Notice of Grafana Security Vulnerability (CVE-2025-4123)
Grafana is an open-source data visualization and monitoring tool. It is widely used by enterprises and organizations to collect, analyze, and display metrics and log data from different data sources.
Description
|
Type |
CVE-ID |
Severity |
Discovered |
|---|---|---|---|
|
Code execution |
High |
2025-05-21 |
Impact
A vulnerability was found in the processing of the custom frontend plugin of Grafana. This vulnerability allows attackers to execute cross-site scripting (XSS) attacks by exploiting client path traversal and open redirection issues. Such attacks may result in arbitrary JavaScript execution and could redirect users to malicious websites. If anonymous access is enabled, an attack can be carried out without any privilege escalation.
Identification Method
- Go to Add-ons and check whether the Grafana add-on has been installed and, if it has been, what version.
Figure 1 Viewing the installed add-on version
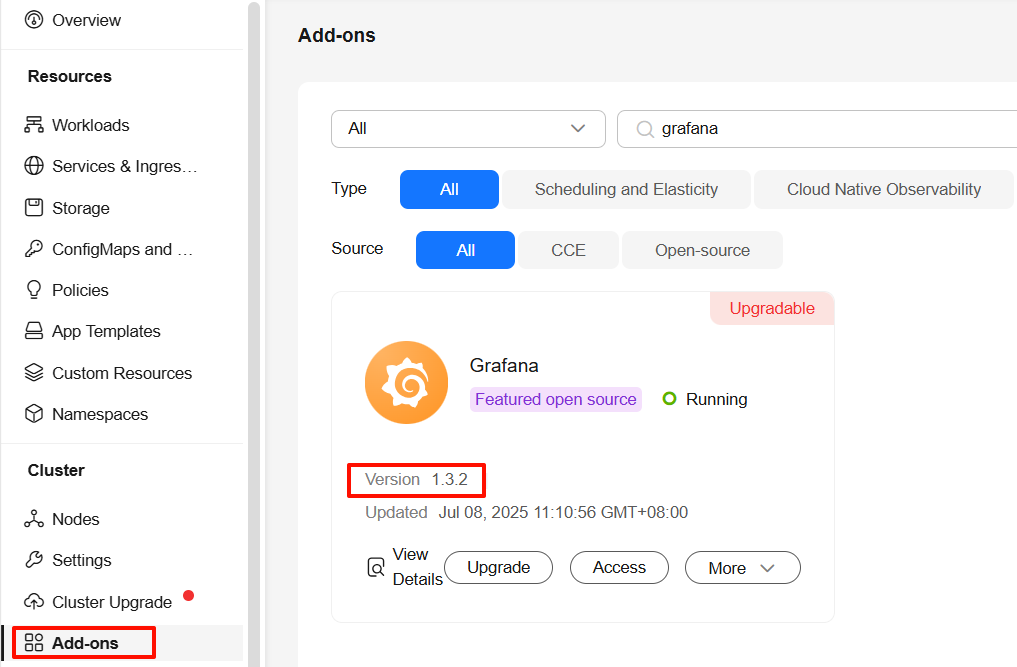
- If the add-on version is 1.3.2 or earlier, the vulnerability is present.
Solution
Do not expose Grafana to the Internet. CCE will release a new version of the Grafana add-on to fix this vulnerability. For details, see Grafana Release History.
Helpful Links
- Grafana security notice: https://grafana.com/security/security-advisories/cve-2025-4123/
- Grafana fixing description: https://grafana.com/blog/2025/05/23/grafana-security-release-medium-and-high-severity-security-fixes-for-cve-2025-4123-and-cve-2025-3580/
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





