Overview
QingTian confidential computing aims to use dedicated hardware and related firmware as the root of trust to protect customer application code and data being processed from external access.
- Confidentiality protection: Ensures that customer data and code are not accessed by CSPs' internal personnel, cloud systems, and customers' internal personnel or VM administrators.
- Integrity protection: Ensures that customer data and code are not tampered with by CSPs' internal personnel, cloud systems, and customers' internal personnel or VM administrators.
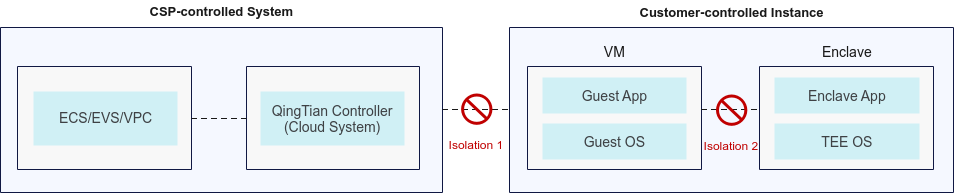
To achieve these objectives, QingTian confidential computing provides security isolation in two dimensions:
- Isolation dimension 1: Isolate customer data and code from CSPs' internal personnel and cloud system software.
- Isolation dimension 2: Isolate customer data and code from customers' internal personnel and untrusted guest OSs.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





