Help Center/
Edge Security/
Best Practices/
Using Edge Security to Defend Against Resource Theft/
Automated or AI-powered Protection/
IP Intelligence Database
Updated on 2025-12-15 GMT+08:00
IP Intelligence Database
The IP intelligence database integrated with edge security can identify malicious request sources to improve protection efficiency.
Procedure
- Log in to the management console.
- Click
 in the upper left corner of the page and choose .
in the upper left corner of the page and choose . - In the navigation pane on the left, choose Edge Security > Policies.
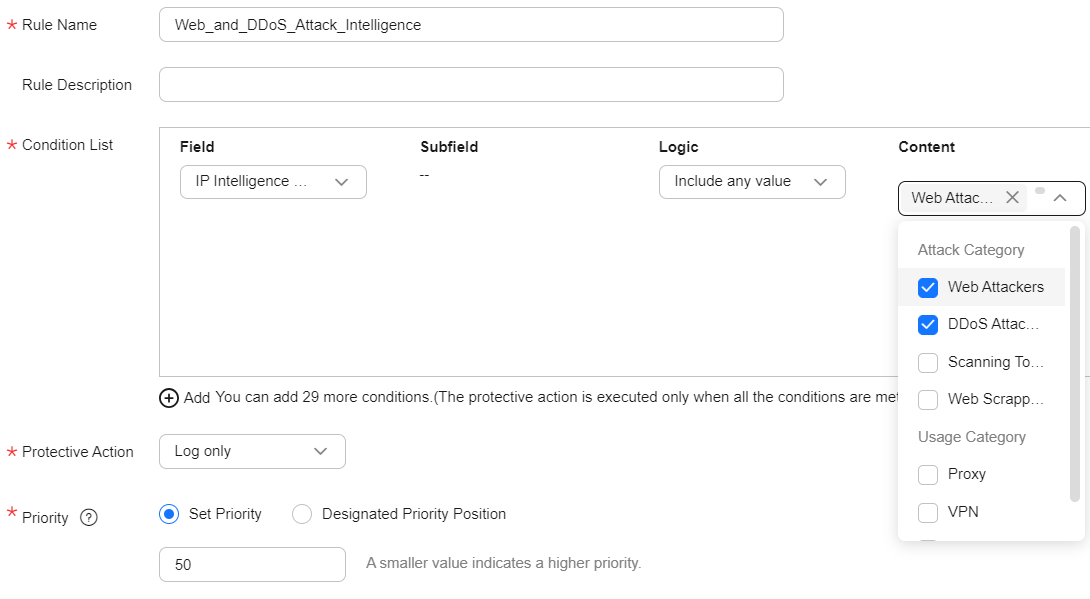
- Click the name of the policy to be modified and choose Precise Protection. Set field in Condition List to IP intelligence tag, set Logic to Include any value, and select attack IP intelligence as required, such as web attacker, DDoS attacker, scanning tool, and web crawler.
- You can configure protection actions as required based on the IP intelligence identification result. You are advised to set Log only. After the intelligence identification result is evaluated, malicious IP addresses are configured in the IP address blacklist or CC attack protection is configured.
Figure 1 Configuring rules
Parent topic: Automated or AI-powered Protection
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
The system is busy. Please try again later.
For any further questions, feel free to contact us through the chatbot.
Chatbot





