Limiting Traffic of a Specified Protocol
After protocol blocking is enabled, the system limits the rate of traffic destined for Anti-DDoS Service objects based on the protocol type. This feature supports protocols such as UDP, TCP, and ICMP.
For details about the rate limit thresholds for different protocols, see Table 1.
|
Protocol Type |
Rate Limit (pps) |
|---|---|
|
UDP |
10 Mbit/s |
|
TCP |
10 Mbit/s |
|
ICMP |
100pps |
|
Other (other protocols) |
10 Mbit/s |
Enabling Protocol Blocking
- Log in to the AAD console.
- In the navigation pane on the left, choose . The Protection Policies page is displayed.
- Click Create Protection Policy.
- In the displayed dialog box, set the policy name, select an instance, and click OK.
Figure 1 Creating a policy

- In the row containing the target policy, click Set Protection Policy in the Operation column.
- In the Protocol-based Traffic Control configuration box, click Set, as shown in Figure 2.
- In the Protocol Rate Limiting Settings dialog box, configure the protocol policy and click OK.
Figure 3 Setting protocol blocking
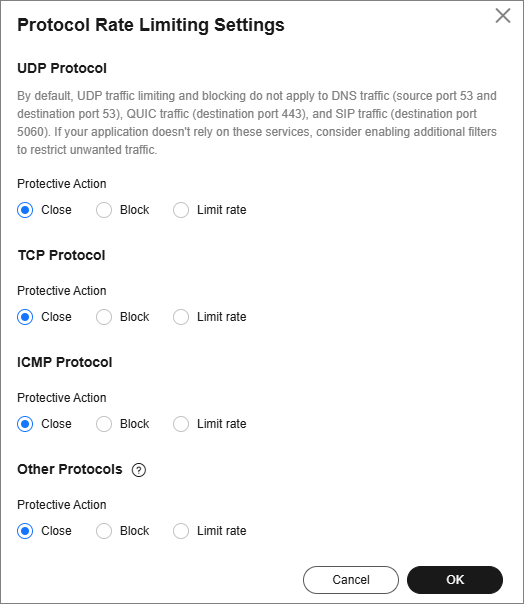
Table 2 Parameter description Protective Action
Description
Close
After the Protective Action is set to Close, the rate limit saved in the database is used for protection.
Block
After the Protective Action is set to Block, the default rate limit is used for traffic control.
Limit rate
After the Protective Action is set to Limit rate, traffic is limited based on the user-defined policy.
- Rate Limiting (Kbit/s): Traffic is limited based on the user-defined rate limit.
- Fragment Rate Limiting (Kbit/s): Traffic is limited based on the user-defined fragment rate limit.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot