Adding and Editing an Incident
Scenarios
This section describes how to add or edit an incident.
- Adding an incident: If you identify an attack or a fault that needs to be handled, you can add an incident for tracking and handling the attack or fault.
- Editing an incident: If information such as the incident status, severity, and owner changes, you can edit the incident accordingly.
Adding an Incident
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose .
Figure 2 Accessing the Incidents page
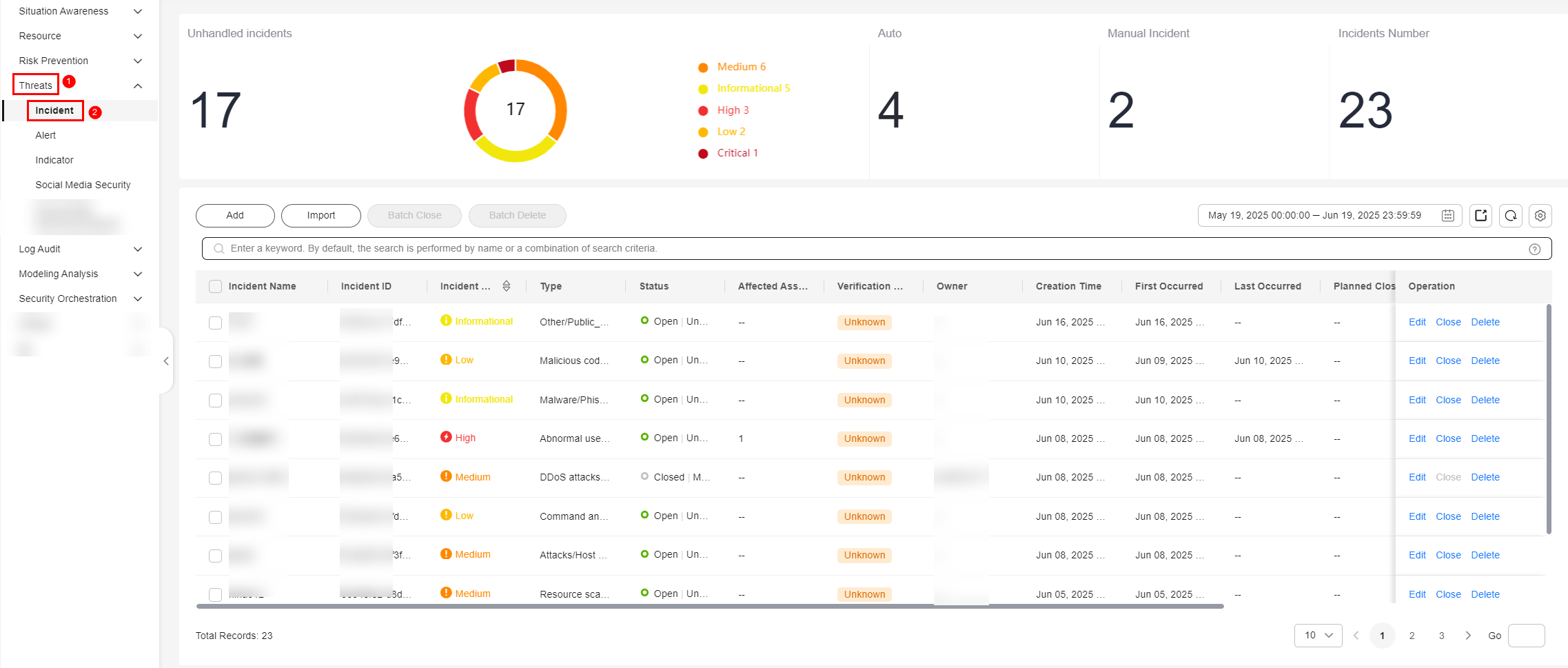
- On the Incidents page, click Add. On the displayed Add page, set parameters as described in Table 1.
Table 1 Parameters for adding an incident Parameter
Description
Basic Information
Incident Name
Custom incident name. The value must contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 2,550 characters
Type
Select an incident type from the drop-down list.
(Optional) Service ID
Enter the service ID corresponding to the incident.
Incident Severity
Select a severity level.
The options are Critical, High, Medium, Low, and Informational.
Status
Select an incident status.
The options are Open, Blocked, and Closed.
- Open: Select Open if the incident has not been handled or the fault still exists.
- Blocked: Select Blocked if the incident cannot be handled or resolved due to a specific reason.
- Closed: Select Closed if the incident has been handled, the issue has been resolved, or the fault no longer exists.
(Optional) Owner
Primary owner of the incident.
Data Source Product Name
Select the name of the data source product.
Data Source Type
Select a data source type. For example, if the source is a cloud service, select Cloud Service.
Timeline
First Occurrence Time
Configure the time when the incident occurred for the first time.
(Optional) Last Occurrence Time
Configure the time when the incident occurred last time.
(Optional) Planned Closure Time
Time to close the incident.
Other
(Optional) Verification Status
Verification status of the incident to identify the accuracy of the incident.
- Unknown: It is unclear whether the incident may lead to an attack.
- Attack succeeded: The incident was triggered by a successful attack.
- Attack failed: The incident was triggered by a failed attack.
(Optional) Stage
Select the incident phase.
- Preparation: Prepare resources to process incidents.
- Detection and analysis: Detect and analyze the cause of an incident.
- Containment, extradition, and recovery: Handle an incident.
- Post Incident Activity: Follow-up activities.
(Optional) Debugging data
Whether the incident can be used as the debugging data of the workflow trigger source. For more details about workflows, see Overview.
- Yes: The incident can be used as the trigger source for debugging the workflow. The Data Class is Incident for the workflow.
- No: The incident cannot be used as the debugging data of the workflow.
(Optional) Labels
Label of the incident. For example, "mining pool", "External connection." Use commas (,) to separate multiple labels.
Description
Incident description. The value can contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 10,240 characters.
- Click OK. You can check the added incident by referring to Viewing Incidents. Path: In the navigation pane on the left, choose .
Editing an Incident
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 3 Workspace management page

- In the navigation pane on the left, choose .
Figure 4 Accessing the Incidents page

- In the incident list, locate the row that contains the target incident and click Edit in the Operation column.
- On the Edit page that is displayed, edit incident parameters.
Table 2 Parameters for editing an incident Parameter
Description
Basic Information
Incident Name
Custom incident name. The value must contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 2,550 characters
Incident Type
Incident type
(Optional) Service ID
Enter the service ID corresponding to the incident.
Incident Level
Select a severity level. The options are Critical, High, Medium, Low, and Informational.
Status
Select an incident status.
The options are Open, Blocked, and Closed.
- Open: Select Open if the incident has not been handled or the fault still exists.
- Blocked: Select Blocked if the incident cannot be handled or resolved due to a specific reason.
- Closed: Select Closed if the incident has been handled, the issue has been resolved, or the fault no longer exists.
(Optional) Owner
Primary owner of the incident.
Data Source Name
Name of the data source, which cannot be changed
Data Source Type
Type of the data source, which cannot be changed
Timeline
First Occurrence Time
Time when the incident occurred for the first time.
(Optional) Last Occurrence Time
Time when the incident occurred last time.
(Optional) Planned Closure Time
Time to close the incident.
Other
(Optional) Verification Status
Verification status of the incident to identify the accuracy of the incident.
- Unknown: It is unclear whether the incident may lead to an attack.
- Attack succeeded: The incident was triggered by a successful attack.
- Attack failed: The incident was triggered by a failed attack.
(Optional) Phase
Incident phase.
- Preparation: Prepare resources to process incidents.
- Detection and analysis: Detect and analyze the cause of an incident.
- Contain, extradition, and recovery: Handle an incident.
- Post Incident Activity: Follow-up activities.
(Optional) Debugging data
Whether the incident can be used as the debugging data of the workflow trigger source. For more details about workflows, see Overview.
- Yes: The incident can be used as the trigger source for debugging the workflow. The Data Class is Incident for the workflow.
- No: The incident cannot be used as the debugging data of the workflow.
(Optional) Label
Label of the incident. For example, "mining pool", "External connection." Use commas (,) to separate multiple labels.
Description
Incident description. The value can contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 10,240 characters.
- Click OK. The incident editing is complete. You can check the incident details by referring to Viewing Incidents. Path: In the navigation pane on the left, choose .
Related Operations
- Viewing Incidents: On the Incidents page in SecMaster, you can check the incident list for the last 360 days. The list includes the incident name, type, severity, and occurrence time of each incident. You can customize filters to quickly search for a specific incident by its name, severity, occurrence time, and other attributes.
- Importing and Exporting Incidents: You can export incident details to a local PC and easily share information with other departments. A maximum of 9,999 incident records can be exported.
- Closing and Deleting an Incident: You can close and delete an incident.
- Converting an Alert into an Incident or Associating an Alert with an Incident: SecMaster analyzes alerts it aggregates from other services. If SecMaster detects attacks or serious threats, you can convert such alerts into incidents or associate such alerts with certain incidents. For the differences and relationships between alerts and incidents, see Relationships Between Alerts and Incidents.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





