Security Reference Framework
Huawei Cloud suggests using its "1 center + 7 layers of defense" security reference framework and cloud-native security services to create a robust cloud protection system, as shown below. The security reference framework follows the defense-in-depth principle and combines various security measures. It tailors specific protection for critical systems and essential enterprise data according to their needs. This creates several layers of defense that work together, make it harder for attackers to break them. These layers also provide enough time for detecting and responding to threats.
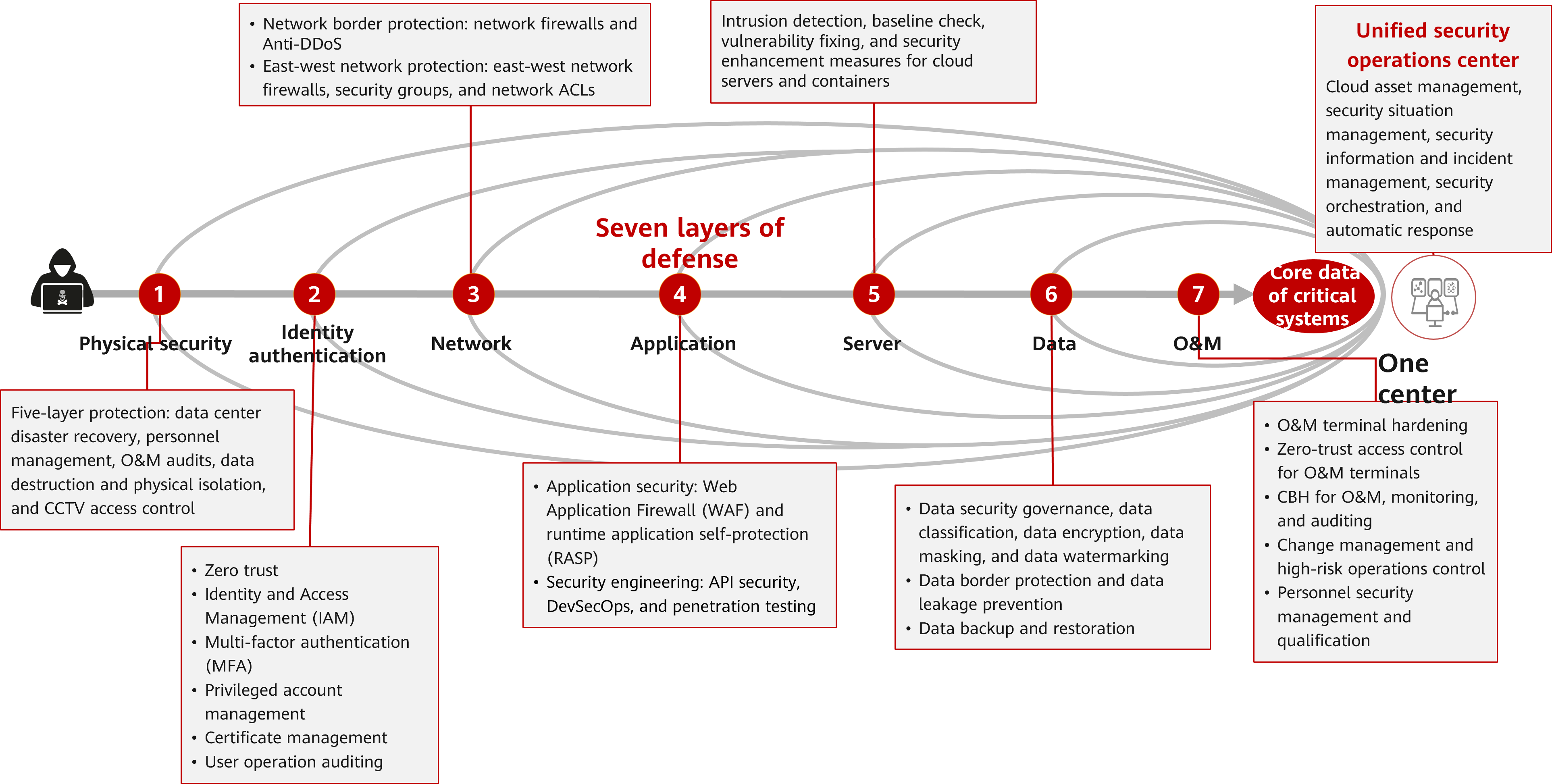
- Physical security
Huawei Cloud data centers are protected by five layers of physical security, including data center disaster recovery, personnel management, O&M audits, data destruction and physical isolation, CCTV, and access control. Tenants do not need to pay attention to the physical security of data centers. However, enterprises need to maintain the physical security of their data centers where the dedicated cloud is deployed.
- Identity authentication
Huawei Cloud verifies identities based on the principle of zero trust, and assigns permissions based on the principle of least privilege (PoLP). By default, multi-factor authentication is enabled to prevent unauthorized access. Privileged accounts are properly managed, and any user operations on the cloud platform are recorded and audited.
For details, see IAM best practices.
- Network
The core is to protect network borders and control east-west access on the intranet.
- Network border protection: The network border refers to the border where one network connects to another, typically where Internet access, VPN, and private line access are involved. Cloud Firewall (CFW), VPC security groups, and network ACLs provided by Huawei Cloud control traffic flowing through the network border. CFW detects and prevents network intrusions. Whitelists can be used to allow only limited access and traffic over high-risk ports and protocols are not allowed.
- East-west network protection: You can manage services by confidentiality level, for example, deploying services of different confidentiality levels in different VPCs. You can use VPCs to isolate large network security zones, use CFW to control access between east-west VPC networks, and use VPC security groups to protect instances and network ACLs to protect subnets.
- Application
WAF should be deployed to protect application servers that provide Internet-accessible services. To design application security layer, you need to pay attention to software security engineering and improve the built-in security capability of applications. From the perspective of security risks, you should pay more attention to applications connected to external networks. In addition, you need to identify internal core applications and strengthen their security.
- Server
Server-level intrusion detection works better. Install server security products on servers to handle vulnerabilities and configure security settings.
- Data
You can identify and categorize data assets early, manage data security across its entire lifecycle, anonymize, encrypt, and audit critical data usage, and regularly back up essential data. And also, you can build a solid data security border, by applying identity authentication, network access control, and resource control, to prevent sensitive data leaks.
- O&M
Initiate O&M activities only from secure networks. Establish dedicated access channels for O&M activities. For example, let O&M personnel use dedicated O&M services and bastion hosts for O&M to minimize black screen O&M operations and ensure that O&M activities can be audited and traced.
- One center
Security depends less (30%) on technology and more (70%) on operations. Only when security products at each defense layer are correctly configured and well maintained can security be effectively implemented. To achieve this, a unified security operations platform that integrates various security products is needed.
Establishing an in-depth defense system may be time-consuming. You need to balance security, efficiency, cost, and experience throughout the process. You should regularly assess security risks, strengthen defenses against top threats, continuously enhance protective measures, and test system effectiveness through activities like team/blue team drills.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





