Viewing and Handling Security Risks in a Cluster
Scenarios
HSS can present risks in the risk view or image view. This helps you comprehensively learn the risk status of the cluster environment and implement one-stop management of the cluster security posture.
- Risk view: View all the scan results of a risk, for example, a system vulnerability, application vulnerability, emergency vulnerability, configuration risk, IaC risk, or security and compliance issue.
- Cluster view: View the scan results of a cluster, including its system vulnerabilities, application vulnerabilities, emergency vulnerabilities, configuration risks, and security and compliance issues.
This section describes how to view and handle cluster security risks in the risk view and the cluster view.
Viewing and Handling Cluster Environment Risks in the Risk View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Cluster Environment.
- On the Risk View tab page, view and handle all types of security risks. They include:
- System vulnerabilities
OS vulnerability scan results.Figure 1 System vulnerabilities
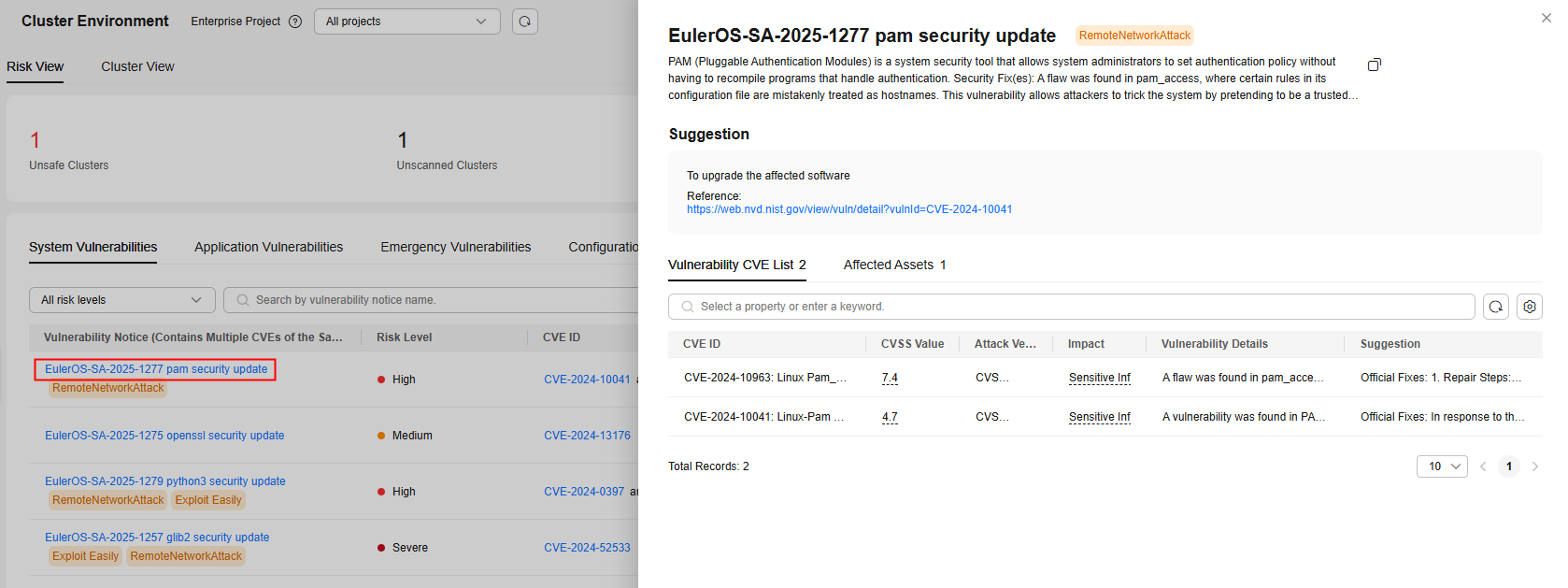
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, CVE details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Application vulnerabilities
Application software vulnerability scan results.
Figure 2 Application vulnerabilities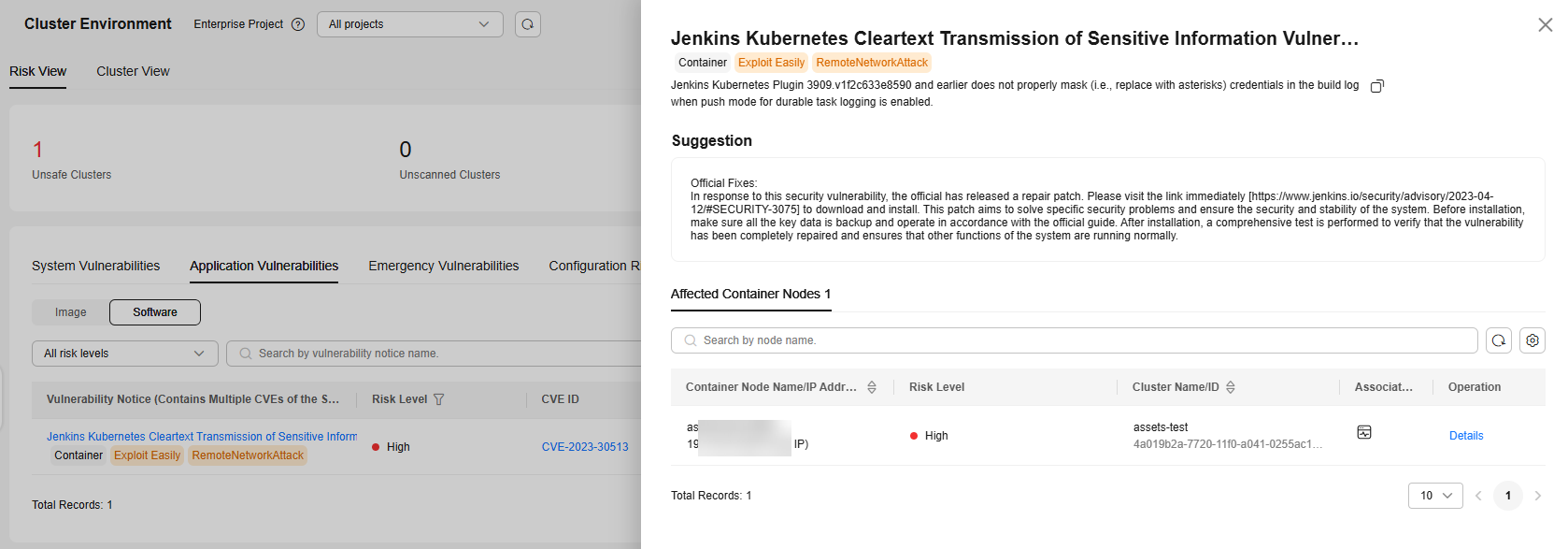
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Emergency vulnerabilities
The emergency vulnerability list shows all the vulnerabilities of this type that can be detected by HSS.Figure 3 Emergency vulnerabilities
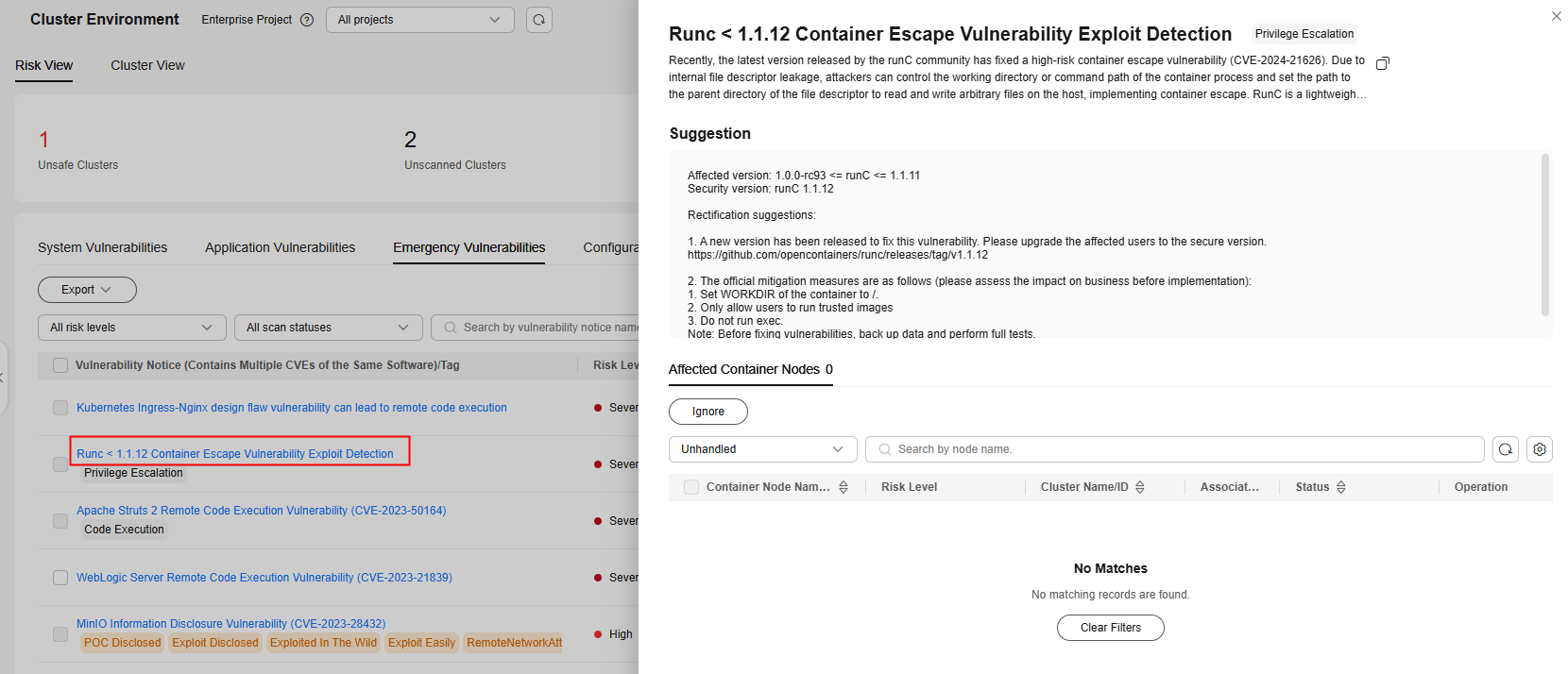
If the value of Affected Containers/Container Nodes is not 0 for an emergency vulnerability, there are containers or container nodes having emergency vulnerabilities. Click a vulnerability notice name to go to the details page. View the notice details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Configuration risks
The configuration risk list shows all the configuration risks that can be detected by HSS.Figure 4 Configuration risks
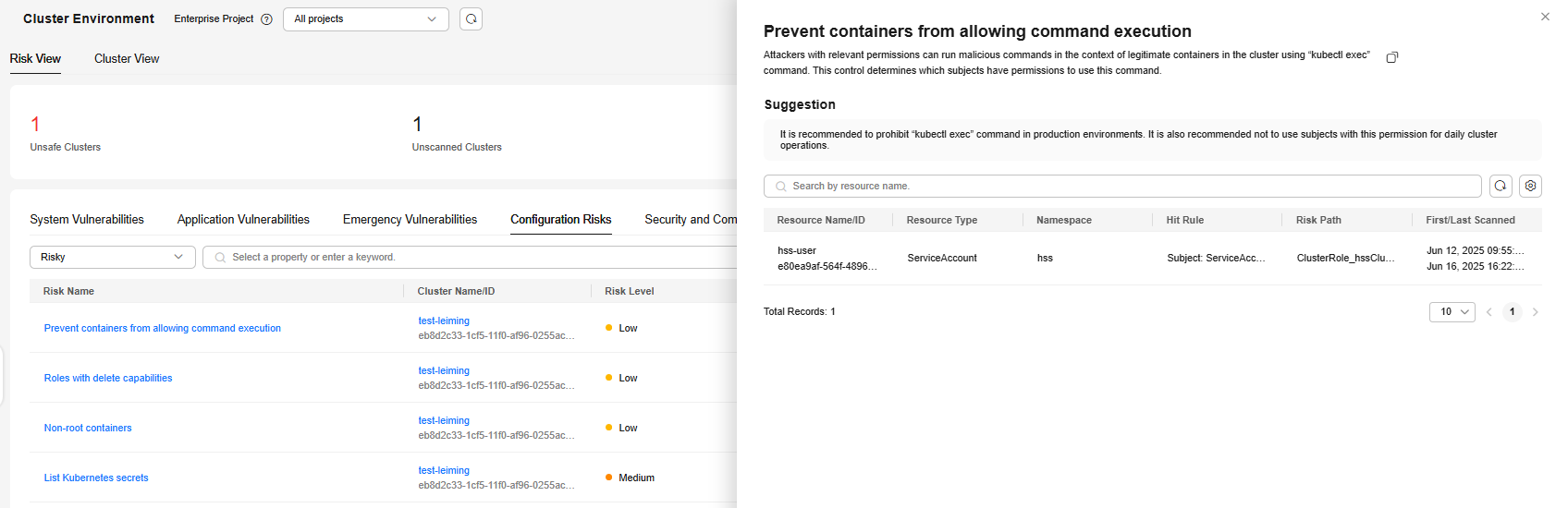
If the value of Affected Resources is not 0 for a configuration risk, there are Kubernetes resources having risks. Click a risk name. On the risk details page, view the suggestion and the information about affected resources, such as the resource names, namespaces, hit rules, and paths. You can rectify the configuration risks based on the information.
- Security and compliance
The security and compliance list shows all the issues of this type that can be detected by HSS.Figure 5 Security and compliance
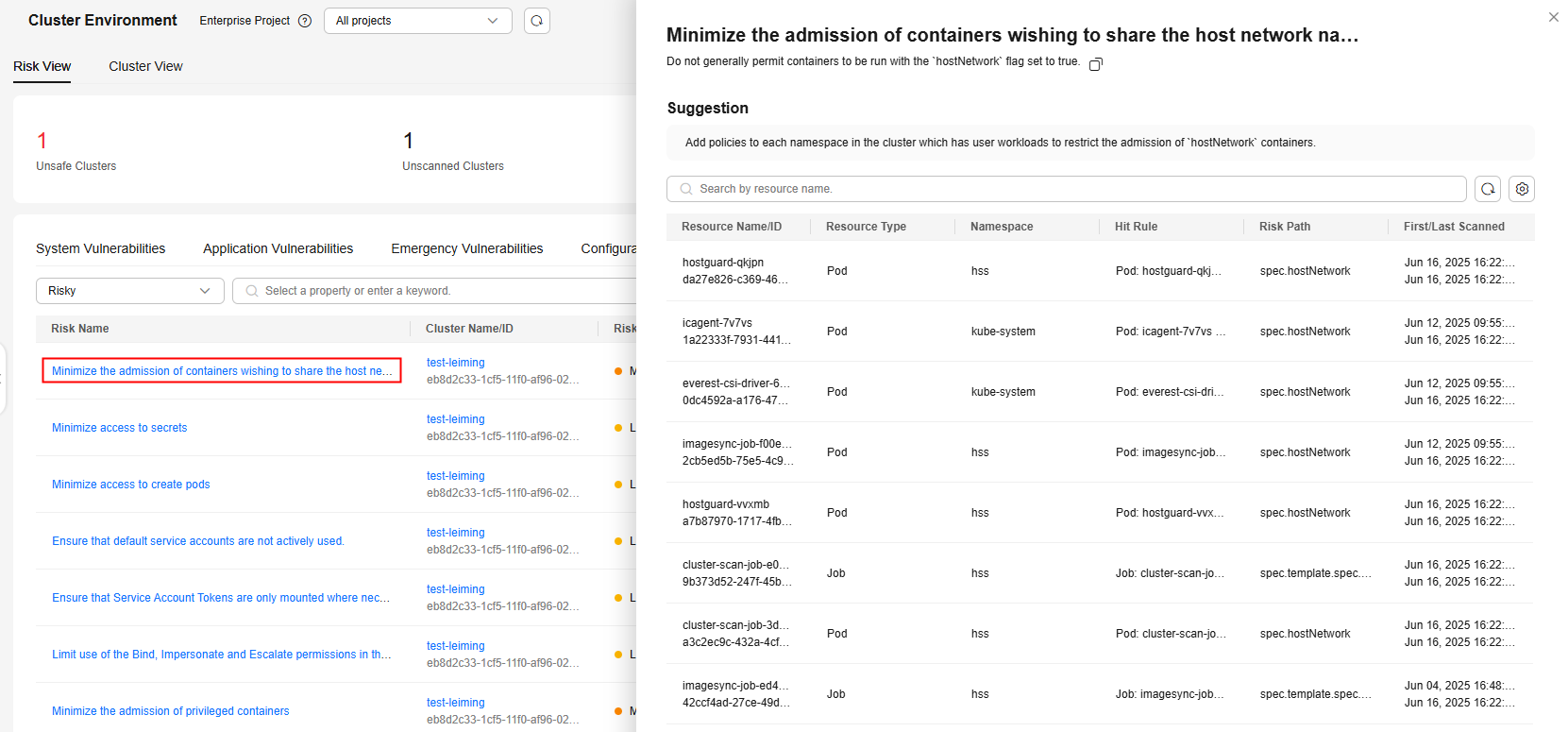
If the value of Affected Resources is not 0 for a security and compliance issue, there are Kubernetes resources having risks. Click a risk name. On the risk details page, view the suggestion and the information about affected resources, such as the resource names, namespaces, hit rules, and paths. You can rectify the security and compliance issue based on the information.
- IaC risks
IaC scan results.
Figure 6 IaC risks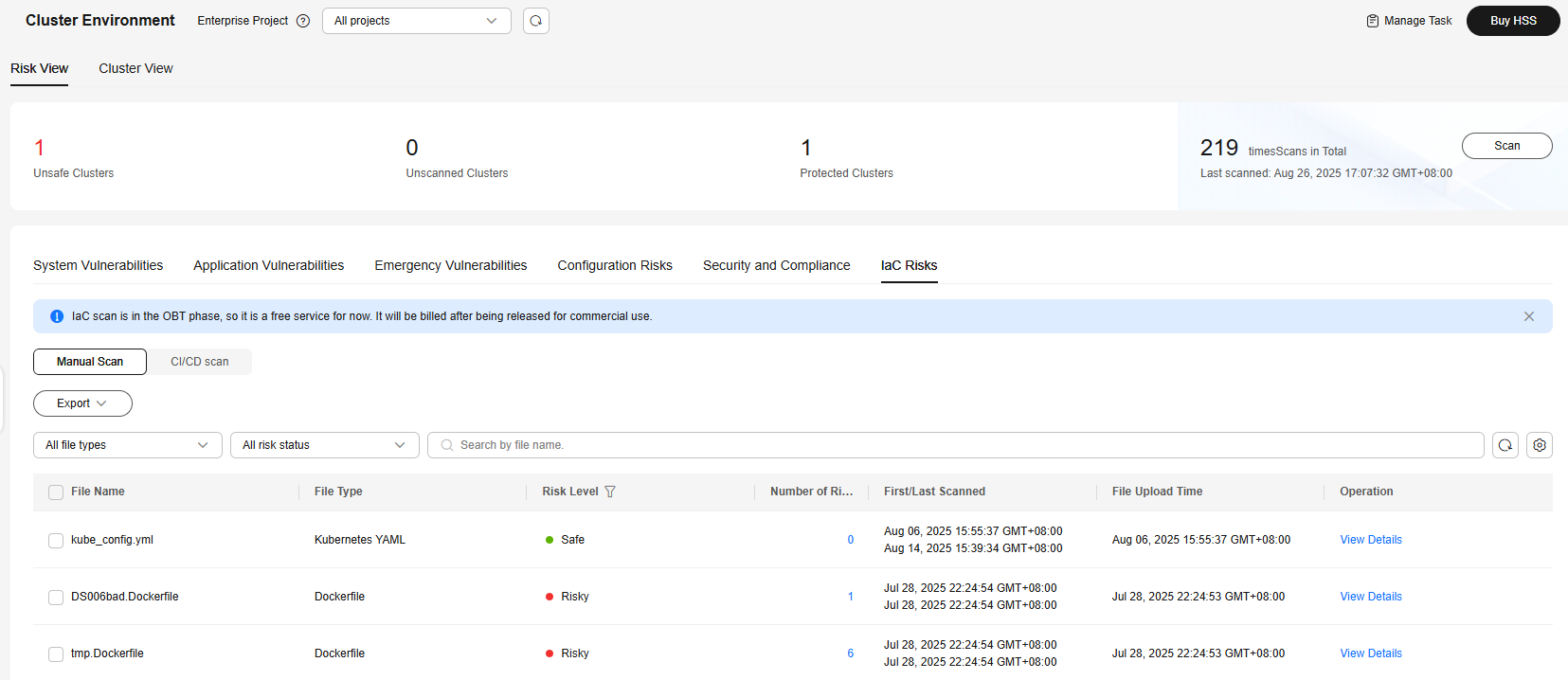
IaC scan results are displayed in the Manual Scan or CI/CD scan view. The Manual Scan view shows the scan results of the IaC files that you manually upload on the Cluster Environment page. The CI/CD Scan view shows the scan results of the IaC files that are automatically scanned when you integrate the scan plug-in into the Jenkins project.
If Risky is displayed in the Risk Level column of a file, the file is insecure.
To view the check results of a file, click View Details in the Operation column. On the details page, view the risk name, risk level, risk description, building instruction, and suggestion.
- System vulnerabilities
Viewing and Handling Cluster Environment Risks in the Cluster View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Cluster Environment.
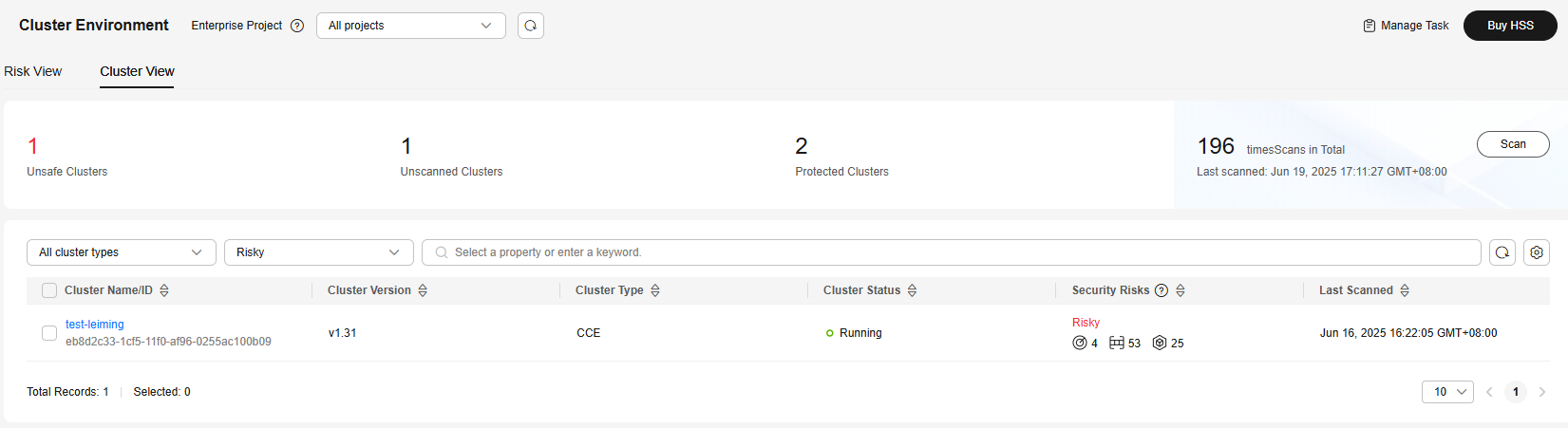
- Click Cluster View.
Figure 7 Cluster view
- If Risky is displayed in the Security Risks column of a cluster, hover the cursor over the cell to view the risk distribution. Click the number of a risk to go to the cluster risk details page.
Figure 8 Risk distribution
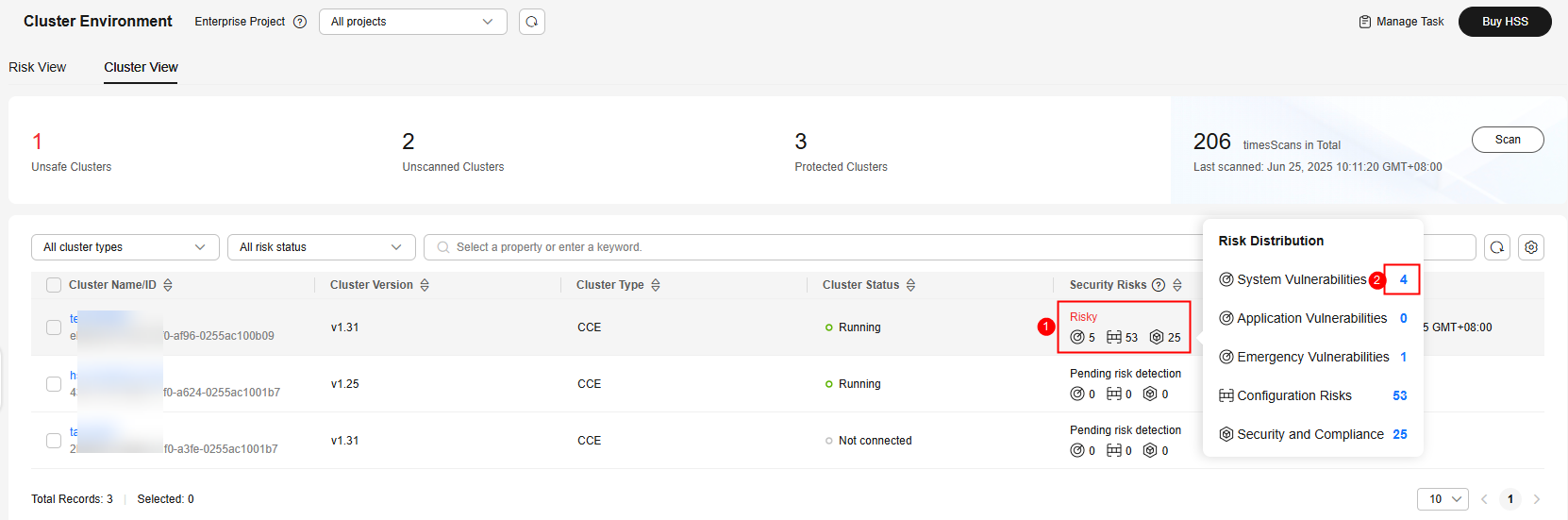
- View and handle risks. They include:
- System vulnerabilities
OS vulnerability scan results.Figure 9 System vulnerabilities
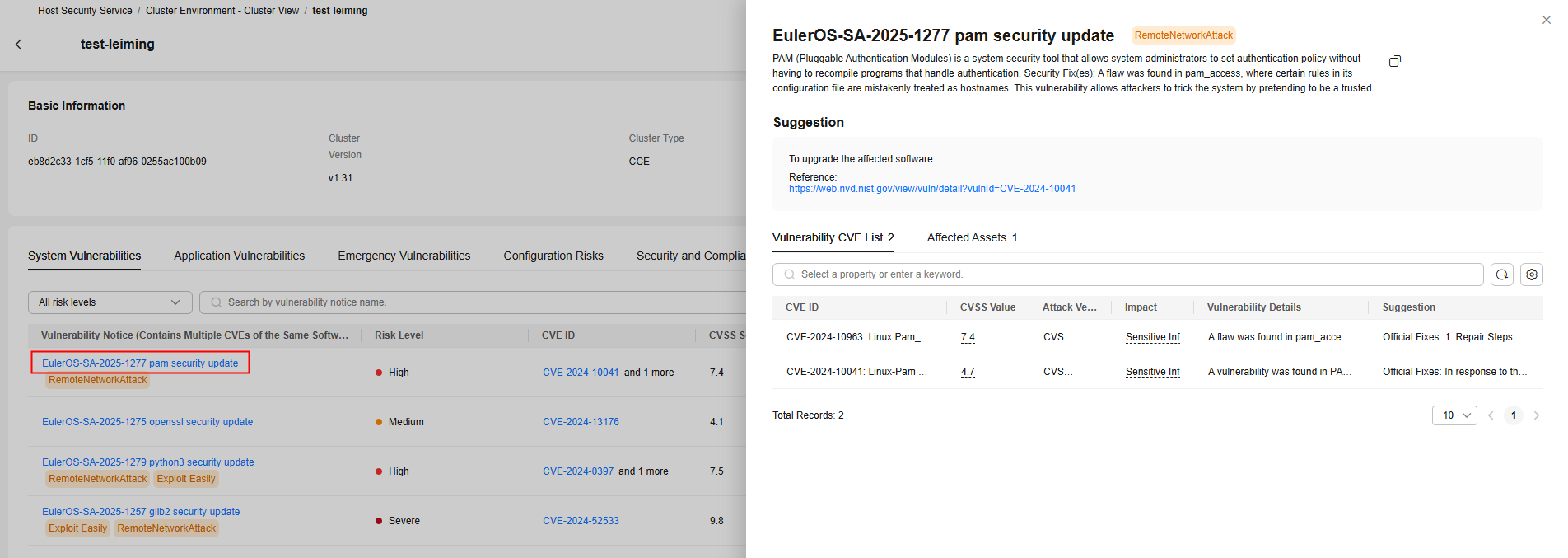
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, CVE details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Application vulnerabilities
Application software vulnerability scan results.
Figure 10 Application vulnerabilities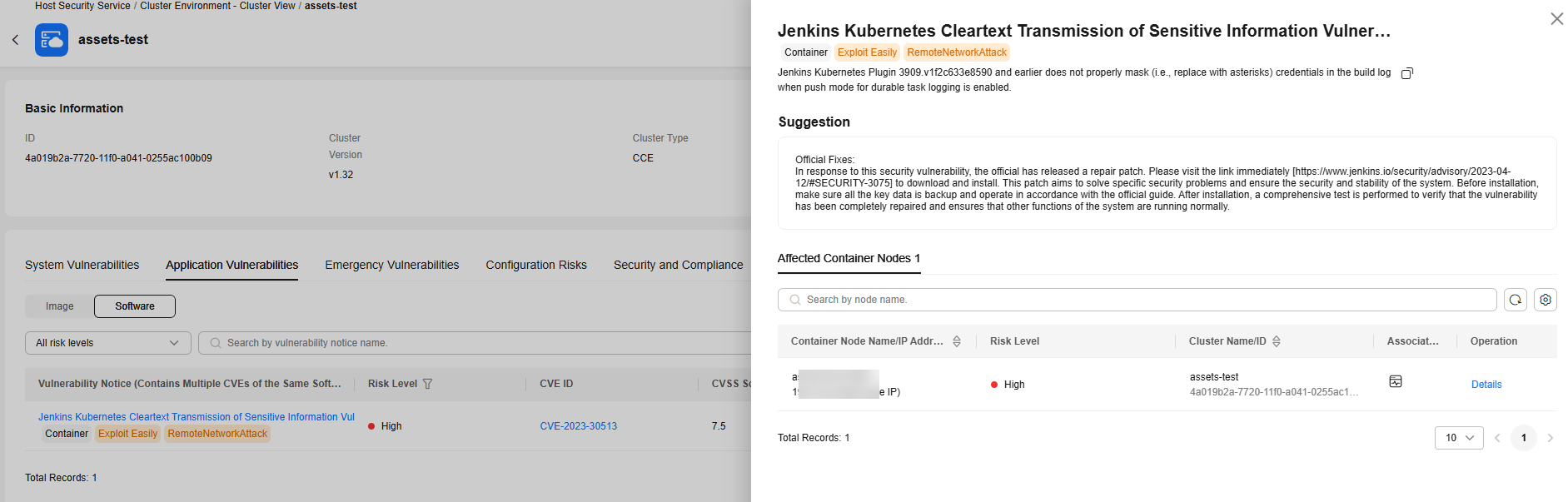
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Emergency vulnerabilities
The emergency vulnerability list shows the emergency vulnerabilities of container assets.Figure 11 Emergency vulnerabilities
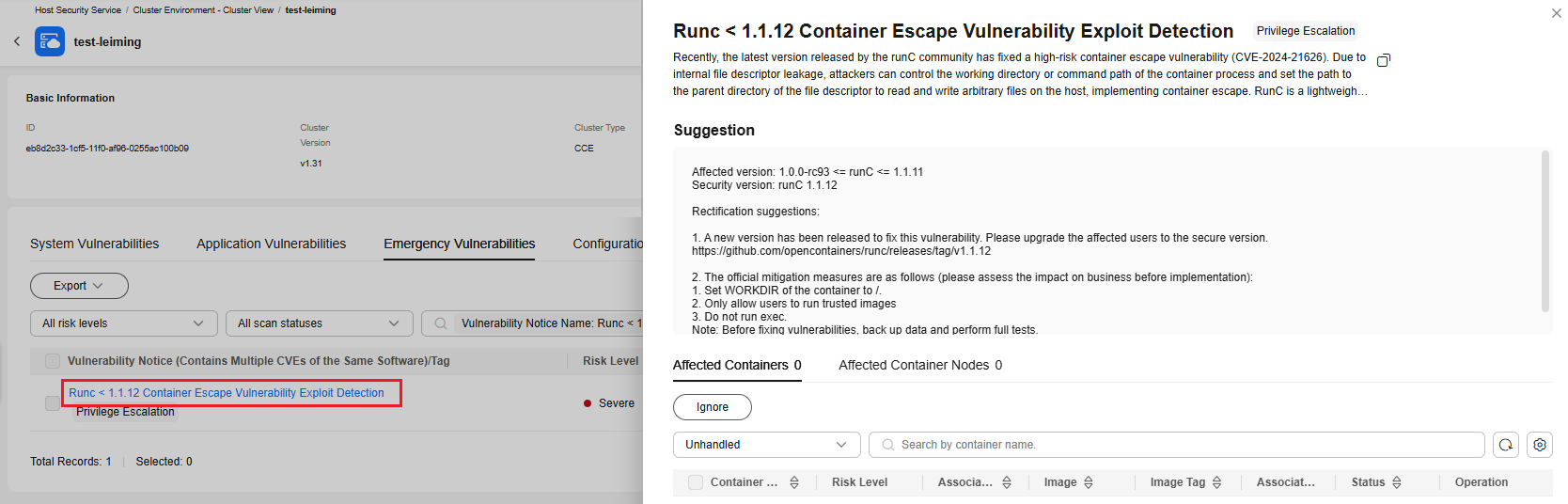
Click a vulnerability notice name to go to the details page. View the notice details, suggestions, and affected assets. You can fix the vulnerabilities based on the suggestions.
- Configuration risks
The configuration risk list shows all the configuration risks that can be detected by HSS.Figure 12 Configuration risks
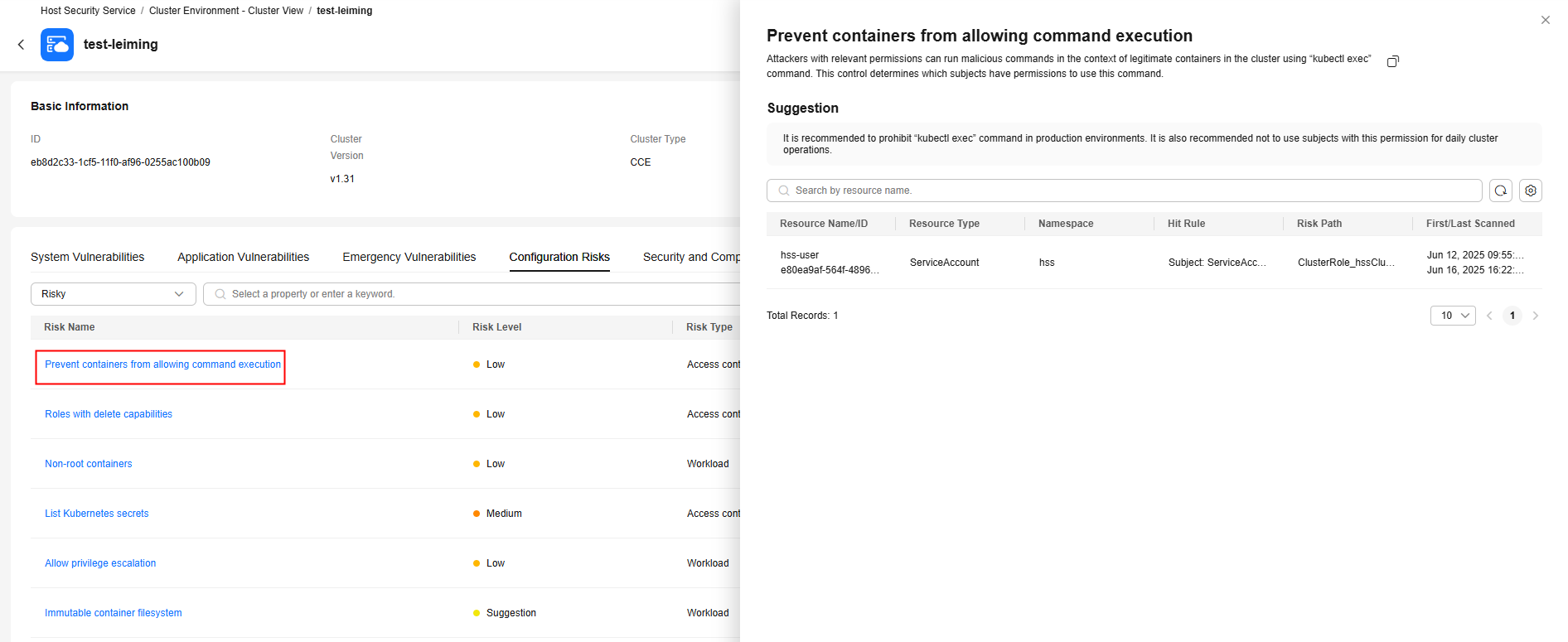
If the value of Affected Resources is not 0 for a configuration risk, there are Kubernetes resources having risks. Click a risk name. On the risk details page, view the suggestion and the information about affected resources, such as the resource names, namespaces, hit rules, and paths. You can rectify the configuration risks based on the information.
- Security and compliance
The security and compliance list shows all the issues of this type that can be detected by HSS.Figure 13 Security and compliance
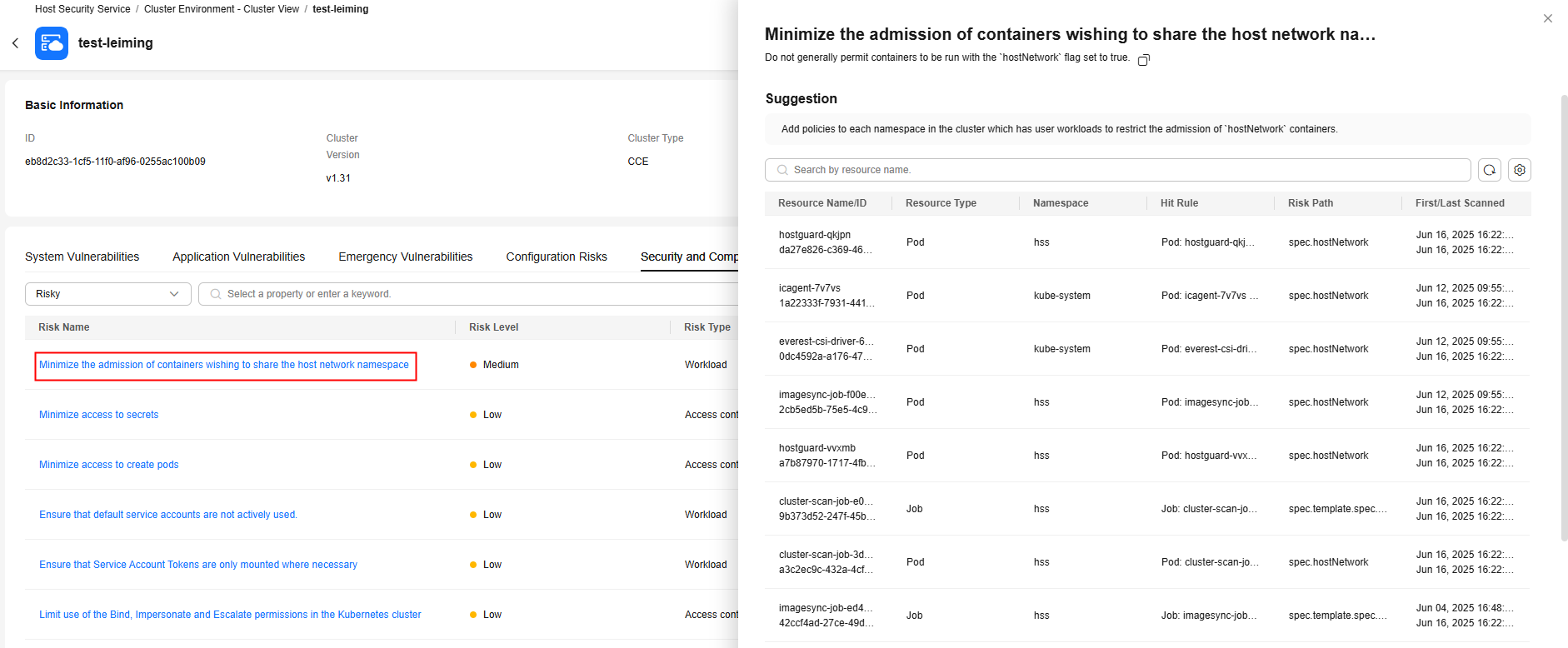
If the value of Affected Resources is not 0 for a security and compliance issue, there are Kubernetes resources having risks. Click a risk name. On the risk details page, view the suggestion and the information about affected resources, such as the resource names, namespaces, hit rules, and paths. You can rectify the security and compliance issue based on the information.
- System vulnerabilities
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





