kubeconfig of an On-Premises Cluster
Obtaining the kubeconfig of an On-Premises Cluster
A kubeconfig file can be used to organize information about clusters, users, namespaces, and authentication mechanisms. The kubectl command-line tool uses the kubeconfig file to find the information it needs to choose a cluster and communicate with the API server of the cluster.
You need to use ucs-ctl to obtain the kubeconfig file of an on-premises cluster.
- Use ucs-ctl to obtain the name of the on-premises cluster.
./ucs-ctl get cluster

- Use ucs-ctl to export the kubeconfig file of the on-premises cluster.
./ucs-ctl get kubeconfig -c test-redhat86 -o kubeconfig
You can run the ucs-ctl get kubeconfig -h command to view the following parameters in a kubeconfig file:
- -c, --cluster string: specifies the name of the cluster whose kubeconfig file is to be exported.
- -e, --eip string: specifies the EIP of the API server.
- -o, --output string: specifies the name of the kubeconfig file.
- -p, --secretPath string: specifies the path that stores the encrypted material of the kubeconfig file to be exported.
Updating the Certificate File of an On-Premises Cluster
You can use ucs-ctl to update the certificate file of an on-premises cluster if the certificate information is disclosed or the certificate expires or when you perform routine security maintenance.
- You can select TLS or CA to update the certificate.
./ucs-ctl kcm update-cert {cluster_name} --mode tls
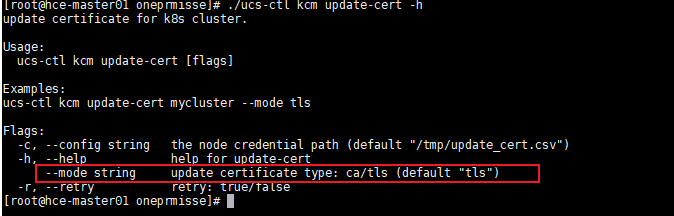
- If you need to update the certificate again, delete the file in the certificate directory and then update the certificate. If you do not delete the file first, "error: "update cert recordFile[\"var/paas/ucs/{cluster_name}/cert_update/status.json\"] already exists, please use the option \"-- retry or -r\"to retry it"." will be displayed.
rm -rf /var/paas/ucs/{cluster_name}/cert_update
Using the kubeconfig of an On-Premises Cluster
After obtaining the kubeconfig file generated by ucs-ctl, take the following steps to make this file take effect on the node:
- Copy the kubeconfig file to the node.
scp /local/path/to/kubeconfig user@remote:/remote/path/to/kubeconfig
- If environment variable EnableSecretEncrypt has been added, delete it first.
unset EnableSecretEncrypt
- Make the kubeconfig file take effect by using one of the following methods:
- Method 1: Copy the kubeconfig file to the default path.
mv /remote/path/to/kubeconfig $HOME/.kube/config
- Method 2: Specify KUBECONFIG as the environment variable.
export KUBECONFIG=/remote/path/to/kubeconfig
- Method 3: Specify kubeconfig in command lines.
kubectl --kubeconfig=/remote/path/to/kubeconfig
- Method 1: Copy the kubeconfig file to the default path.
After the preceding operations are performed, kubectl can communicate with the API server of the on-premises cluster. For details about how to use the kubeconfig file, see Organizing Cluster Access Using kubeconfig Files.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





