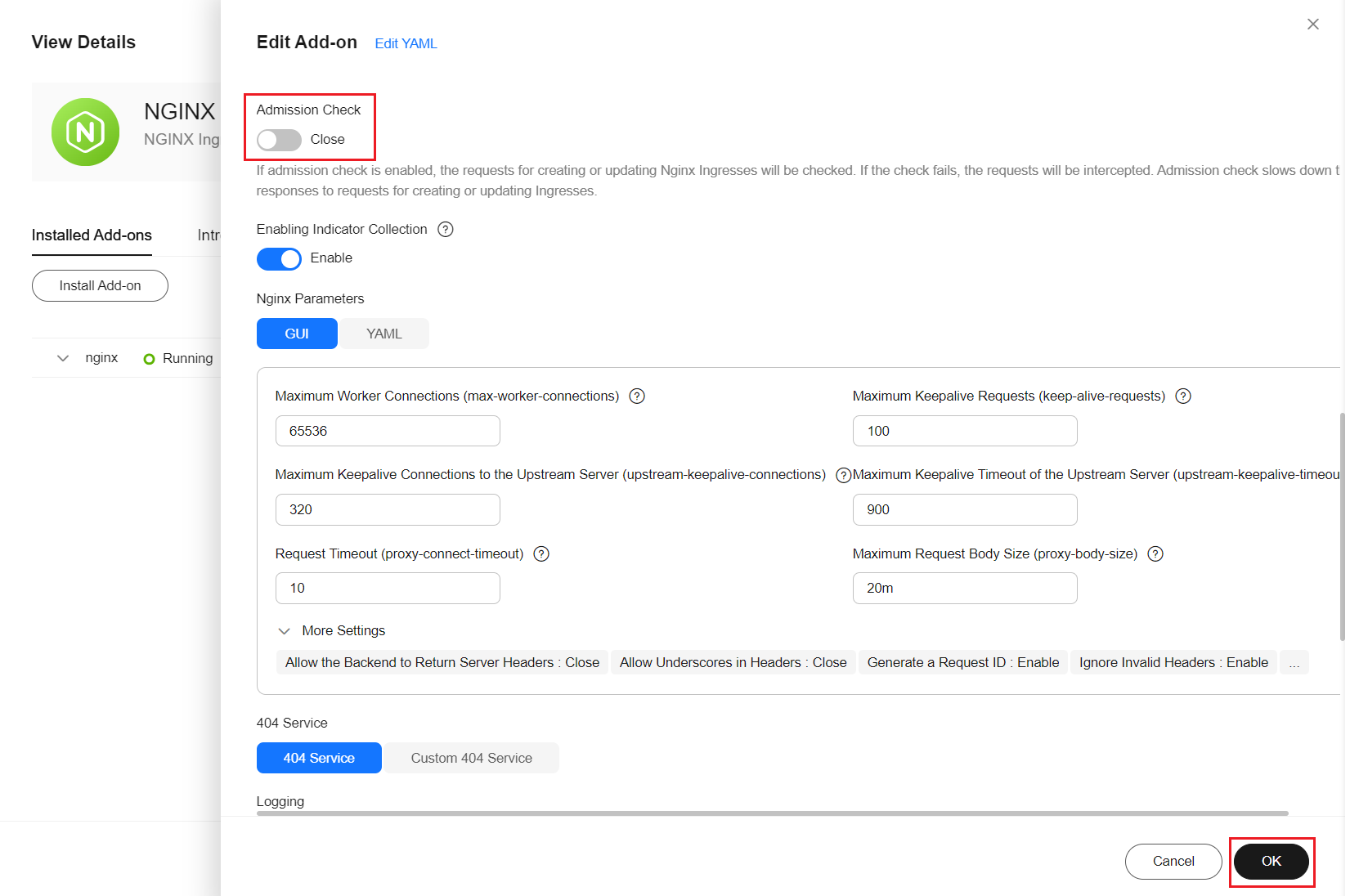
- In the navigation pane, choose Add-ons. In the right pane, find the NGINX Ingress Controller add-on and click Manage. In the window that slides out from the right, select the add-on version that is affected by the vulnerability and click Edit.
Figure 2 Managing the add-on
- Disable Admission Check and click OK. Wait until the add-on status becomes normal.
Figure 3 Disabling admission check
- Upgrade NGINX Ingress Controller to the specified version with these vulnerabilities fixed. Then you can enable admission check.

Disabling admission check in NGINX Ingress Controller will bypass the pre-verification of ingress configurations, which may lead to configuration errors and affect service reliability and stability. After disabling the admission check, ensure the ingress configuration is valid when creating or updating the ingress. Verify the configuration thoroughly in a test environment before deploying it to production.
- For CVE-2025-1097, CVE-2025-1098, and CVE-2025-24514, disabling the admission check mitigates the vulnerability risk. Before fixing these vulnerabilities, grant only the permissions for creating and managing ingresses to trusted users based on the principle of least privilege. For details, see Namespace Permissions (Kubernetes RBAC-based).
- Log in to the CCE console.
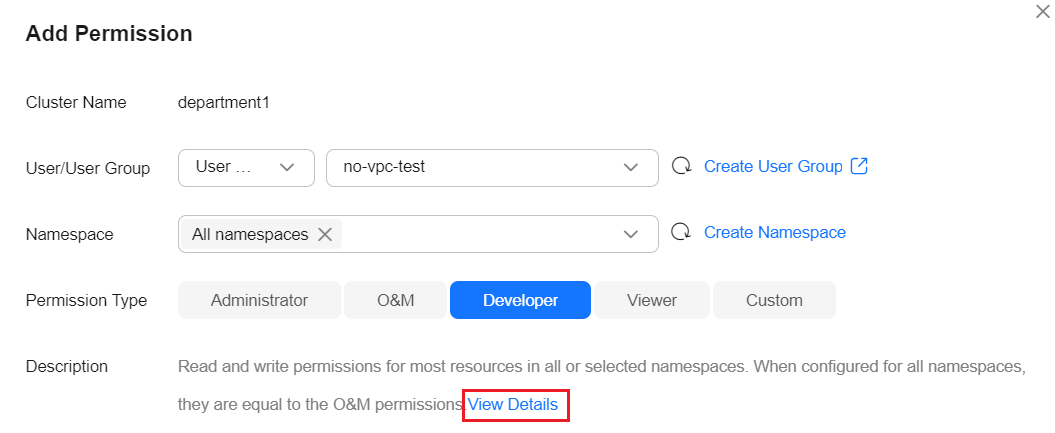
- Go to the Permissions page, select the target cluster, and click Add Permission in the upper right corner.
- Specify the user or user group, namespace, and permission type to be granted, and click View Details.
- Click Clone.
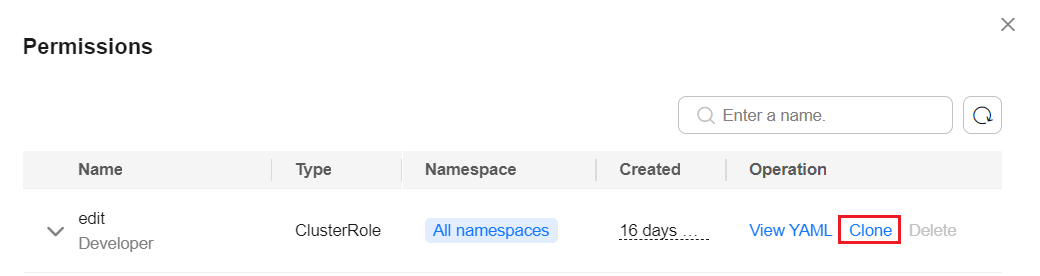
- Enter the name of the new custom permission.
- Delete the ingress role and click OK.
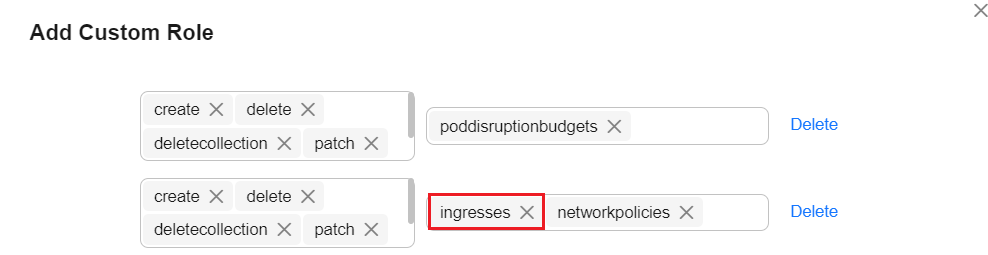
- Return back to the page for adding permissions, set Permission Type to Custom, and select the custom permission created in the previous step.
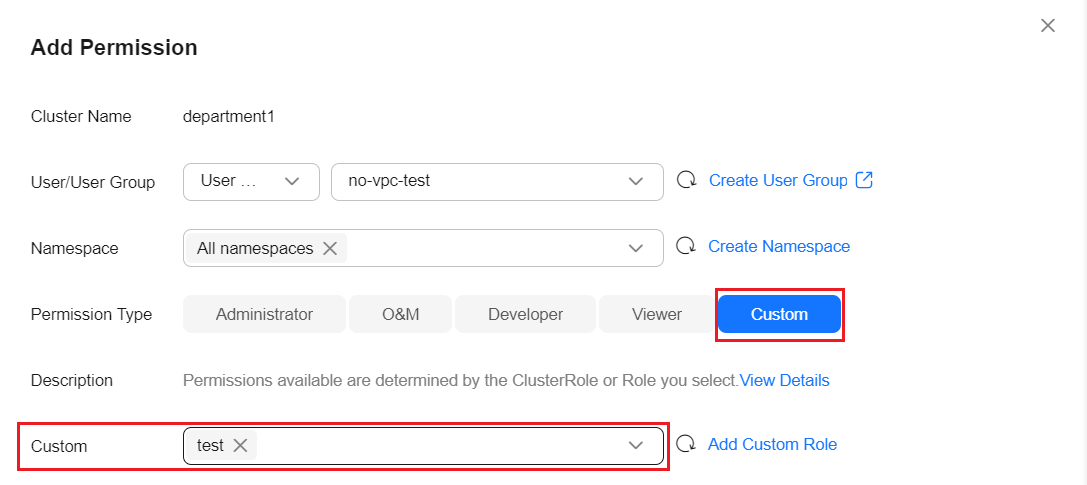
- Click OK.
Helpful Links
- Release history of the open source NGINX Ingress Controller v1.11.5: https://github.com/kubernetes/ingress-nginx/releases/tag/controller-v1.11.5
- Release history of the open source NGINX Ingress Controller v1.12.1: https://github.com/kubernetes/ingress-nginx/releases/tag/controller-v1.12.1
- Kubernetes disclosure notice of CVE-2025-1974: https://kubernetes.io/blog/2025/03/24/ingress-nginx-cve-2025-1974
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.