Secure Operations Framework
With years of experience in security operations and continuous support for customers, Huawei Cloud SecMaster offers the following security operation frameworks and processes to help you get started.
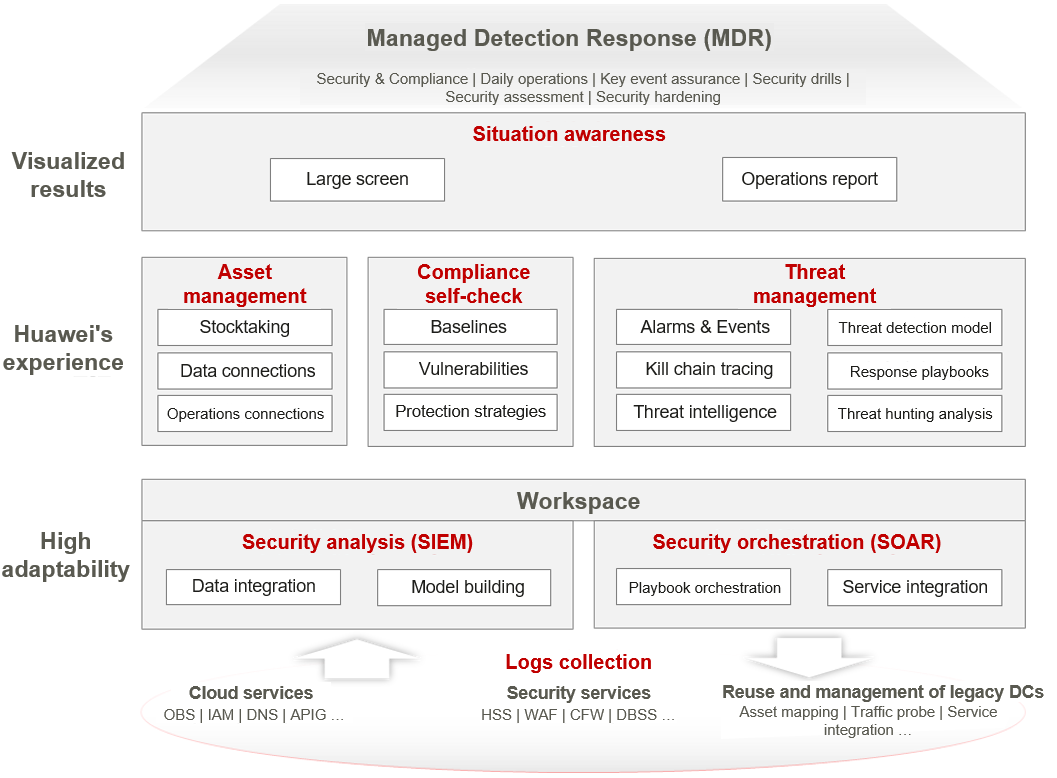
- Define security operation responsibilities
First, you need to clarify the responsibilities of application teams and the Cloud Center of Excellence (CCoE) team. This is subject to each enterprise's cloud operations mode. For example, in the enablement and collaborative operation mode, the CCoE team is responsible for security protection and centralized security operations at the platform layer, and application teams are responsible for security operations of application systems and required cloud resources. Then, SecMaster allocates workspaces for the CCoE team and each application team, ensuring clear division of responsibilities and providing a unified security operations management view for the CCoE team. Finally, you need to connect the security data and assets of the service system running environment to the unified security operations platform. SecMaster can manage the running environments of Huawei Cloud and IDCs, as well as environments across regions and accounts.
- Identify and clear asset risks
SecMaster automatically inventories assets on Huawei Cloud, including hosts, IP addresses, websites, and databases, and connects on-premises asset information via third-party software.
You can enable HSS to scan for vulnerabilities in Linux, Windows, and web applications, integrating results to SecMaster for lifecycle management. OS vulnerabilities can be patched with a few clicks.
Additionally, SecMaster identifies compliance risks, aligning with over 10 standards like DJCP, PCI-DSS, and ISO27001. It also provides best practices, hardening suggestions, and reports. You can use SecMaster to comprehensively check the protection coverage of assets and centrally manage security policies at each defense line.
- Perform data integration and security analysis
First, integrate security data and cloud service logs to SecMaster. Build a unified on- and off-cloud data integration solution to access logs of third-party ecosystem software.
Then, build a security threat detection model based on security data. This model identifies kill chains, analyzes behaviors of each line of defense, and implements in-depth monitoring. It uses big data technologies and intelligent analysis algorithms to accurately detect abnormal behaviors and show them in pop-up messages. The model uses User and Entity Behavior Analytics (UEBA) to restore kill chains and automatically update user profiles, asset fingerprints, and intelligence profiles.
Then, after you connect your platform with threat intelligence, the data, logs, and alarms in daily operations are displayed. The information on the Huawei Cloud platform is shared with you to help you perform security operations.
- Handle security incidents
With SecMaster, you can respond to, investigate, and handle alarms and events. It provides entities, assets, intelligence, and historical information to help you check and trace kill chains, along with handling suggestions. Playbooks and processes can be orchestrated to quickly address and manage security threats.
These approaches should be carried out in a long term to continuously discover and handle new security threats, thereby enhancing system security and improving the capabilities of the security operations team.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





