Converting an Alert into an Incident or Associating an Alert with an Incident
Scenarios
SecMaster analyzes alerts it aggregates from other services. During the analysis, if SecMaster detects attacks or serious threats, it converts such alerts into incidents or associates such alerts with certain incidents.
This section describes how to convert an alert into an incident and how to associate an alert with an incident.
Relationships Between Alerts and Incidents
This part describes the meanings and differences between alerts and incidents, reasons for converting alerts into incidents, and reasons for associating alerts with incidents.
- Meanings and Differences Between Alerts and Incidents
- Causes for converting alerts into incidents or associating alerts with incidents
An alert is a notification generated when a system or service becomes abnormal or a potential fault occurs. These exceptions may directly affect service availability. So alerts must be handled in a timely manner to prevent service exceptions. When an alert is generated, you need to take corresponding measures to rectify the fault. Otherwise, services may be abnormal due to these exceptions or faults.
An incident is a notification generated when the system or service is running properly. It may involve some important status changes, but may not cause service exceptions. So incidents do not need to be handled. They are mainly used to analyze and locate problems.
Converting an Alert into an Incident
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose .
Figure 2 Alerts
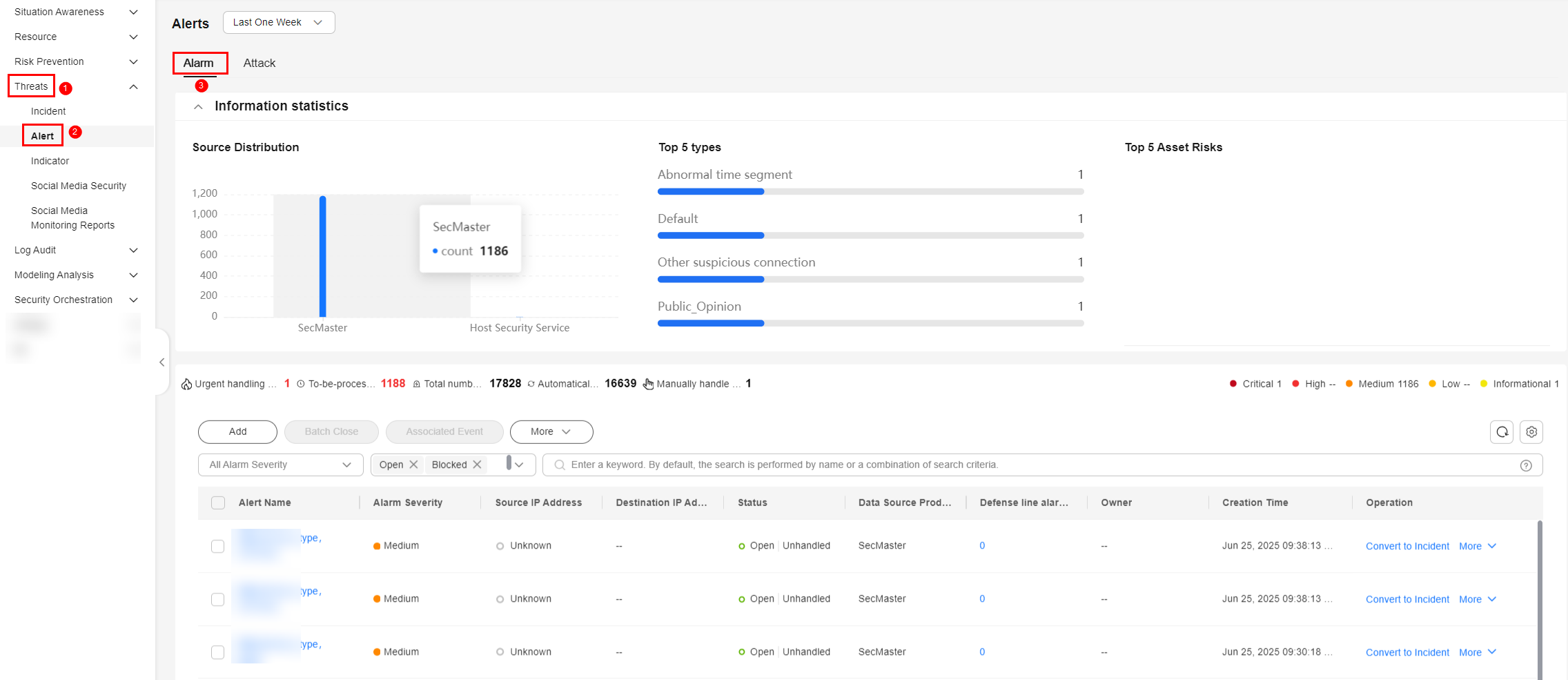
- In the alert list, locate the row that contains the target alert, click Convert to Incident in the Operation column. The Convert to Incident page is displayed on the right.
Alternatively, you can click Alert-to-Incident on top of the details page of the alert.
- On the Convert to Incident page, specify Incident Name and Type.
The incident name is automatically set to the name of the current alert. This name can be modified.
- Click OK.
- In the navigation pane on the left, choose . On the displayed page, view the incident information. For details, see Viewing Incidents.
Associating an Alert with an Incident
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 3 Workspace management page

- In the navigation pane on the left, choose .
Figure 4 Alerts

- In the alert list, select the alerts you want to associate and click Associated Event above the list. The Bind Incident dialog box is displayed.
- In the dialog box displayed, select the target incidents and click OK.
After the association is complete, click the type of the target alert in the alert list. On the alert details page displayed, choose Associated Incidents and check the association details.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





