Checking Cluster Environment Security
Scenarios
If a node in a cluster is protected by the container edition, you can check the cluster environment for IaC risks, vulnerabilities, configuration risks, sensitive information, and permissions management issues.
Checking Cluster Environment Security
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Cluster Environment.
- In the upper right corner of the page, click Scan.
- Select risk types and configure the scan task as needed.
- Scans for system vulnerabilities, application vulnerabilities, configuration risks, and compliance issues:
- Click the Cluster Scan tab.
- Configure scan task parameters.
For more information, see Table 1.
Table 1 Parameters of the scans for system vulnerabilities, application vulnerabilities, configuration risks, and compliance issues Parameter
Description
Example Value
Object Type
Select Cluster.
Cluster
Risk Type
Select Cluster vulnerability, Configuration risk, and Security and Compliance as needed. Cluster vulnerabilities include system and application vulnerabilities. For details about the risk items, see Cluster Environment Security Overview.
Select All
Cluster Scope
Select the cluster scope to be scanned.
- All Clusters
All the clusters where at least one node is protected by the container edition.
- Specific
Select clusters as needed.
All Clusters
- All Clusters
- Select I understand that starting a cluster scan will authorize HSS to create the following resources on the Kubernetes cluster: Job, ConfigMap, ServiceAccount, ClusterRole, and ClusterRoleBinding. For details about the usage of the created resources, see Resource Creation Description.
- Click Scan.
- In the upper right corner of the Cluster Environment page, click Manage Task. On the displayed page, choose Cluster Scan > Cluster to view the scan task progress.
After the scan task is complete, click View Details in the Operation column of a scan task to view the scan result of each cluster. If the scan fails, select the cluster and click Scan Again.
- Scan for emergency vulnerabilities
- Click the Cluster Scan tab.
- Configure scan task parameters.
For more information, see Table 2.
- Click Scan.
- In the upper right corner of the Cluster Environment page, click Manage Task. On the displayed page, click Cluster Scan > Cluster to view the scan task progress.
After the scan task is complete, click View Details in the Operation column of a scan task to view the scan result of each node. If the scan fails, select the node and click Scan Again.
- IaC risk scan
- Click the IaC Scan tab.
- Configure scan task parameters.
For more information, see Table 3.
Figure 1 IaC scan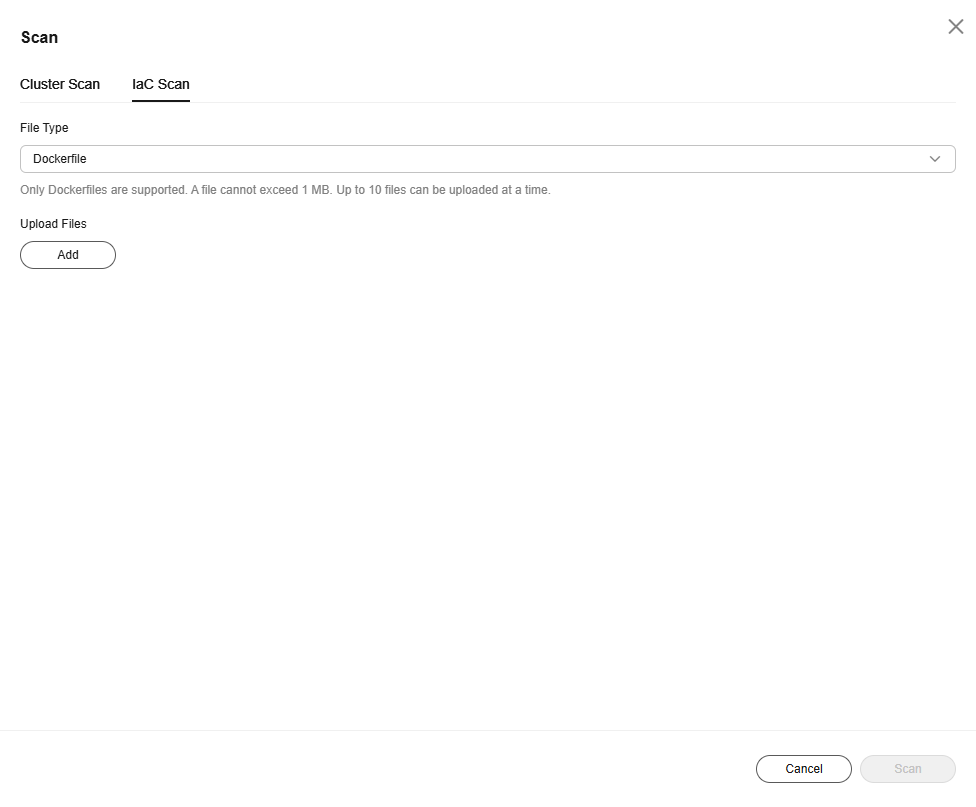
Table 3 IaC scan parameters Parameter
Description
File Type
Select a file type from the drop-down list. The options are as follows:
- Dockerfiles: image configuration file
- Kubernetes YAML: cluster resource configuration file
Upload Files
Click Add and upload the files to be scanned. The requirements are as follows:
- A file cannot exceed 1 MB. Up to 10 files can be uploaded at a time.
- If a file is being scanned, wait until the scan is complete and then upload files.
- Click Scan.
- In the upper right corner of the Cluster Environment page, click Manage Task. On the displayed page, click IaC Scan to view the scan task progress.
After the scan task is complete, click View Details in the Operation column of a scan task to view the scan result of each file. If the scan fails, select the file and click Scan Again.
- Scans for system vulnerabilities, application vulnerabilities, configuration risks, and compliance issues:
Resource Creation Description
If you scan for system vulnerabilities, application vulnerabilities, configuration risks, or security and compliance issues, HSS will create resources in the cluster and use them for the scan, as described in Table 4. These resources will be automatically deleted after the scan task is complete.
- CCE clusters: When creating a scan task, you need to grant HSS the permission to create the resources described in Table 4.
- Other clusters: When you connect these clusters to HSS, you already grant HSS the permission to create the resources described in Table 4. When creating a scan task, you need to confirm that you acknowledge and accept the resources created by HSS. For details about the cluster resource permissions of HSS, see Viewing the Cluster Node List and Permission List.
|
Resource Type |
Resource Name |
Namespace |
Description |
|---|---|---|---|
|
Job |
cluster-scan-job-{id} |
hss |
Risk scan task. The ID in the name is the unique ID of a scan task. |
|
ConfigMap |
cluster-scan-configmap-{id} |
hss |
Scan task configuration. The ID in the name is the unique ID of a scan task. |
|
ServiceAccount |
hss-read-only-sa |
hss |
Account bound to a job to grant the job the read-only permission to query Kubernetes resources. |
|
ClusterRoleBinding |
hss-view-cluster-role-binding |
- |
Used to bind the permission of the internal cluster role view to hss-read-only-sa. |
|
ClusterRole |
hss-read-only-cluster-role |
- |
Used to create a role with the read-only permission for the following resource types to perform RBAC permission checks: roles, rolebindings, clusterroles, clusterrolebindings, validatingwebhookconfigurations, mutatingwebhookconfigurations, networkpolicies, podtemplates, secrets, nodes, leases, and csistoragecapacities |
|
ClusterRoleBinding |
hss-read-only-binding |
- |
Used to bind the permissions of the hss-read-only-cluster-role role to hss-read-only-sa. |
Follow-up Operations
After a scan task is complete, check and mitigate environment security risks. For details, see Viewing and Handling Security Risks in a Cluster.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





