Performing Operations on Managed Services
Prerequisites
Tenants have entrusted MSPs to manage the Border Protection and Response Service. For details, see "MSP-based Management" in the Common Tenant Operations.
Context
The management operations by an MSP vary according to managed services. This section only describes the management operations by an MSP on the Border Protection and Response Service. For details about other common basic operations, such as personalized settings, rights- and domain-based management, tenant creation, service ticket creation, and log viewing, see Basic MSP Operations.
The Border Protection and Response Service supports service management by Tenants or Services. Unless otherwise specified, the following part introduces service management by Tenants.
Searching for and Following Tenants
- Log in to the Huawei Qiankun console using an MSP account and click Tenants in the menu bar.
- Perform related operations in the tenant list on the left.
- Search for a tenant.
Enter a tenant name in the search box and click the
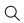 icon on the left or press Enter.
icon on the left or press Enter. - Check tenant information
Click the target tenant. The corresponding user information, such as the name, mobile number, and email address, is displayed on the right of the tenant list.
- Follow
Click Follow next to tenant names in the list and asterisks (*) are displayed. If you do not need to follow the tenant names, click Unfollow.
- Add labels
Click Add Label. The label details are displayed below the tenant name in the list. To delete a label, click x next to the label.
- Filtering tenants
Click
 in the upper right corner of the tenant list to filter tenants by label.
in the upper right corner of the tenant list to filter tenants by label.
- Search for a tenant.
Entering and Exiting MSP-based Management
- Log in to the Huawei Qiankun console using an MSP account and click Tenants in the menu bar.
- Select a tenant to be managed in the tenant list on the left.
- Enter and exit MSP-based management.
- Enter the management
Click Enter Management View. The MSP directly accesses the tenant page on behalf of a managed tenant. The management operations by an MSP are the same as the operations by a tenant.
- Exit the management
After the service management by an MSP is completed, click Exit Management View on the console home page. The MSP account page is displayed.
Figure 1 Exiting the management
- Enter the management
Handling Threat Events
This section introduces MSP management by service.
- Log in to the Huawei Qiankun console using an MSP account and click Services in the menu bar.
- (Optional) Filter tenants by tenant name or label in the Tenant List area.
- Click View Details on the right of the service card or tenant list.
- Click Threat Events in the menu bar to handle threat events.
For details, see Handling Threat Events.
Delivering IP Blacklists and Whitelists
This section introduces MSP management by service.
- Log in to the Huawei Qiankun console using an MSP account and choose in the menu bar.
- (Optional) Filter tenants by tenant name or label in the Tenant List area.
- Click View Details on the right of the service card or tenant list.
- Click Blacklist and Whitelist in the menu bar.
- The following describes how to deliver IP address blacklists in batches.
Choose , click Create, set parameters, and deliver the IP address blacklists to devices of tenants in batches.
A maximum of 50 IP addresses separated by carriage return characters can be added at a time.
If the delivery is successful, the number of IP address blacklists that are successfully delivered is displayed. If the delivery fails, the detailed information about the IP address blacklists that fail to be delivered is displayed.
Figure 2 Delivering IP address blacklists in batches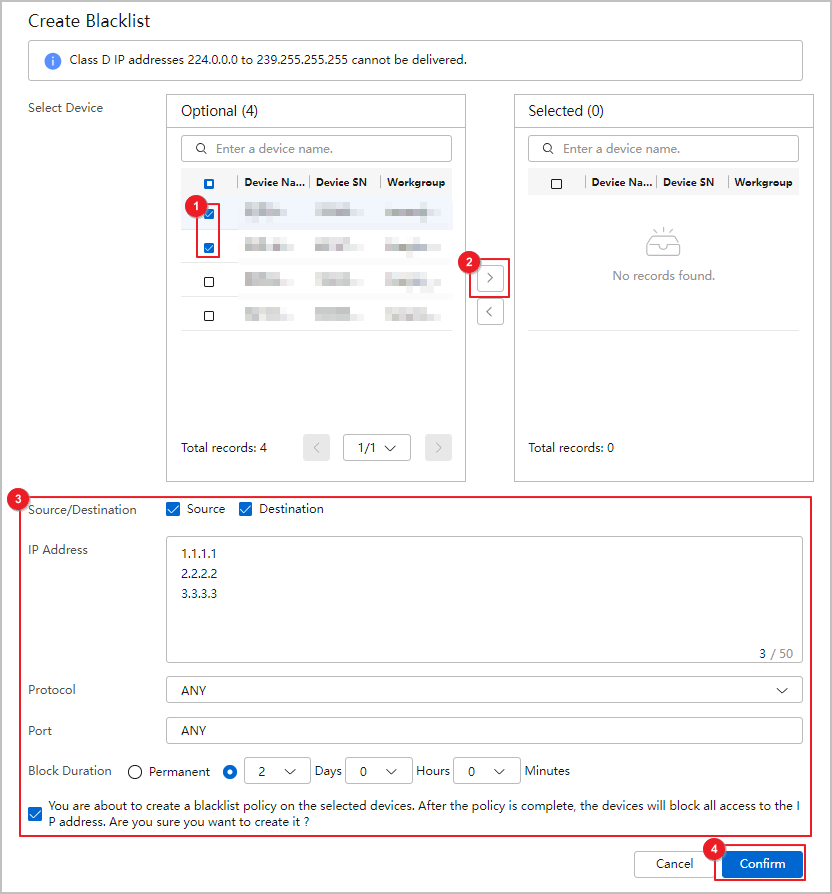
Delivering Domain Name Blacklists
This section introduces MSP management by service.
- Log in to the Huawei Qiankun console using an MSP account and choose in the menu bar.
- (Optional) Filter tenants by tenant name or label in the Tenant List area.
- Click View Details on the right of the service card or tenant list.
- Click Blacklist and Whitelist in the menu bar.
- Choose , click Create, set parameters, and deliver the domain name blacklists to devices of tenants in batches.
A maximum of 50 domain names separated by carriage return characters can be added at a time. Domain names support regular expression matching. For details about the rules, move the mouse cursor over the
 icon.
icon.If the delivery is successful, the number of domain name blacklists that are successfully delivered is displayed. If the delivery fails, the detailed information about the domain name blacklists that fail to be delivered is displayed.
Figure 3 Delivering domain name blacklists in batches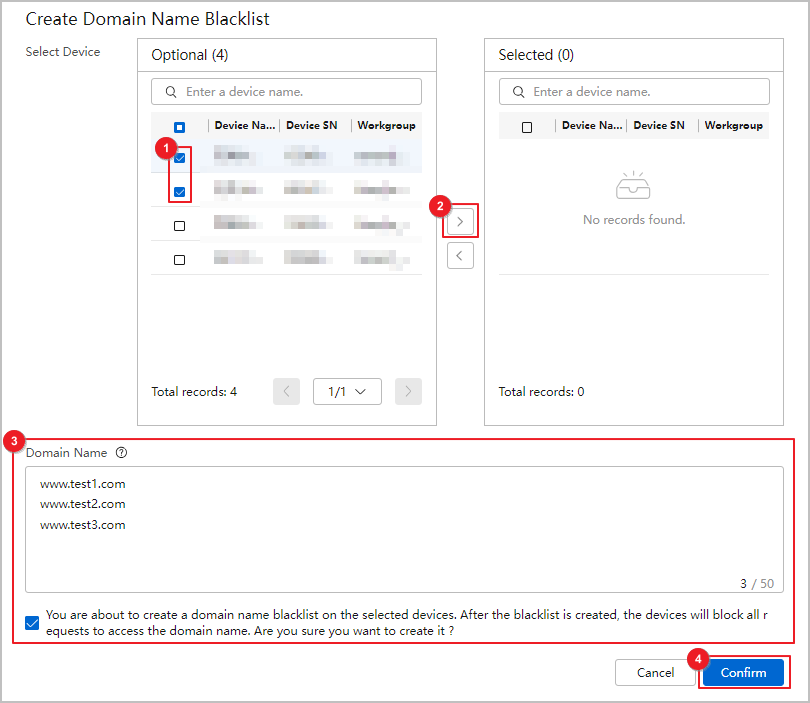
Checking Security Reports
- Log in to the Huawei Qiankun console using an MSP account and click Tenants in the menu bar.
- Select a tenant to be managed in the tenant list on the left.
- Click Enter Management View. Then choose .
- Click Security Reports in the menu bar to check the security reports.
For details, see Checking Security Reports.
Creating a Custom Report
MSPs can specify a period to generate custom reports and push the reports to managed tenants. The MSP can use this function only during service management by Services.
- Log in to the Huawei Qiankun console using an MSP account and choose in the menu bar.
- (Optional) Filter tenants by tenant name or label in the Tenant List area.
- Click View Details on the right of the service card or tenant list.
- Choose Security Reports, click the Custom Report tab, and click Create.
- Set related parameters. Confirm and push the reports.
Figure 4 Customizing reports
Checking the Security Protection Dashboard
The MSP security protection dashboard displays data related to security events of all managed tenants.
- Log in to the Huawei Qiankun console using an MSP account and click Dashboard in the menu bar.
- Optional: Click
 in the upper left corner of the page, filter tenants by label, and customize related data to be displayed.
in the upper left corner of the page, filter tenants by label, and customize related data to be displayed. - Check the MSP security protection dashboard.
Figure 5 MSP security protection dashboard
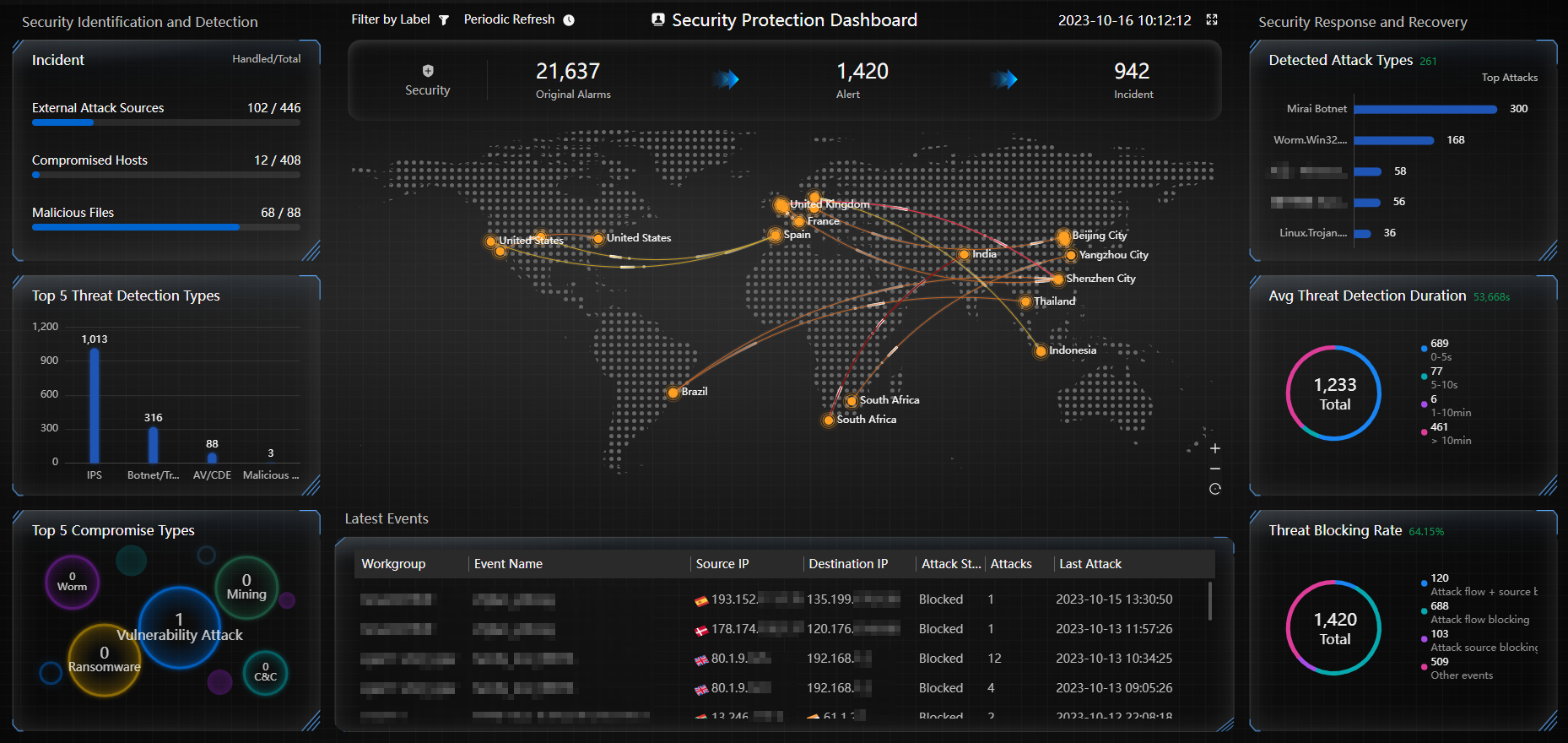
Table 1 Description of modules on the MSP security protection dashboard Module
Description
Incident
Displays the numbers of handled and total external attack sources, compromised hosts, and malicious files.
Top 5 Threat Detection Types
Displays top 5 threat event types by quantity.
Top 5 Compromise Types
Displays top 5 causes leading to compromised hosts by quantity.
Security Events
Displays the number of security events of each type.
- Original Alarms: Huawei Qiankun identifies original events based on threat logs provided by Qiankun Shield devices.
- Alert: Huawei Qiankun aggregates original events into alarm events after automatic model-based analysis and manual handling by security operations experts.
- Incident: After further intelligent analysis, Huawei Qiankun classifies alarm events into three types: external attack sources, compromised hosts, and malicious files.
Attack Map
Dynamically displays the source-to-destination attack direction and region distribution of the latest threat events.
Latest Events
Displays threat event information in reverse chronological order.
Detected Attack Types
Displays top 5 detected attack types by quantity.
Avg Threat Detection Duration
Displays the average time taken by Huawei Qiankun to detect threat events based on the logs reported by Qiankun Shield devices.
Threat Blocking Rate
Displays information about threat event blocking.
- Attack flow + source blocking: displays the number of threat events detected and blocked by Qiankun Shield devices based on security protection policies and blacklisted by Huawei Qiankun.
- Attack flow blocking: displays the number of threat events detected and blocked by Qiankun Shield devices based on security protection policies.
- Attack source blocking: displays the number of threat events to which Huawei Qiankun has delivered blacklists.
- Other events: displays the number of threat events that have not been handled.
Exporting the compromised Host Report
The MSP can use this function only during service management by Services.
- Log in to the Huawei Qiankun console using an MSP account and choose in the menu bar.
- (Optional) Filter tenants by tenant name or label in the Tenant List area.
- Click View Details on the right of the service card or tenant list.
- Click Threat Events in the menu bar. Click View More in the upper right corner of the Compromised Hosts area.
- Click Export and export the analysis report as prompted.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






