Validating a Custom Identity Policy
IAM Access Analyzer helps you check IAM custom identity policies, IAM trust policies, and Service control policies (SCPs) in Organizations against policy grammar. Policy validation check findings include security warnings, errors, general warnings, and suggestions. You can use the findings to create policies that are functional and secure. Access analyzer provides check findings when you create or edit custom identity policies and trust policies on the IAM console and SCPs on the Organizations console in the JSON format, or by calling APIs. The following example describes how to validate a custom identity policy with Access Analyser on the IAM console.
Validating Identity Policies (IAM Console)
- Log in to the new IAM console.
- In the navigation pane, click Identity Policies. In the upper right corner, click Create Identity Policy.
Figure 1 Creating an identity policy

- Select JSON for Policy View.
- (Optional) In the Policy Content area, click Select Existing Policy, select an existing policy (for example, EVSFullAccessPolicy), and click OK.

You can select multiple policies of the same applicable scope (either Global services or Project-level services.) If you need permissions for both global and project-level services, create two policies for more refined access control.
- Modify policy statements.
- Effect: Set it to Allow or Deny.
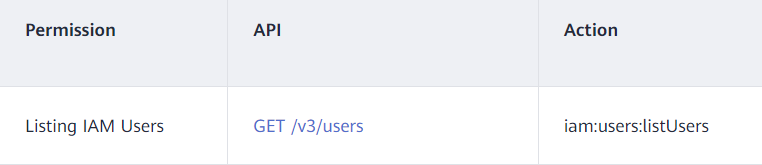
- Action: Enter the actions listed in the API actions table (see Figure 2) of each service.

- The Version is 5.0 and cannot be modified.
- For details about the actions supported by each service in the API reference, see Actions Supported by Identity Policy-based Authorization.
- The access analyzer automatically checks the policy and displays the check findings in the lower part of the Policy Content. You can click a result category to view details.
- Security: Indicates security risks, which may be caused by overly permissive access.
- Errors: Indicate errors that prevent the policy from functioning, such as grammar errors or invalid parameters. If an error occurs, the policy cannot be created.
- Warnings: Indicate errors that prevent the policy from functioning, such as a mismatch between a parameter type and a value. The policy can still be created even if there is a warning.
- Suggestions: Indicate suggestions for the policy to achieve expected results. For example, suggestions are given when there are empty arrays or empty objects.
You are advised to adjust the policy based on the suggestions. Access Analyzer Policy Check Reference provides the solutions.
Figure 3 Viewing policy validation check findings
- (Optional) Enter a brief description for the identity policy.
- Click OK.
- Attach the identity policy to a user group. Users in the group then have the permissions defined in the policy.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot