Connecting to an Elasticsearch Cluster Through Spring Boot
Working directly with Elasticsearch's underlying APIs can increase development complexity, such as additional code maintenance tasks. CSS Elasticsearch clusters support data query and management through Spring Data Elasticsearch (an integrated Elasticsearch component in the Spring Boot ecosystem). This component encapsulates official Elasticsearch Java APIs. Developers can use the Spring repository API or native query DSL to efficiently access clusters without working with underlying APIs. For details about how to use Spring Boot, see Spring Boot.
Prerequisites
- The target Elasticsearch cluster is available.
- The server that runs the Java code can communicate with the Elasticsearch cluster.
- Depending on the network configuration method used, obtain the cluster access address. For details, see Network Configuration.
- Java has been installed on the server and the JDK version is 1.8 or later. Download JDK 1.8 from Java Downloads.
- The Spring Boot version has been confirmed. To ensure better compatibility, use a Java client that has the same version as the target Elasticsearch cluster.
In this document, Spring Boot 2.5.5 is used as an example. The corresponding Spring Data Elasticsearch version is 4.2.x, and the target Elasticsearch cluster version is 7.10.2.
Preparations
- Check that the Spring Boot version you're using meets the compatibility requirements. For details, see the official compatibility list.
In this document, Spring Boot 2.5.5 is used as an example. The corresponding Spring Data Elasticsearch version is 4.2.x, and the target Elasticsearch cluster version is 7.10.2.
- Create a Spring Boot project.
- Declare Java dependencies. Declare the Apache version in Maven mode.
<parent> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-parent</artifactId> <version>2.5.5</version> </parent> <dependencies> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-data-elasticsearch</artifactId> </dependency> <dependency> <groupId>org.elasticsearch.client</groupId> <artifactId>elasticsearch-rest-high-level-client</artifactId> <version>7.10.2</version> </dependency> </dependencies>
Accessing a Cluster
The sample code varies depending on the security mode settings of the target Elasticsearch cluster. Select the right reference document based on your service scenario.
|
Elasticsearch Cluster Security-Mode Settings |
Whether to Load a Security Certificate |
Details |
|---|---|---|
|
Non-security mode Security mode + HTTP |
- |
|
|
Security mode + HTTPS |
No |
Connecting to a Cluster That Uses HTTPS via Spring Boot (Without a Certificate) |
|
Security mode + HTTPS |
Yes |
Connecting to a Cluster That Uses HTTPS via Spring Boot (With a Certificate) |
Connecting to a Cluster That Uses HTTP Through Spring Boot
The following are steps for using Spring Boot to connect to a non-security mode Elasticsearch cluster; or a security-mode Elasticsearch cluster that uses HTTP instead of HTTPS.
- Configure the application.properties file.
1 2 3 4
elasticsearch.url=host1:9200,host2:9200 // You do not need to configure the following two lines for a non-security cluster. elasticsearch.username=username elasticsearch.password=password
Table 2 Configuration parameters Parameter
Description
host
Address for accessing the cluster.
username
Username for accessing the cluster.
password
Password of the user.
- Configure the client code.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45
package com.xxx.configuration; import org.elasticsearch.client.RestHighLevelClient; import org.springframework.beans.factory.annotation.Value; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.ComponentScan; import org.springframework.context.annotation.Configuration; import org.springframework.data.elasticsearch.client.ClientConfiguration; import org.springframework.data.elasticsearch.client.RestClients; import org.springframework.data.elasticsearch.config.AbstractElasticsearchConfiguration; import org.springframework.data.elasticsearch.repository.config.EnableElasticsearchRepositories; @Configuration // com.xxx.repository is the repository directory, which is defined by extends org.springframework.data.elasticsearch.repository.ElasticsearchRepository. @EnableElasticsearchRepositories(basePackages = "com.xxx.repository") // com.xxx indicates the project directory, for example, com.company.project. @ComponentScan(basePackages = "com.xxx") public class Config extends AbstractElasticsearchConfiguration { @Value("${elasticsearch.url}") public String elasticsearchUrl; // There is no need to set the following two parameters for a non-security cluster. @Value("${elasticsearch.username}") public String elasticsearchUsername; @Value("${elasticsearch.password}") public String elasticsearchPassword; @Override @Bean public RestHighLevelClient elasticsearchClient() { final ClientConfiguration clientConfiguration = ClientConfiguration.builder() .connectedTo(StringHostParse(elasticsearchUrl)) // For a non-security cluster, there is no need to configure withBasicAuth. .withBasicAuth(elasticsearchUsername, elasticsearchPassword) .build(); return RestClients.create(clientConfiguration).rest(); } private String[] StringHostParse(String hostAndPorts) { return hostAndPorts.split(","); } }
- If Spring Boot starts properly, the cluster is connected.
Connecting to a Cluster That Uses HTTPS via Spring Boot (Without a Certificate)
The following are steps for using Spring Boot to connect to a security-mode + HTTPS Elasticsearch cluster without loading a security certificate.
- Configure the application.properties file.
1 2 3
elasticsearch.url=host1:9200,host2:9200 elasticsearch.username=username elasticsearch.password=password
Table 3 Configuration parameters Parameter
Description
host
Address for accessing the cluster.
username
Username for accessing the cluster.
password
Password of the user.
- Configure the client code.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73
package com.xxx.configuration; import org.elasticsearch.client.RestHighLevelClient; import org.springframework.beans.factory.annotation.Value; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.ComponentScan; import org.springframework.context.annotation.Configuration; import org.springframework.data.elasticsearch.client.ClientConfiguration; import org.springframework.data.elasticsearch.client.RestClients; import org.springframework.data.elasticsearch.config.AbstractElasticsearchConfiguration; import org.springframework.data.elasticsearch.repository.config.EnableElasticsearchRepositories; import java.security.KeyManagementException; import java.security.NoSuchAlgorithmException; import java.security.SecureRandom; import java.security.cert.CertificateException; import java.security.cert.X509Certificate; import javax.net.ssl.HostnameVerifier; import javax.net.ssl.SSLContext; import javax.net.ssl.SSLSession; import javax.net.ssl.TrustManager; import javax.net.ssl.X509TrustManager; @Configuration // com.xxx.repository is the repository directory, which is defined by extends org.springframework.data.elasticsearch.repository.ElasticsearchRepository. @EnableElasticsearchRepositories(basePackages = "com.xxx.repository") // com.xxx indicates the project directory, for example, com.company.project. @ComponentScan(basePackages = "com.xxx") public class Config extends AbstractElasticsearchConfiguration { @Value("${elasticsearch.url}") public String elasticsearchUrl; @Value("${elasticsearch.username}") public String elasticsearchUsername; @Value("${elasticsearch.password}") public String elasticsearchPassword; @Override @Bean public RestHighLevelClient elasticsearchClient() { SSLContext sc = null; try { sc = SSLContext.getInstance("SSL"); sc.init(null, trustAllCerts, new SecureRandom()); } catch (KeyManagementException | NoSuchAlgorithmException e) { e.printStackTrace(); } final ClientConfiguration clientConfiguration = ClientConfiguration.builder() .connectedTo(StringHostParse(elasticsearchUrl)) .usingSsl(sc, new NullHostNameVerifier()) .withBasicAuth(elasticsearchUsername, elasticsearchPassword) .build(); return RestClients.create(clientConfiguration).rest(); } private String[] StringHostParse(String hostAndPorts) { return hostAndPorts.split(","); } public static TrustManager[] trustAllCerts = new TrustManager[] { new X509TrustManager() { @Override public void checkClientTrusted(X509Certificate[] chain, String authType) throws CertificateException { } @Override public void checkServerTrusted(X509Certificate[] chain, String authType) throws CertificateException { } @Override public X509Certificate[] getAcceptedIssuers() { return null; } } }; public static class NullHostNameVerifier implements HostnameVerifier { @Override public boolean verify(String arg0, SSLSession arg1) { return true; } } }
- If Spring Boot starts properly, the cluster is connected.
Connecting to a Cluster That Uses HTTPS via Spring Boot (With a Certificate)
The following are steps for using Spring Boot to connect to a security-mode + HTTPS Elasticsearch cluster while loading a security certificate.
- Obtaining and Uploading a Security Certificate.
- Configure the application.properties file.
1 2 3
elasticsearch.url=host1:9200,host2:9200 elasticsearch.username=username elasticsearch.password=password
Table 4 Configuration parameters Parameter
Description
host
Address for accessing the cluster.
username
Username for accessing the cluster.
password
Password of the user.
- Configure the client code.
- com.xxx indicates the project directory, for example, com.company.project.
- com.xxx.repository is the repository directory, which is defined by extends org.springframework.data.elasticsearch.repository.ElasticsearchRepository.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99
package com.xxx.configuration; import org.elasticsearch.client.RestHighLevelClient; import org.springframework.beans.factory.annotation.Value; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.ComponentScan; import org.springframework.context.annotation.Configuration; import org.springframework.data.elasticsearch.client.ClientConfiguration; import org.springframework.data.elasticsearch.client.RestClients; import org.springframework.data.elasticsearch.config.AbstractElasticsearchConfiguration; import org.springframework.data.elasticsearch.repository.config.EnableElasticsearchRepositories; import java.io.File; import java.io.FileInputStream; import java.io.InputStream; import java.security.KeyStore; import java.security.SecureRandom; import java.security.cert.CertificateException; import java.security.cert.X509Certificate; import javax.net.ssl.HostnameVerifier; import javax.net.ssl.SSLContext; import javax.net.ssl.SSLSession; import javax.net.ssl.TrustManager; import javax.net.ssl.TrustManagerFactory; import javax.net.ssl.X509TrustManager; @Configuration // com.xxx.repository is the repository directory, which is defined by extends org.springframework.data.elasticsearch.repository.ElasticsearchRepository. @EnableElasticsearchRepositories(basePackages = "com.xxx.repository") // com.xxx indicates the project directory, for example, com.company.project. @ComponentScan(basePackages = "com.xxx") public class Config extends AbstractElasticsearchConfiguration { @Value("${elasticsearch.url}") public String elasticsearchUrl; @Value("${elasticsearch.username}") public String elasticsearchUsername; @Value("${elasticsearch.password}") public String elasticsearchPassword; @Override @Bean public RestHighLevelClient elasticsearchClient() { SSLContext sc = null; try { // certFilePath and certPassword are the path and password of the security certificate. TrustManager[] tm = {new MyX509TrustManager(certFilePath, certPassword)}; sc = SSLContext.getInstance("SSL", "SunJSSE"); sc.init(null, tm, new SecureRandom()); } catch (Exception e) { e.printStackTrace(); } final ClientConfiguration clientConfiguration = ClientConfiguration.builder() .connectedTo(StringHostParse(elasticsearchUrl)) .usingSsl(sc, new NullHostNameVerifier()) .withBasicAuth(elasticsearchUsername, elasticsearchPassword) .build(); return RestClients.create(clientConfiguration).rest(); } private String[] StringHostParse(String hostAndPorts) { return hostAndPorts.split(","); } public static class MyX509TrustManager implements X509TrustManager { X509TrustManager sunJSSEX509TrustManager; MyX509TrustManager(String certFilePath, String certPassword) throws Exception { File file = new File(certFilePath); if (!file.isFile()) { throw new Exception("Wrong Certification Path"); } System.out.println("Loading KeyStore " + file + "..."); InputStream in = new FileInputStream(file); KeyStore ks = KeyStore.getInstance("JKS"); ks.load(in, certPassword.toCharArray()); TrustManagerFactory tmf = TrustManagerFactory.getInstance("SunX509", "SunJSSE"); tmf.init(ks); TrustManager[] tms = tmf.getTrustManagers(); for (TrustManager tm : tms) { if (tm instanceof X509TrustManager) { sunJSSEX509TrustManager = (X509TrustManager) tm; return; } } throw new Exception("Couldn't initialize"); } @Override public void checkClientTrusted(X509Certificate[] chain, String authType) throws CertificateException { } @Override public void checkServerTrusted(X509Certificate[] chain, String authType) throws CertificateException { } @Override public X509Certificate[] getAcceptedIssuers() { return new X509Certificate[0]; } } public static class NullHostNameVerifier implements HostnameVerifier { @Override public boolean verify(String arg0, SSLSession arg1) { return true; } } }
- If Spring Boot starts properly, the cluster is connected.
Obtaining and Uploading a Security Certificate
To access a security-mode Elasticsearch cluster that uses HTTPS, perform the following steps to obtain the security certificate if it is required, and upload it to the client.
- Obtain the security certificate CloudSearchService.cer.
- Log in to the CSS management console.
- In the navigation pane on the left, choose Clusters > Elasticsearch.
- In the cluster list, click the name of the target cluster. The cluster information page is displayed.
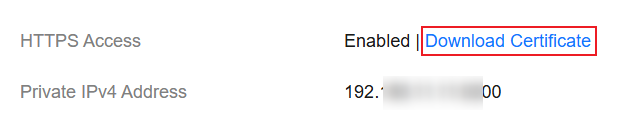
- Click the Overview tab. In the Network Information area, click Download Certificate below HTTPS Access.
Figure 1 Downloading a security certificate
- Convert the security certificate CloudSearchService.cer. Upload the downloaded security certificate to the client and use keytool to convert the .cer certificate into a .jks certificate that can be read by Java.
- In Linux, run the following command to convert the certificate:
keytool -import -alias newname -keystore ./truststore.jks -file ./CloudSearchService.cer - In Windows, run the following command to convert the certificate:
keytool -import -alias newname -keystore .\truststore.jks -file .\CloudSearchService.cer
In the preceding command, newname indicates the user-defined certificate name.
After this command is executed, you will be prompted to set the certificate password and confirm the password. Securely store the password. It will be used for accessing the cluster.
- In Linux, run the following command to convert the certificate:
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





