Configuring Protected Branch Rules
Protected Branch Rules Overview
CodeArts Repo makes a code branch more secure by preventing anyone other than the administrator from committing code, preventing anyone from forcibly committing code, or from deleting the branch. You can set this branch to be protected.
Constraints
Project manager or project administrator can configure project-level protected branch rules. For details, see Configuring Project-Level Permissions.
Configuring Protected Branch Rules
The process is as follows:
If you want all repository groups and repositories in this project to use the preceding settings, select Force Inherit.
- On the CodeArts Repo homepage, access the Scrum_Test project. In the top navigation bar, choose Settings > Policy Settings > Protected Branch and click Create Protected Branch.
Figure 1 Project-level protected branch page
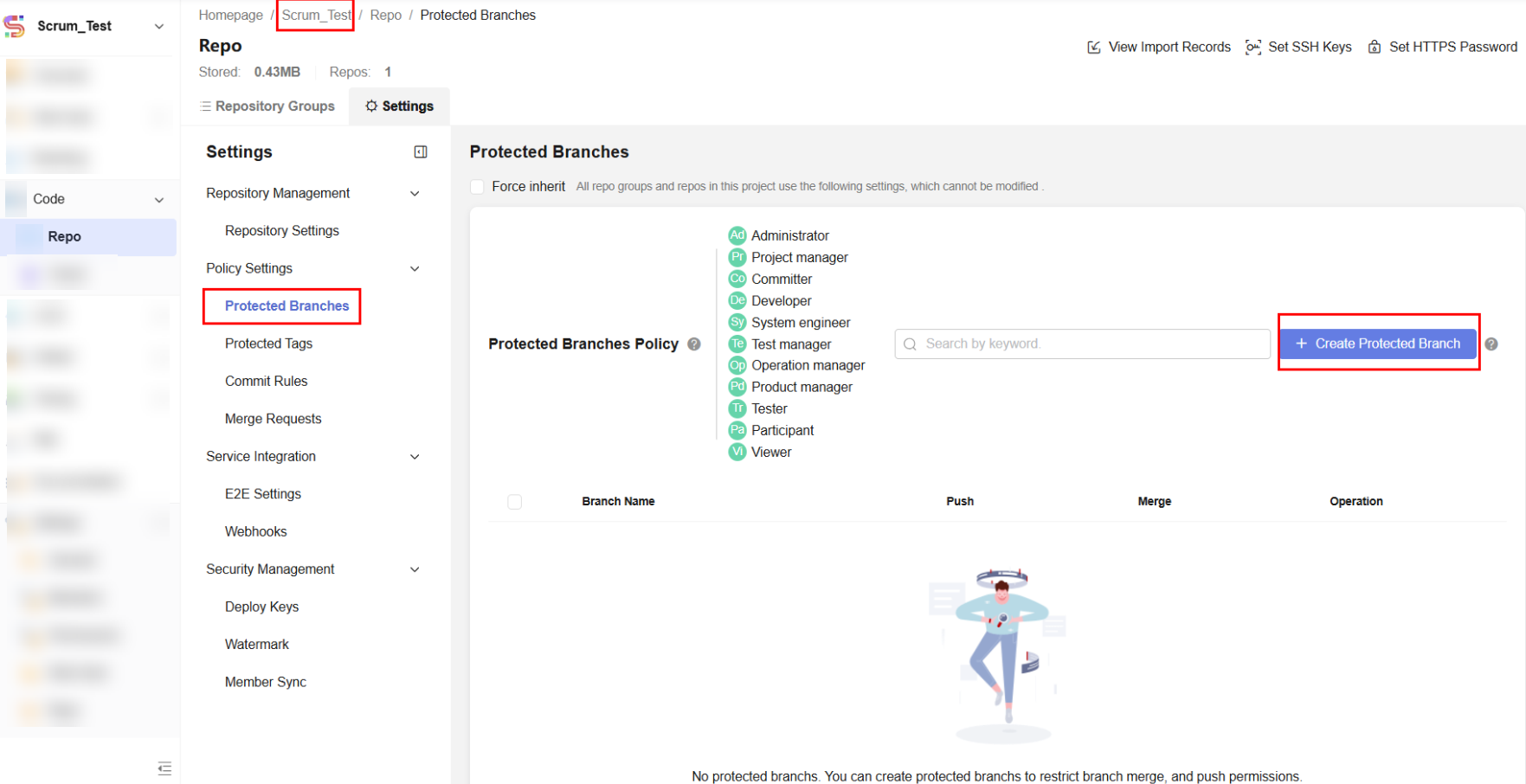
- Set the master branch as a protected branch so that no one can push code to the protected branch. Only committers can merge code to the protected branch. See the following figure.
If a branch contains a single slash (/), the branch cannot be matched using the wildcard * due to the fnmatch syntax rule.
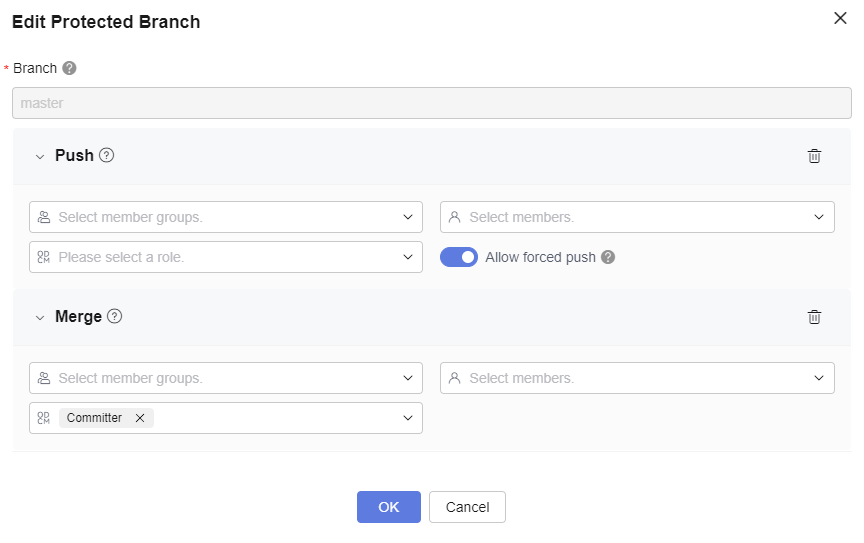

After Allow forced push is enabled, users who have the branch push permission can use the force push command to overwrite the protected branch, but cannot delete the branch. If you have selected Prevent git push-f command in Commit Rules, this function will be invalid.
Helpful Links
When you commit a code file, if an error message indicating you have no permission to commit to the target protected branch (DEV-23-8040) is displayed, the branch you are committing is a protected branch and you need to contact an administrator to grant you the commit permission.
Video Tutorial
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





