Configuring Commit Rules
Introduction
CodeArts Repo supports verification and restriction rules for high-quality code commits. This section describes how to configure project-level commit rules and use common regular expressions.
Before configuring commit rules, check Constraints.
If you have the configuration permission, you can set the same commit rules for all repositories in a project based on Table 1. When configuring rules, you can refer to Examples of Common Regular Expression.
Constraints
When your role is Project Manager or Project Administrator, you can set project-level commit rules. If you do not have the permission, see Configuring Project-Level Repo Permissions.
Configuring Project-Level Commit Rules
On the CodeArts Repo homepage, go to a project, and choose Settings > Policy Settings > Commit Rules on the top navigation bar.
If you want to set the same commit rules for all repositories in a project, set parameters based on Table 1 and select Force inherit.
|
Parameter |
Description |
Example Value |
|---|---|---|
|
Reject non-signed-off-by commits |
This function records the developer responsible for code modifications, confirming their verification and accountability for the submitted content. This is a transparent way to track contributors and safeguard the quality of contributions. If this option is selected, only signed-off-by commits can be pushed to the repository. Currently, the following two modes are supported:
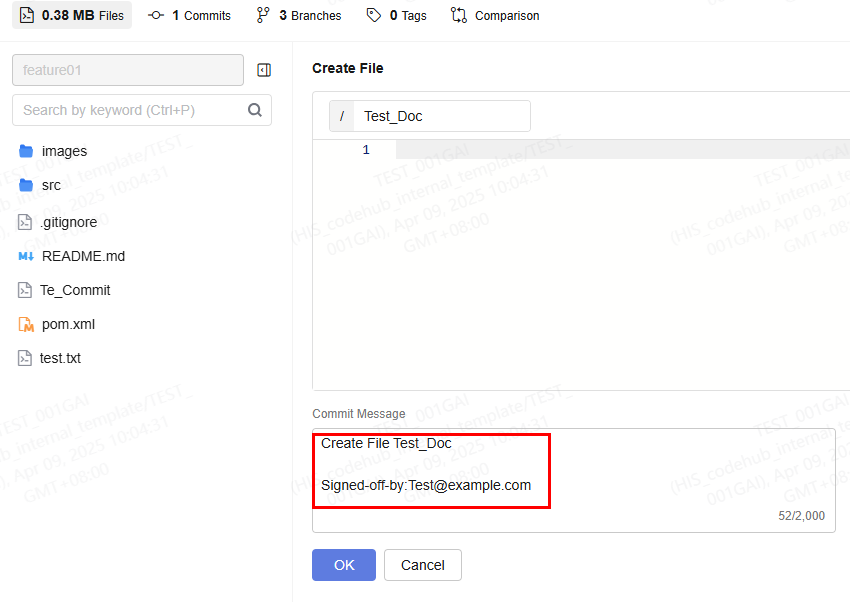
When performing online commit in the CodeArts Repo, use the following format to compile and commit information: commit message # Enter the customized commit information.
# This is a blank line.
Signed-off-by: User-defined signature # Enter the user-defined signature after Signed-off-by:
When committing code on the Git client, run the following command. -s indicates that the signature (Signed-off-by) is added to the commit message. You need to configure the signature and email address on the client in advance by referring to Helpful Links. git commit -s -m "<your_commit_message>" |
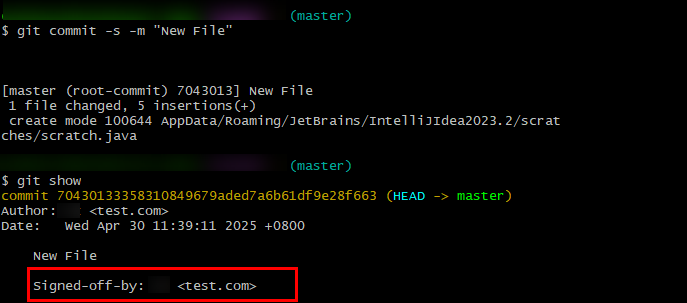
Refer to the following example if this option is selected:
git commit -s -m "New File" You can run the git show command to check the signature result.
|
|
Reject commits not signed by GPG |
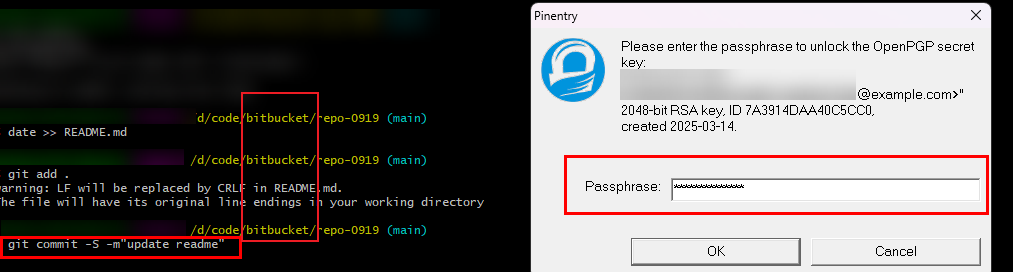
If this option is selected, only commits signed by GPG can be pushed to the repository. For details, see Configuring a GPG Public Key. Git client signature mode: When committing code on the Git client, you need to add the -S parameter, indicating that the GPG (GNU Privacy Guard) signature is used to verify the identity of the committer. git commit -s -m "your commit message" When using tags on the Git client, you need to add the -s parameter, indicating that the GPG signature is used to verify the authenticity of the tag. git tag -s -m "your tag message" |
After this option is selected, run the following command and the commit message is update readme. git commit -S -m "update readme" After the command is executed successfully, you'll be instructed to enter the password of the GPG key, as shown in the following figure.
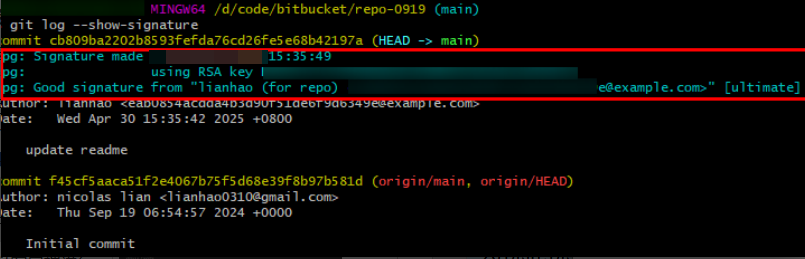
As shown in the following figure, you can run the following command to view the GPG signature submission records.
|
|
Tags cannot be deleted |
After this option is selected, tags cannot be deleted online or by running commands on the client. |
After this option is selected, an error message indicating tags cannot be deleted is displayed when you delete any tag. |
|
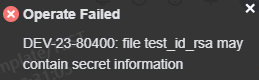
Prevent committing secrets |
The confidential file names include id_rsa and id_dsa. After this option is selected, an error is reported if the name of a new file submitted online or locally contains rsa, id_rsa, dsa, or id_dsa. |
After this option is selected, if the name of a new file is test_id_rsa, an error message indicating the file may contain sensitive information is displayed.
|
|
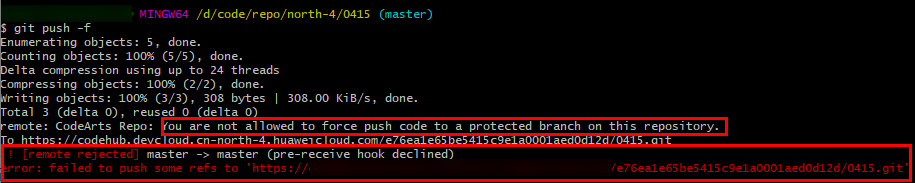
Prevent git push -f |
Configure whether to use the git push -f command on the client to commit code. It is recommended to enable this considering the git push -f command is used to push your local code repository to CodeArts Repo. |
After this option is enabled, the following error message is displayed when you run the git push -f command locally: "CodeArts Repo: You are not allowed to force push code to a protected branch on this repository."
|
If you want to set commit rules for a specified branch of a repository in a project, click Create Commit Rule. For details about the parameters, see Table 2.
|
Parameter |
Description |
Example Value |
|---|---|---|
|
Rule Name |
Customize a rule name. |
Test_Rule |
|
Branch |
Enter a complete rule name or create a regular expression. The input needs to be verified, including the branch name and regular expression. |
Branch_* indicates that all branch names must start with Branch_. |
|
Commit Rule |
Optional.
|
For more regular expression rules, see Examples of Common Regular Expression. |
|
Basic Attributes |
Optional.
|
|
|
Binary Rules |
Optional. To ensure repository performance, you are advised to select Do not allow new binary files (privileged users excepted). This is not selected by default. Do not allow new binary files (privileged users excepted) is selected by default. After Allow changes to binary files (privileged users excepted) is selected, binary files in the modify state will not be intercepted and can be directly uploaded. Binary files can be deleted without binary check.
|
Example: Select Do not allow new binary files (privileged users excepted). |
|
Effective Date |
Optional. Before being committed, all commits created after the effective date must match the hook settings. If this parameter is left empty, all commits are checked regardless of the commit date. |
Example: April 15, 2025 |
Examples of Common Regular Expression
Common regular expression examples are listed below.
|
Rule |
Example |
|---|---|
|
Single a, b, or c |
[abc] |
|
Characters other than a, b, or c |
[^abc] |
|
Lowercase letters ranging from a to z |
[a-z] |
|
Characters outside the range of a to z |
[^a-z] |
|
Uppercase and lowercase letters in the range of a to z or A to Z |
[a-zA-Z] |
|
Any single character |
. |
|
Match a or b. |
a|b |
|
Any blank character |
\s |
|
Non-blank characters |
\S |
|
Arabic numeral characters |
\d |
|
Non-Arabic numeral characters |
\D |
|
Letters, digits, or underscores (_) |
\w |
|
Characters other than letters, digits, or underscores (_) |
\W |
|
Match the content in parentheses (not capture) |
(?:...) |
|
Match and capture the content in parentheses |
(...) |
|
No or one a |
a? |
|
No or more a's |
a* |
|
One or more a's |
a+ |
|
Three a's |
a{3} |
|
More than three a's |
a{3,} |
|
3 to 6 a's |
a{3,6} |
|
Beginning of text |
^ |
|
End of text |
$ |
|
Word boundary |
\b |
|
Non-word boundary |
\B |
|
Line breaker |
\n |
|
Carriage return character |
\r |
|
Tab key |
\t |
|
Null string |
\0 |
Managing Commit Rules
Click  in the row where the target commit rule is located to view details, as shown in the following figure. Click
in the row where the target commit rule is located to view details, as shown in the following figure. Click  to modify the rule and save it again. Click
to modify the rule and save it again. Click  to delete the commit rule.
to delete the commit rule.
git config --global user.name your name
- Run the following command to set a global email address in Git:
git config --global user.email your email address
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot